CVE-2024-5910: Critical Vulnerability Threatens Palo Alto Networks’ Expedition
Palo Alto Networks, a leading cybersecurity firm, has released a critical security advisory detailing multiple vulnerabilities across its product lines, including PAN-OS, Cortex XDR, and Expedition. These flaws range in severity and impact, but all pose a significant risk to organizations relying on Palo Alto’s solutions.
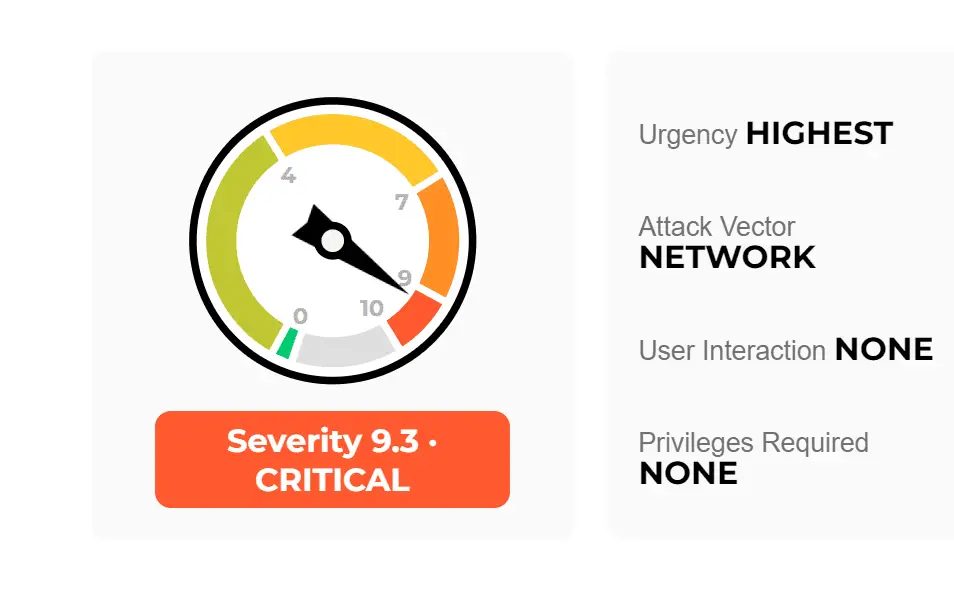
CVE-2024-5910: Missing Authentication in Expedition (CVSS 9.3)

The most severe vulnerability, CVE-2024-5910, affects the Expedition configuration management tool and could allow an attacker with network access to take over admin accounts, potentially exposing sensitive configuration data and credentials. Palo Alto Networks urges all Expedition users to update to version 1.2.92 or later immediately.
PAN-OS Vulnerabilities:
PAN-OS, the operating system powering Palo Alto firewalls, is also affected by multiple vulnerabilities [1,2,3]. CVE-2024-5911, an arbitrary file upload flaw, could allow attackers to disrupt Panorama systems, potentially causing service outages. Another vulnerability, CVE-2024-5913, enables privilege escalation if an attacker can tamper with the physical file system. Additionally, CVE-2024-3596, a man-in-the-middle vulnerability, could allow attackers to bypass authentication and gain superuser privileges when using RADIUS authentication with CHAP or PAP.
Cortex XDR Agent Flaw:
The Cortex XDR agent, responsible for endpoint protection, is also affected by CVE-2024-5912, a flaw in file signature verification. This could allow attackers to bypass executable blocking and run untrusted software on compromised devices.
Mitigation and Remediation:
Palo Alto Networks strongly recommends that all affected users apply the available patches and updates as soon as possible. Specific workarounds and mitigations are also detailed in the security advisory, including restricting network access to Expedition and following best practices for securing administrative access to PAN-OS.




