CVE-2024-21633 Let Attacker Gain Remote Code Execution in Mobile Security Framework (MobSF)

The discovery of a subtle yet potent vulnerability can send ripples across the industry. Recently, a security researcher @cybaqkebm identified a critical flaw in the Mobile Security Framework (MobSF), a widely used platform for mobile application security analysis.
The vulnerability, identified as CVE-2024-21633, exists in the apktool, a component of the MobSF. This tool, used for reverse engineering Android applications, inadvertently allowed arbitrary file writing. The flaw, rated with a CVSS score of 7.8, could enable an attacker to place files at a desired location within the system running Apktool, provided they had the necessary permissions.
The exploitation process involved a series of calculated steps. By manipulating the output path of resource files, an attacker could write files to a relative path within the “${decode target path}/res/” directory. The challenge was to execute these non-executable files. The researcher, however, found a creative solution: targeting MobSF’s use of jadx, another tool in the framework that converts DEX files to Java. By overwriting the jadx binary with a malicious payload and waiting for MobSF to execute it, the attacker could gain unauthorized access.
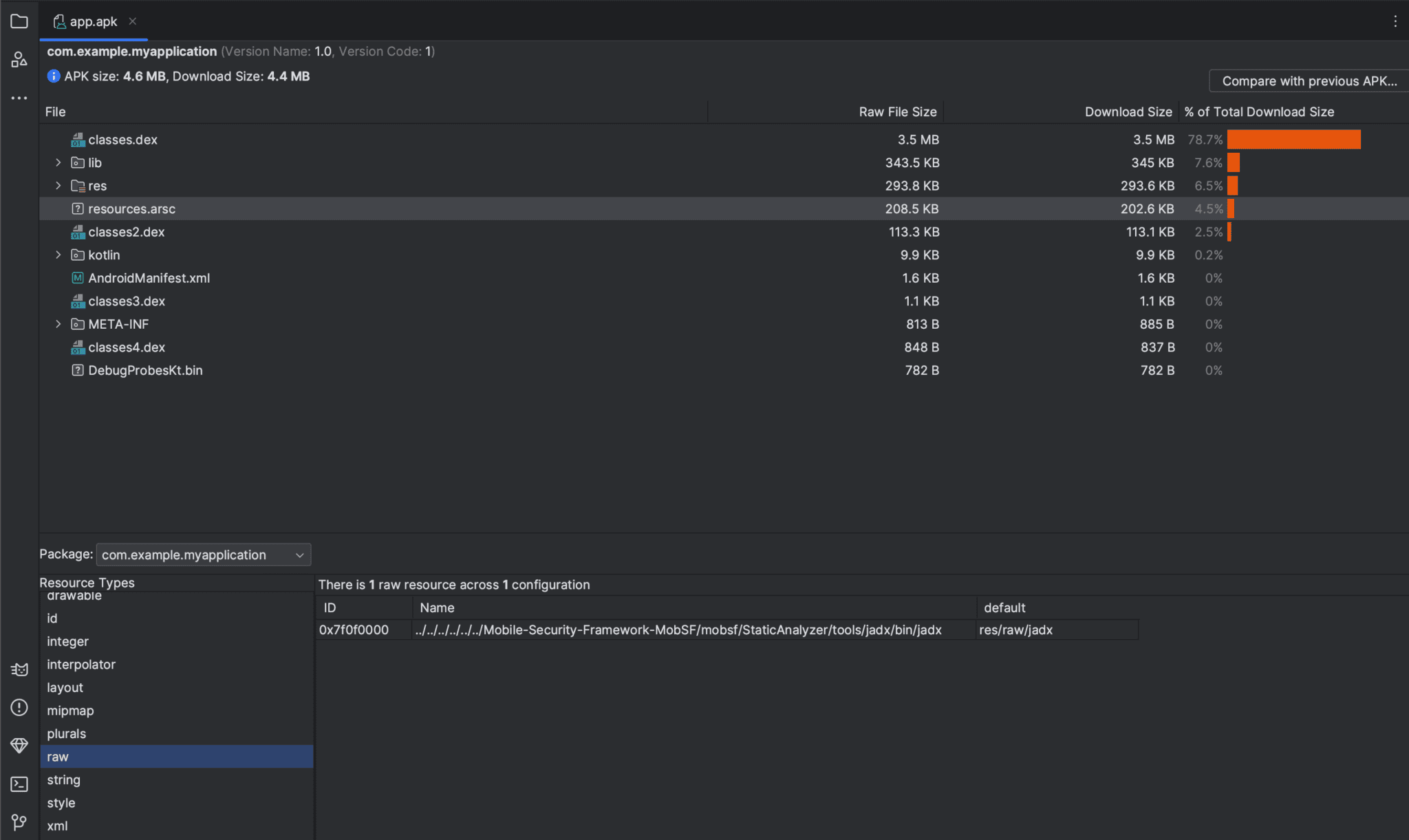
Two primary ideas guided the exploitation strategy: overwriting shell initialization files (like .bashrc or .zshrc) or creating a cron job. The former required knowing the user’s directory or username, while the latter demanded root privileges. The ingenious aspect was exploiting MobSF’s behavior of changing jadx’s permissions to executable, thus setting the stage for executing the malicious file.

Upon discovery, the vulnerability was promptly reported to the MobSF team, who quickly rectified it by updating the apktool version. However, concerns remain about the framework’s practice of making files executable and running them subsequently. This incident highlights the need for more stringent security measures, especially in tools that handle potentially vulnerable code.





