Image: Ebrahim Shafiei
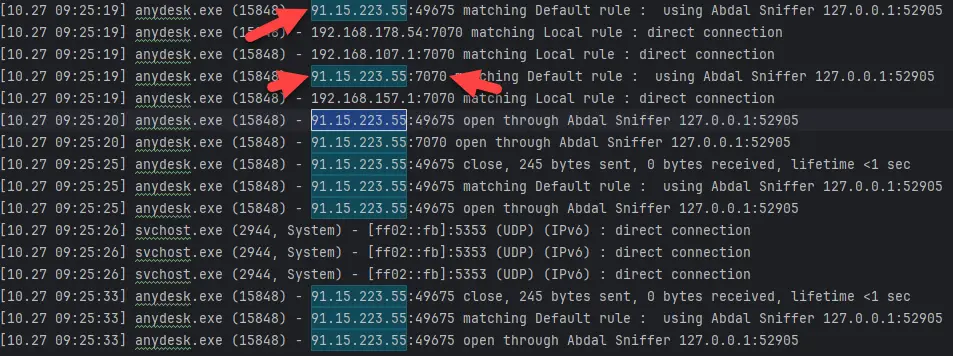
A newly discovered vulnerability in popular remote desktop software AnyDesk could allow attackers to uncover users’ IP addresses, posing significant privacy risks. Security researcher Ebrahim Shafiei identified the flaw (CVE-2024-52940) in AnyDesk’s “Allow Direct Connections” feature on Windows systems.
The vulnerability affects AnyDesk versions 8.1.0 and below. When “Allow Direct Connections” is enabled and the connection port is set to 7070 on the attacker’s system, it allows them to retrieve the public IP address of a target using only their AnyDesk ID. Worryingly, this requires no configuration changes on the victim’s system.
“This vulnerability in AnyDesk’s ‘Allow Direct Connections’ feature exposes sensitive IP information of the target,” Shafiei explains. “Attackers can exploit this flaw to retrieve the public IP address, and, in specific cases, the private IP address of the target system.”
The implications of this vulnerability are significant, especially in scenarios where remote access tools are not adequately protected. Leaked IP addresses can be used for further attacks, including targeted phishing campaigns, denial-of-service attacks, or even to pinpoint a user’s physical location.
Shafiei has published proof-of-concept exploit code for this vulnerability on Github, highlighting the urgency of the situation. He emphasizes the need for an update or patch from AnyDesk’s development team to fully address the issue.
Currently, no official fix is available from AnyDesk. Users are advised to exercise caution when using the “Allow Direct Connections” feature and consider disabling it until a patch is released.
Related Posts:
- AnyDesk’s Cybersecurity Breach: Unveiling the Recent Attack
- AnyDesk Breach 2024: Dark Web Sale of 18,317 Credentials
- Beware of Fake Downloads: AsyncRAT Spreads via Popular Software Cracks
- Patch Now! Ladon, AnyDesk, and More Lurk in Unpatched ActiveMQ Servers
- Mad Liberator Ransomware Group Exploits Anydesk to Steal Data in Stealthy Attacks