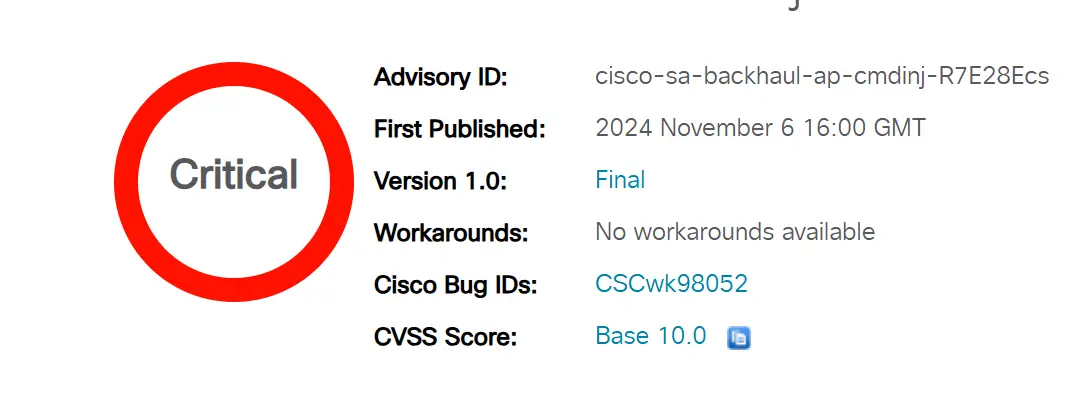
In a critical security advisory, Cisco has disclosed a command injection vulnerability in its Unified Industrial Wireless Software used for Cisco Ultra-Reliable Wireless Backhaul (URWB) Access Points. Identified as CVE-2024-20418, this vulnerability carries a maximum Common Vulnerability Scoring System (CVSS) score of 10.0, highlighting the potential impact on affected systems.
CVE-2024-20418 is a flaw within the web-based management interface of Cisco’s URWB software, which allows an unauthenticated, remote attacker to inject and execute arbitrary commands with root privileges. According to Cisco, this severe vulnerability arises from “improper validation of input to the web-based management interface.” By sending specially crafted HTTP requests, a potential attacker could gain unauthorized root access, leading to complete control over the device’s operating system.
This vulnerability affects specific Cisco Catalyst Access Points if they run a vulnerable release with the URWB operating mode enabled. The affected devices include:
- Catalyst IW9165D Heavy Duty Access Points
- Catalyst IW9165E Rugged Access Points and Wireless Clients
- Catalyst IW9167E Heavy Duty Access Points
Devices not operating in URWB mode are safe from this vulnerability. Cisco advises administrators to check if the URWB mode is enabled by using the show mpls-config CLI command. If this command is available, it confirms that the device is in URWB mode and may be vulnerable.
Cisco’s Product Security Incident Response Team (PSIRT) has not received any reports of active exploitation. “The Cisco PSIRT is not aware of any public announcements or malicious use of the vulnerability that is described in this advisory,” the advisory stated. However, given the critical nature of this flaw, organizations are urged to prioritize patching.
There are no workarounds available to address this vulnerability, making prompt action essential. Cisco has released updates to its software, advising users of version 17.14 and earlier to migrate to a fixed release. For users running 17.15, upgrading to 17.15.1 is recommended to mitigate the vulnerability.
Related Posts:
- CVE-2023-20252: Cisco Catalyst SD-WAN Manager Unauthorized Access Vulnerability
- Cisco releases patch to fix three high security bugs
- Hackers use Cisco Router flaws to attack Iran, 3,500 routers hacked
- Cisco Smart Install Protocol was misused, tens of thousands of critical infrastructure may be attacked
- Cisco releases the security updates to fix flaws in multiple Cisco products