
In alarming news from February 2024, ConnectWise, a prevalent provider of remote desktop software, disclosed severe security flaws within their ScreenConnect product. These flaws pose an immediate danger, with active exploitation already observed.
The Vulnerabilities
- CVE-2024-1708 (CVSS Score 8.4): A path-traversal vulnerability enabling attackers to execute malicious code or steal sensitive data. Any ScreenConnect version before 23.9.7 is at risk.
- CVE-2024-1709 (CVSS Score 10): An authentication bypass that offers attackers unhindered backdoor entry to critical systems and information. Again, versions before 23.9.7 are impacted.
Critical Concern
CVE-2024-1709 stands out as particularly dangerous. It’s alarmingly easy to exploit, and proof-of-concept (PoC) attacks already exist online.

Security researchers at Unit 42 warn that both cybercriminals and state-backed groups will likely seize upon this flaw. ConnectWise itself has verified compromised accounts tied to these vulnerabilities.
The Global Threat
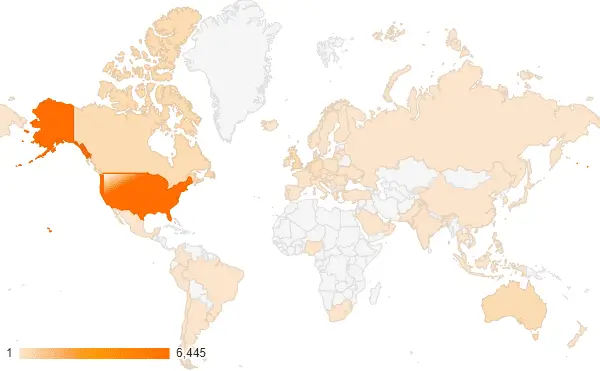
Unit 42 researchers have pinpointed over 18,000 unique IP addresses running ScreenConnect worldwide as of February 21st, 2024. The heavy concentration of these systems in the US (almost 75%) creates a massive target zone.
What Should You Do?
-
Immediate Action For Self-Hosted Deployments: If you operate a self-hosted or on-premises ScreenConnect solution, upgrade to version 23.9.10.8817 without delay.
-
Cloud Users – Breathe Easier: Customers utilizing ConnectWise’s cloud hosting (screenconnect[.]com or hostedrmm[.]com) are already protected. No further action is required.
Why the Urgency?
Past breaches suggest that once vulnerabilities like these are public, attacks escalate swiftly. Hackers won’t hesitate to:
- Deploy Ransomware: Disabling vital systems and extorting businesses for hefty payments.
- Data Theft: Exfiltrating valuable customer information, trade secrets, or anything else that can be weaponized or sold.
- Establish Footholds: These vulnerabilities can provide a launchpad for lateral movement within your network, compromising even more systems.
Beyond Patching: Vigilance Matters
Updating is your immediate safeguard. However, remain alert in the coming weeks. Monitor your network logs for unusual activity from ScreenConnect hosts and be aware of the latest threat intelligence reports.