
A zero-day vulnerability in Google Chrome (CVE-2024-5274) has been publicly disclosed, along with technical details and a proof-of-concept (PoC) exploit, potentially escalating the risk for users worldwide. This flaw, known as a ‘type confusion’ vulnerability in Chrome’s JavaScript engine, allows attackers to execute malicious code, opening the door for a range of cyber attacks.
CVE-2024-5274, a bug within Chrome’s V8 JavaScript engine, enables a type confusion vulnerability. This occurs when the program misinterprets one type of data for another, leading to potential crashes, data corruption, or even arbitrary code execution by attackers.
The disclosure of CVE-2024-5274 was initially accompanied by a patch from Google in May 2024. However, technical details about the flaw were withheld to prevent potential exploitation. This changed when researchers @mistymntncop and @buptsb published the PoC exploit code and accompanying technical analysis on GitHub.
The availability of the PoC presents a double-edged sword. On one hand, it serves as a valuable resource for security researchers and practitioners, who can study the vulnerability in depth to develop better defensive measures. On the other hand, it provides threat actors with a blueprint for crafting exploits, transforming theoretical vulnerabilities into active threats.
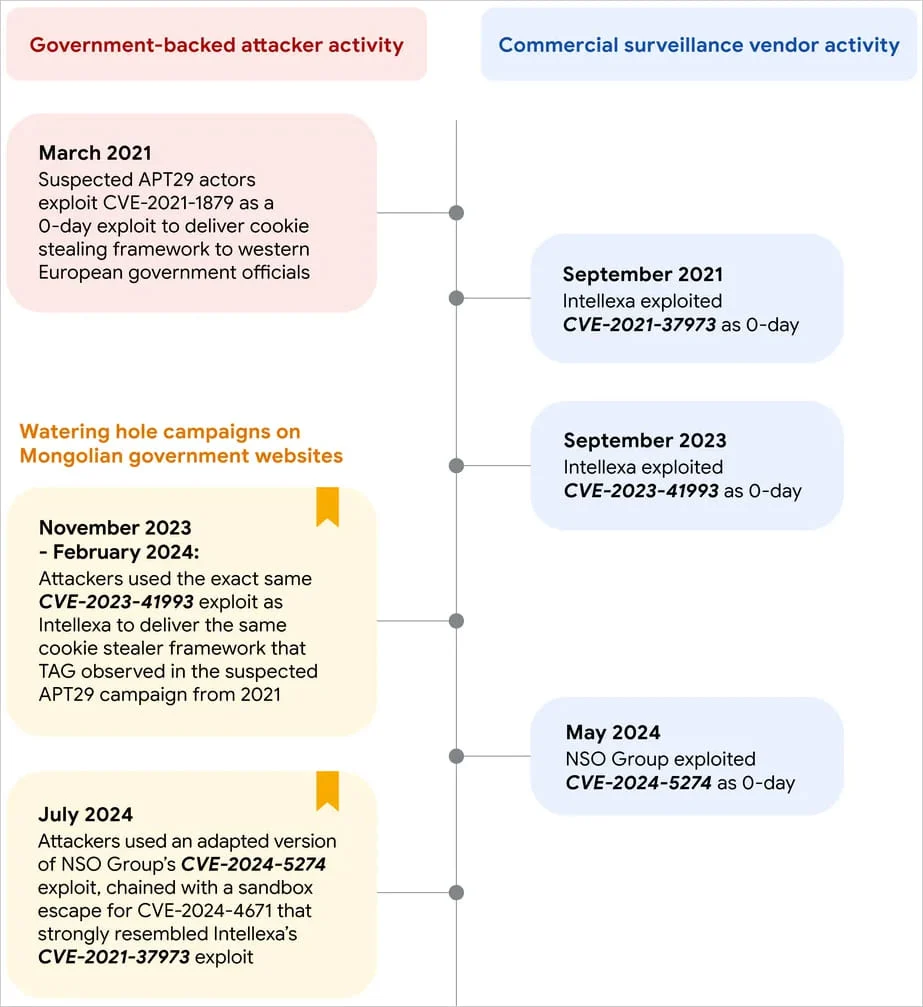
Google has now disclosed that the Russian state-sponsored APT29 hacking group has been actively exploiting CVE-2024-5274. The group, known for its sophisticated cyber-espionage campaigns, leveraged this vulnerability in July 2024 to target Android users visiting the compromised website ‘mga.gov[.]mn’. This attack was part of a broader campaign that also exploited CVE-2024-4671, another critical flaw in Google Chrome.
Interestingly, the exploit for CVE-2024-5274 used by APT29 appears to be a modified version of an exploit initially developed by the NSO Group for a zero-day attack in May 2024. The CVE-2024-4671 exploit, on the other hand, bore striking similarities to those previously employed by Intellexa, further highlighting the evolving tactics of advanced persistent threats (APTs).
Google has addressed this vulnerability in Chrome’s Stable channel with version 125.0.6422.112/.113 for Windows and Mac, and version 125.0.6422.112 for Linux. It is crucial to update your browser immediately to protect yourself from potential attacks.
Related Posts:
- CISA Warns: Actively Exploited Chrome Zero-Day Joins ‘Must-Patch’ List
- CVE-2024-5274: Google Patches Zero-Day Vulnerability Actively Exploited in the Wild