Image: Rhino Security Labs
Rhino Security Labs recently detailed a series of critical vulnerabilities affecting default installations of the Appsmith product. The most severe of these is CVE-2024-55963, which allows unauthenticated remote code execution due to a misconfigured PostgreSQL database included by default.
Appsmith is an open-source developer tool designed to help organizations build internal applications, such as dashboards, admin panels, and customer support tools. Users can develop User Interface (UI) elements and connect various data sources to the User Interface such as databases and Large Language Models (LLMs).
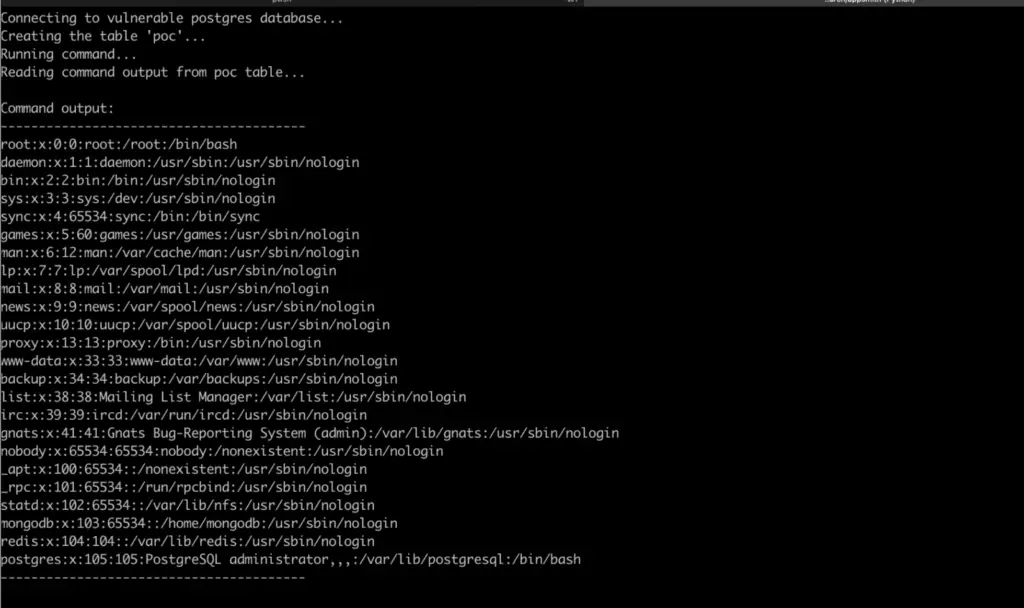
The report highlights that Appsmith provides the ability to connect a variety of datasources to create applications. One of these practice datasources is a PostgreSQL database running locally on the Appsmith server. The vulnerability lies in the PostgreSQL authentication configuration file, “pg_hba.conf,” which contains an entry that allows any local user to connect as any PostgreSQL user without providing a password.
As the report states, “This configuration allows any local user to connect as any PostgreSQL user (including superuser) without providing a password because the trust authentication method explicitly bypasses authentication.”
This misconfiguration, combined with Appsmith’s default configuration that allows user signup, makes it possible for an attacker to sign up, create an application, and connect to the misconfigured database. From there, they can execute SQL queries that allow for system command execution.
In addition to the unauthenticated RCE, Rhino Security Labs identified two additional vulnerabilities:
- CVE-2024-55964: An Insecure Direct Object Reference (IDOR) vulnerability that allows an “App Viewer” user to access Database SQL.
- CVE-2024-55965: A Denial of Service vulnerability via Broken Access Control, allowing “App Viewer” access to the ‘Restart’ API request.
Rhino Security Labs provides in-depth coverage of each issue, including technical analyses, proof-of-concept exploits, and detection techniques.
The good news is that Appsmith has addressed these vulnerabilities in recent releases. Users running self-hosted Appsmith instances should upgrade to v1.52 or later to ensure full protection against these three vulnerabilities.