
Ivanti has issued a security advisory addressing a critical vulnerability (CVE-2024-7593) in its Virtual Traffic Manager (vTM), a software-based Layer 7 application delivery controller (ADC). The flaw, which has been assigned a CVSS score of 9.8, enables remote unauthenticated attackers to bypass authentication and create an administrator user, potentially leading to complete system compromise.
The vulnerability stems from an incorrect implementation of the authentication algorithm within Ivanti vTM versions prior to 22.2R1 and 22.7R2. The CVE-2024-7593 flaw specifically affects the admin panel, allowing attackers to gain unauthorized access without valid credentials. The critical nature of this vulnerability highlights the need for immediate attention from organizations using the affected versions of vTM.
The following versions of Ivanti Virtual Traffic Manager are impacted:
- 22.2: Fixed in 22.2R1 (available)
- 22.3: Fixed in 22.3R3 (available week of August 19th)
- 22.3R2: Fixed in 22.3R3 (available week of August 19th)
- 22.5R1: Fixed in 22.5R2 (available week of August 19th)
- 22.6R1: Fixed in 22.6R2 (available week of August 19th)
- 22.7R1: Fixed in 22.7R2 (available)
Ivanti has confirmed that there have been no known exploits in the wild as of the advisory’s release. However, with a Proof of Concept (PoC) publicly available, the risk of exploitation remains high.
Ivanti strongly advises all customers using the affected versions to upgrade to the latest patched releases immediately. The patches for versions 22.2R1 and 22.7R2 are already available, while other versions will have patches released in the week of August 19th.
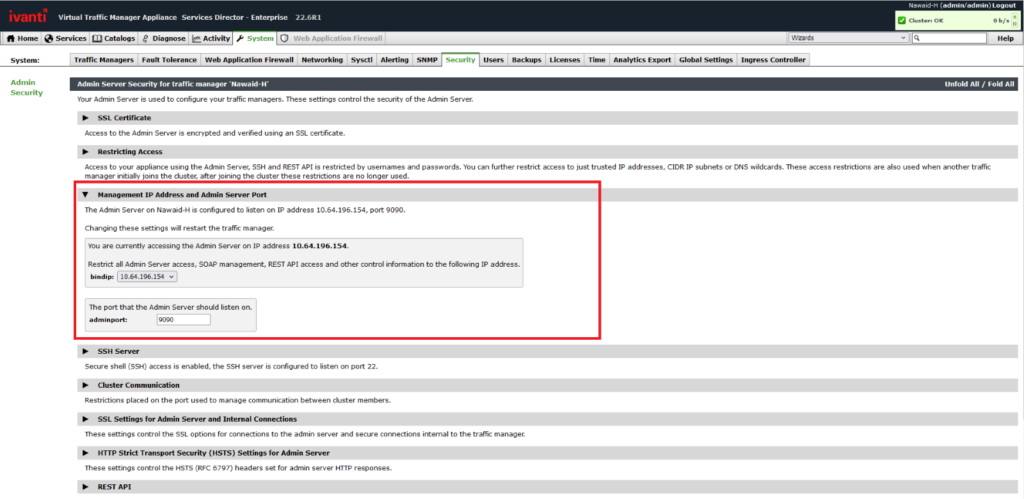
For those unable to upgrade immediately, Ivanti recommends limiting access to the management interface as a temporary mitigation measure.
- On the VTM server navigate to System > Security then click the drop down for the Management IP Address and Admin Server Port section of the page
- In the bindip drop down select the Management Interface IP Address. As another option, customers can also utilize the setting directly above the “bindip” setting to restrict access to trusted IP addresses, further restricting who can access the interface.
Related Posts:
- Critical Vulnerabilities Discovered in Ivanti Connect Secure and Policy Secure
- Akamai Unveils New VPN Post-Exploitation Techniques: Major Vulnerabilities Discovered in Ivanti and FortiGate VPNs