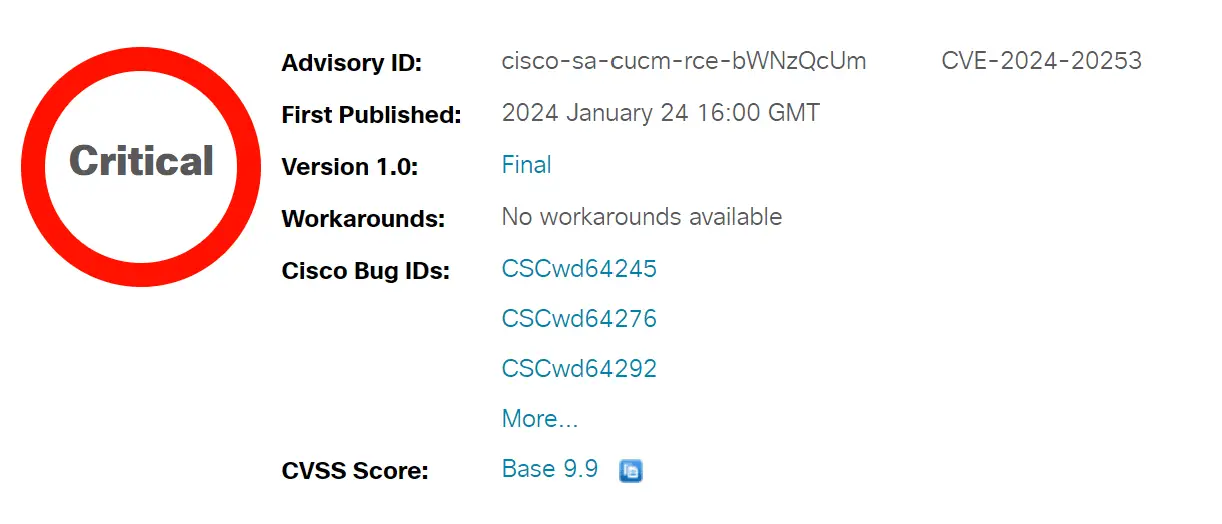
Cisco has patched a critical Unified Communications and Contact Center Solutions security flaw that can let unauthenticated, remote attackers execute arbitrary code on an affected device. This security flaw officially tracked as CVE-2024-20253, has a high severity rating of 9.9 on the CVSS.
At the heart of CVE-2024-20253 lies a perilous gap in security: the improper handling of user-provided data as it is ingested into memory. This flaw opens the door for unauthenticated, remote attackers to craft and dispatch malicious messages to a listening port on vulnerable devices.

The potential for damage escalates with the realization that successful exploitation could pave the way for attackers to gain root access. Such a scenario is the stuff of nightmares for security professionals, as it would offer cybercriminals the keys to the kingdom, allowing them to manipulate or compromise systems and data at their whim.
“A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system with the privileges of the web services user. With access to the underlying operating system, the attacker could also establish root access on the affected device,” Cisco explains.
This vulnerability affects the following Cisco products in the default configuration:
- Packaged Contact Center Enterprise (PCCE) (CSCwe18830)
- Unified Communications Manager (Unified CM) (CSCwd64245)
- Unified Communications Manager IM & Presence Service (Unified CM IM&P) (CSCwd64276)
- Unified Communications Manager Session Management Edition (Unified CM SME) (CSCwd64245)
- Unified Contact Center Enterprise (UCCE) (CSCwe18830)
- Unified Contact Center Express (UCCX) (CSCwe18773)
- Unity Connection (CSCwd64292)
- Virtualized Voice Browser (VVB) (CSCwe18840)
In the face of this daunting vulnerability, Cisco’s Product Security Incident Response Team (PSIRT) has been quick to act, issuing patches to fortify the defenses of its Unified Communications and Contact Center Solutions.
Notably, Cisco has reported that, thus far, there is no evidence to suggest that CVE-2024-20253 has been exploited in the wild. This absence of active exploitation or public proof-of-concept exploits offers a silver lining, providing organizations with a crucial window to apply the necessary patches and secure their systems against potential attacks.