
Popular FTP server ProFTPD has been found to contain a critical security flaw that could allow attackers to gain root access to vulnerable systems. The vulnerability, tracked as CVE-2024-48651 (CVSS 7.5), exists in the mod_sql component of ProFTPD versions 1.3.8b and earlier.
This flaw arises from the improper handling of supplemental groups, which are additional group memberships assigned to a user. In affected versions, users inherit the supplemental group with GID 0 (root) if they don’t have any explicitly assigned supplemental groups. This unintended inheritance grants them unauthorized root privileges, potentially leading to complete system compromise.
The issue was initially reported by users in the Debian bug tracker and subsequently discussed in the ProFTPD Github repository. Developers have addressed the vulnerability with a source code patch, urging users to update their installations immediately.
Widespread Impact
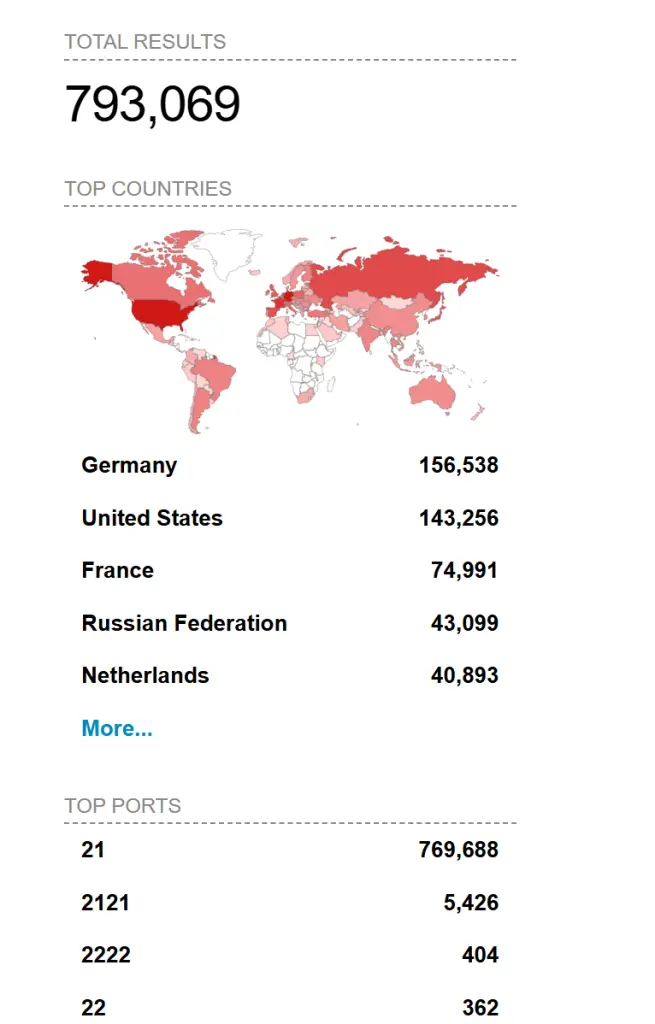
While FTP usage has declined with the rise of more secure protocols, ProFTPD remains widely deployed. Shodan scans reveal nearly 800,000 servers running ProFTPD globally, with the highest concentrations in Germany, the USA, and France. The exact number of vulnerable instances remains unclear, but the potential for widespread exploitation is significant.
Mitigation
IT administrators running ProFTPD servers are strongly advised to take the following steps:
- Update: Check for updated packages from your distribution provider that include the security patch.
- Recompile: If an updated package is not available, recompile the server from the latest source code in the ProFTPD Github repository.
- Monitor: Closely monitor system logs for any suspicious activity.
Organizations should prioritize migrating to more secure alternatives like SFTP or FTPS whenever possible.
Related Posts:
- CVE-2023-51713: A DoS Flaw Affects ProFTPD
- Let’s Encrypt Root gains the trust of all major root programs