
Recently, security researcher Sergey Kornienko from PixiePoint Security published an analysis and proof-of-concept (PoC) exploit for a critical zero-day vulnerability in the Windows Kernel, identified as CVE-2024-38106. This elevation of privilege (EoP) vulnerability has already been exploited in the wild, prompting urgent action from both security professionals and end users.
CVE-2024-38106 (CVSS 7.0) resides in the core of the Windows operating system, specifically within the ntoskrnl.exe process, also known as the Windows NT Operating System Kernel Executable. This kernel is a fundamental component of Windows, acting as the bridge between hardware and software, and is critical for the efficient functioning of numerous Windows services.
The vulnerability stems from a race condition, a scenario where the outcome depends on the sequence or timing of uncontrollable events. In this case, an attacker who successfully exploits the race condition could elevate their privileges to the SYSTEM level, effectively gaining full control over the targeted machine.
Kornienko’s meticulous analysis of the patch revealed significant changes to two key functions: VslGetSetSecureContext() and NtSetInformationWorkerFactory(). These modifications were critical in addressing the underlying race condition:
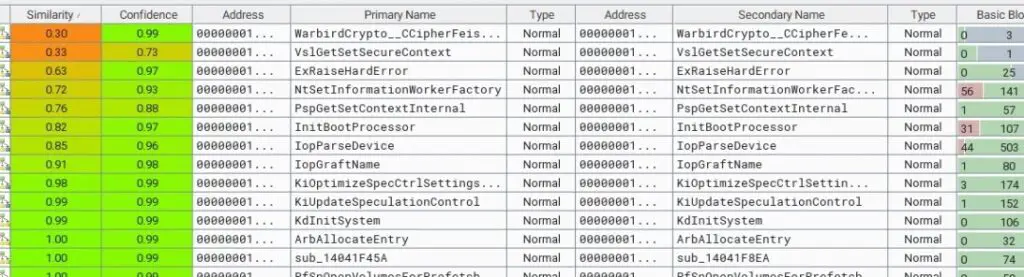
- VslGetSetSecureContext(): The patch introduced proper locking mechanisms for the VslpEnterIumSecureMode() operation, which is tied to the Virtualization-Based Security (VBS) secure kernel. This enhancement prevents the race condition by ensuring that the operation is executed in a controlled and secure manner.
- NtSetInformationWorkerFactory(): The changes here were more complex, involving the addition of a flag check that interacts with the NtShutdownWorkerFactory() process. This check ensures that the race condition between object construction and destruction is mitigated, reducing the risk of exploitation.
Kornienko shared a proof-of-concept (PoC) exploit demonstrating how an attacker could leverage the CVE-2024-38106 vulnerability to escalate privileges, further illustrating the potential impact of the flaw if left unpatched.
The zero-day vulnerability was actively exploited by a North Korean threat actor known as Citrine Sleet. The group used the vulnerability as part of a sophisticated exploit chain that began with targets being directed to a malicious domain controlled by the attackers—voyagorclub[.]space. While the exact method of luring victims to this domain remains unconfirmed, social engineering tactics are suspected.
Once a target accessed the domain, a zero-day remote code execution (RCE) exploit for CVE-2024-7971 was deployed, compromising the sandboxed Chromium renderer process. This initial breach allowed the attackers to download and execute shellcode, which included a Windows sandbox escape exploit targeting CVE-2024-38106. The exploit enabled the attackers to bypass the sandbox and elevate their privileges, allowing the deployment of the FudModule rootkit.
The FudModule rootkit is particularly insidious, employing Direct Kernel Object Manipulation (DKOM) techniques to tamper with kernel security mechanisms, all while executing from user mode. It leverages a kernel read/write primitive to manipulate the system at its most fundamental level, making detection and removal exceptionally difficult.
Microsoft was quick to respond, issuing a patch for CVE-2024-38106 as part of its August 2024 Patch Tuesday release. However, the vulnerability had already been exploited in the wild before the patch was made available, underscoring the need for rapid patch deployment and vigilance against threats.
Related Posts:
- CISA & Microsoft Warn of 6 Actively Exploited Zero-Day Vulnerabilities
- CVE-2024-7971: North Korean APT Citrine Sleet Exploits Chromium Zero-Day
- Urgent Chrome Update: Active Zero-Day Exploit Detected (CVE-2024-7971)
- Mozilla releases emergency update to fix two exploited zero-day vulnerabilities in Firefox
- New DarkGate Malware Campaign Exploits 0-day CVE-2024-21412 Flaw
- Apple backports fix for actively exploited 0-day to older macOS and iPhone/iPad devices