CVE-2024-35204: Veritas System Recovery Vulnerability Puts Data at Risk
A recent security advisory from Veritas has unveiled a high-severity vulnerability in their Veritas System Recovery software. Designated as CVE-2024-35204, this vulnerability has been assigned a CVSS score of 8.4, indicating its high severity. The flaw, found in Veritas System Recovery versions 23.0 (23.0.2.63015) and earlier, allows low-privilege Windows system users to create files in arbitrary locations within the filesystem, including protected directories.
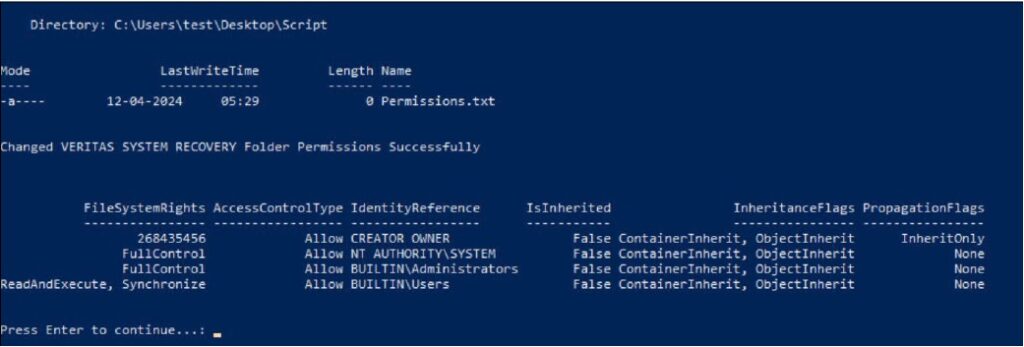
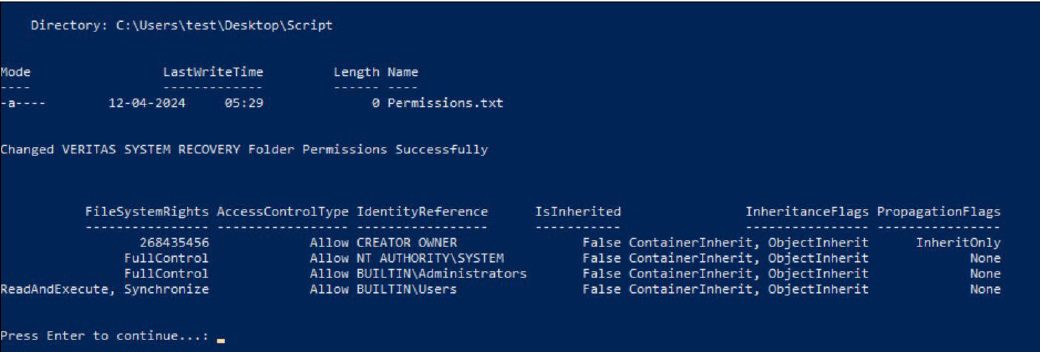
Displays permissions for the Veritas System Recovery folder
The identified vulnerability in Veritas System Recovery permits an attacker with minimal privileges to create files in critical system directories such as C:\Windows, C:\Windows\System32, and C:\Program Files. This capability could be exploited to cause a denial of service or tamper with essential services, such as backup services, potentially leading to significant system disruptions or data loss.
The vulnerability hinges on the way the Veritas System Recovery service logs information. Specifically, the service logs data into the C:\ProgramData\Veritas\VERITAS SYSTEM RECOVERY\LOGS\Veritas System Recovery.log.txt file with NT Authority\System permissions. However, this log file is not exclusively opened or protected, allowing it to be deleted and manipulated by low-privilege users. The directory containing the log file is modifiable by such users, enabling them to transform it into a directory junction or symbolic link.
Multiple versions of Veritas System Recovery are impacted, including:
- Versions 23.2, 23.1, 23.0, 22.0, 21.3, 21.2, 21.1, 21.0
- Earlier, unsupported versions may also be at risk
Veritas has released a hotfix (Hotfix 860045) to address the CVE-2024-35204 vulnerability. All customers running Veritas System Recovery are strongly urged to download and apply the hotfix as soon as possible.





