Security researcher Mykola Grymalyuk published the technical details and a proof-of-concept (PoC) exploit code for a vulnerability (CVE-2024-34331) in Parallels Desktop for Mac, a popular virtualization software. The flaw could allow attackers to escalate privileges and gain root access on affected Intel-based Macs.
The vulnerability stems from how Parallels Desktop interacts with Apple’s createinstallmedia tool, which is used to create bootable macOS installers. By exploiting a lack of signature verification in this process, attackers could inject malicious code and execute it with root privileges.
The attack involves creating a specially crafted macOS installer that contains a malicious payload. When this installer is opened by Parallels Desktop, the vulnerability allows the payload to run with elevated privileges, giving the attacker full control over the system.
The vulnerability affects Parallels Desktop versions 16.0.0 through 19.3.0 on x86_64-based machines. Apple Silicon Macs are not impacted due to the use of Apple’s Virtualization.framework stack, which does not invoke createinstallmedia.
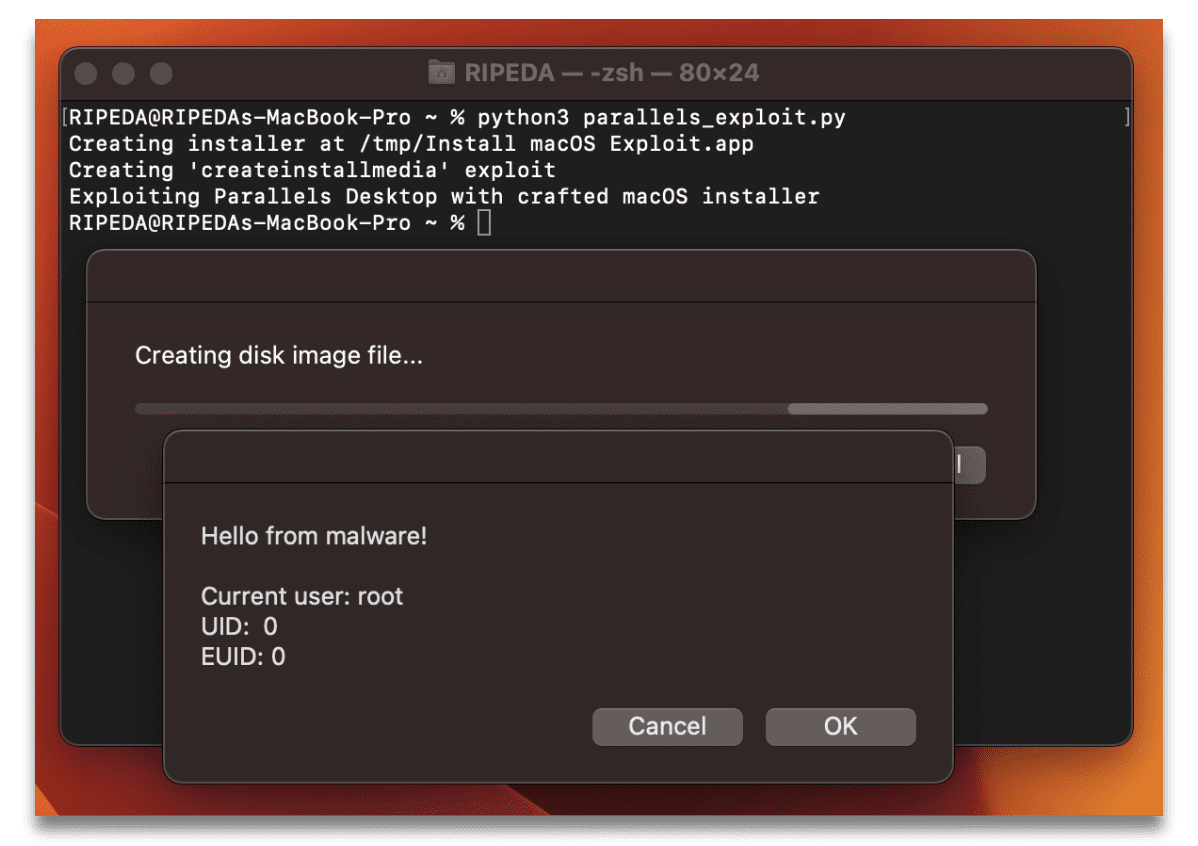
Grymalyuk’s proof of concept (PoC) demonstrates how an attacker can exploit the CVE-2024-34331 vulnerability to achieve local privilege escalation. The process involves creating a malicious macOS Installer app with a payload in createinstallmedia and having Parallels Desktop execute it, thereby gaining root access.
Steps to Exploit:
- Create a macOS Installer app with a malicious payload under Contents/Resources/createinstallmedia.
- Open the application in Parallels Desktop and prepare it for installation.
- prl_client_app takes the malicious macOS Installer app.
- prl_client_app runs Parallels Service.
- Parallels Service runs with SUID, raising privileges to root.
- Parallels Service executes repack_osx_install_app.sh.
- repack_osx_install_app.sh runs createinstallmedia as root.
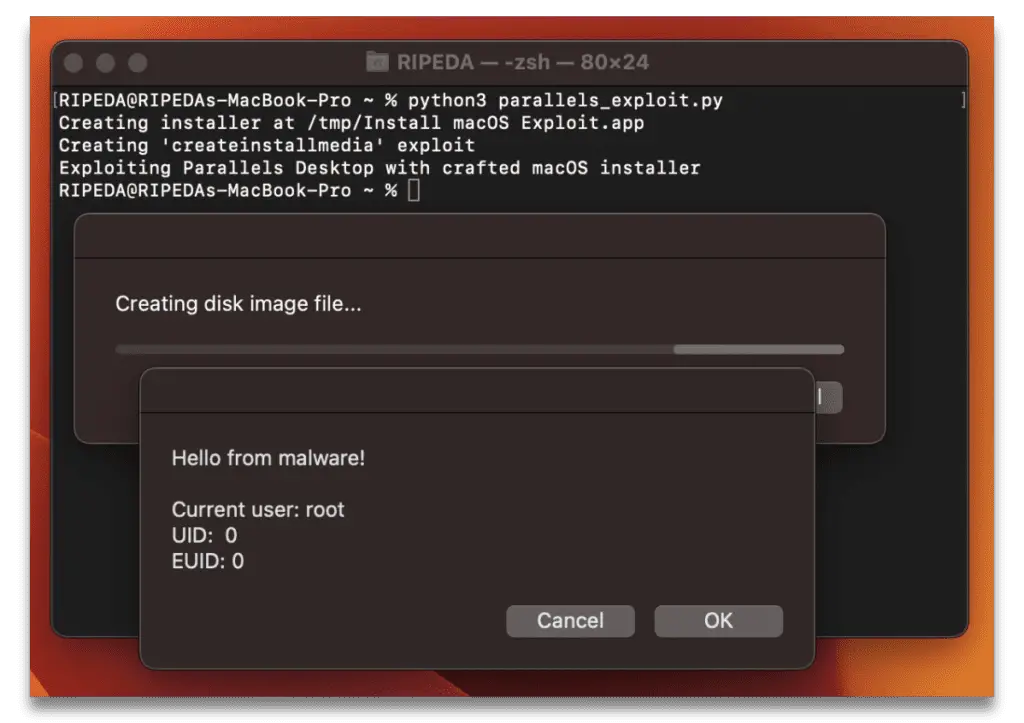
This process, automated through a script (parallels_exploit.py), effectively demonstrates the vulnerability by showcasing root privilege escalation.
Parallels has addressed the issue in version 19.3.1, urging all users to update their software immediately.