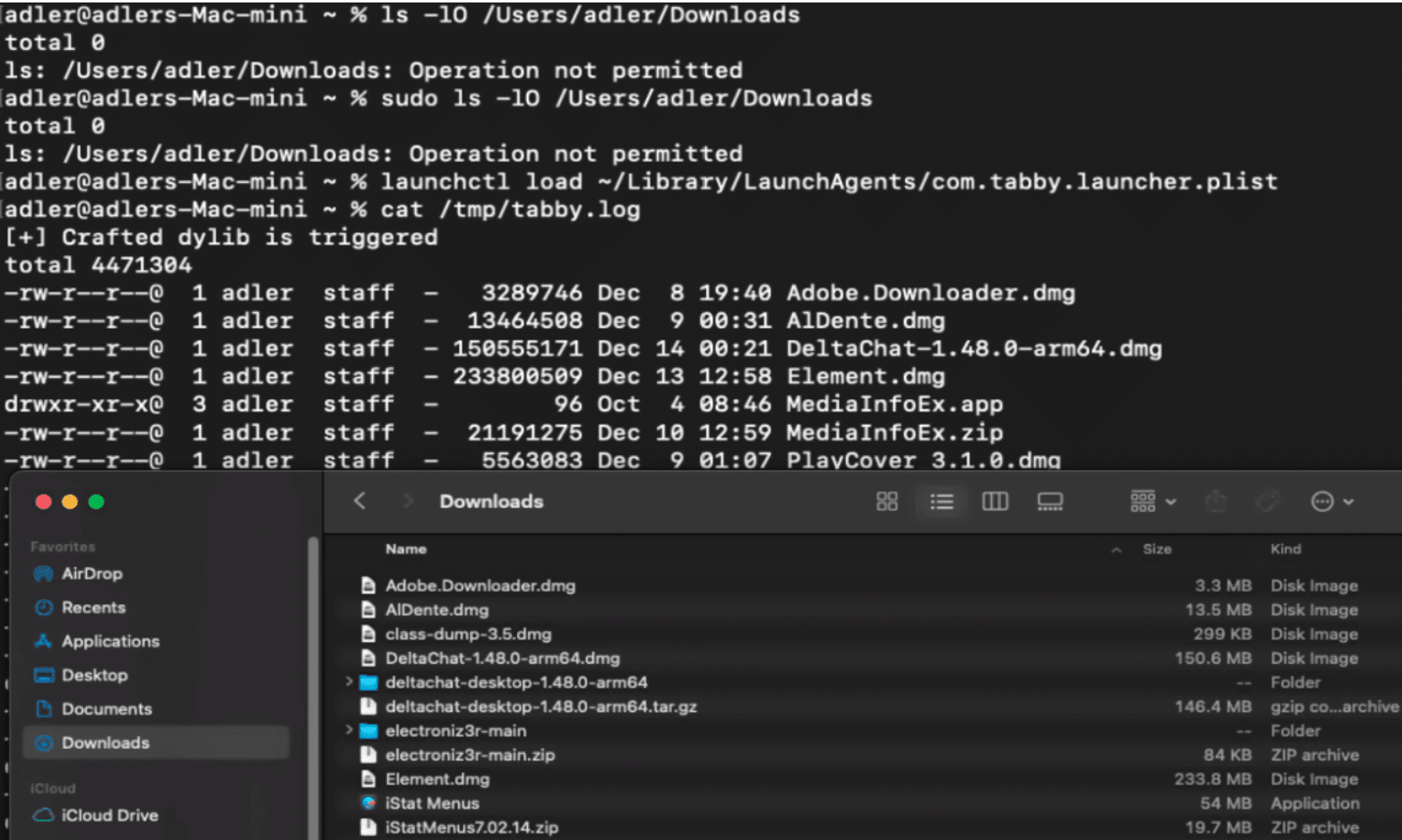
A high-severity vulnerability, CVE-2024-55950 (CVSS 8.6), has been identified in Tabby (formerly Terminus), a widely used terminal emulator and SSH client for Windows, macOS, and Linux. With nearly 61,000 GitHub stars and over 15 million downloads, Tabby’s extensive user base is at potential risk due to overly permissive entitlements and unnecessary access permissions.
Tabby’s macOS application is flagged for including excessive permissions, including access to camera, microphone, and personal folders via Apple Events. These permissions, combined with dangerous entitlements like:
- com.apple.security.cs.allow-dyld-environment-variables
- com.apple.security.cs.disable-library-validation,
introduce significant security risks. According to the advisory, “These entitlements are not required for Tabby’s operation since Tabby’s plugin system is NodeJS-based and doesn’t require external native libraries.” Similar terminal emulators, such as iTerm2 and Waveterm, function without these entitlements, further questioning their necessity.
The excessive permissions enable multiple attack vectors, including:
- TCC Bypass
Attackers can leverage DYLD_INSERT_LIBRARY injection or dylib hijacking to inject malicious code. Once injected, this code inherits Tabby’s extensive permissions, granting unauthorized access to:- Camera and microphone for potential surveillance
- Personal directories like Downloads and Documents
- System-level access without user consent
- Privacy Implications
Unauthorized surveillance and data extraction are major risks, with potential for silent monitoring via hardware access. - Security Compromise
Injected malicious code could bypass macOS security controls, execute unauthorized actions, and compromise sensitive user information.
The advisory warns, “Considering Tabby’s huge user base, and extensive TCC permissions it holds, consequences are particularly concerning.”
The CVE-2024-55950 vulnerability affects Tabby versions prior to 1.0.216, and users are strongly advised to update to the patched version (1.0.216) immediately.
To mitigate the risk, the advisory recommends:
- Reviewing and removing at least one of the unnecessary entitlements, such as com.apple.security.cs.allow-dyld-environment-variables.
- Ensuring configurations align with the minimum required permissions for full functionality.
Security researcher Winslow, credited for discovering this flaw, has also released a proof-of-concept exploit, demonstrating the vulnerability’s real-world implications.
Tabby is not the first high-profile application to face such vulnerabilities. Similar TCC bypass flaws have been documented, including:
- CVE-2020-24259: Signal TCC bypass
- CVE-2023-26818: Telegram TCC bypass
The advisory underscores that, “Tabby’s situation warrants additional attention as terminal emulators often require elevated privileges, successful TCC bypass poses higher risk.”
Developers are also reminded to evaluate and limit unnecessary permissions to minimize attack surfaces in their applications.
For macOS users relying on Tabby, upgrading to the latest version is not just recommended—it’s essential.
Related Posts:
- Researcher Details CVE-2024-44131 – A Critical TCC Bypass in macOS and iOS
- HM Surf (CVE-2024-44133): macOS Flaw Exposing Cameras and Microphones to Hackers, PoC Published
- Microsoft discovers powerdir vulnerability in macOS
- Mozilla wants Facebook to make app private to protect user privacy by default