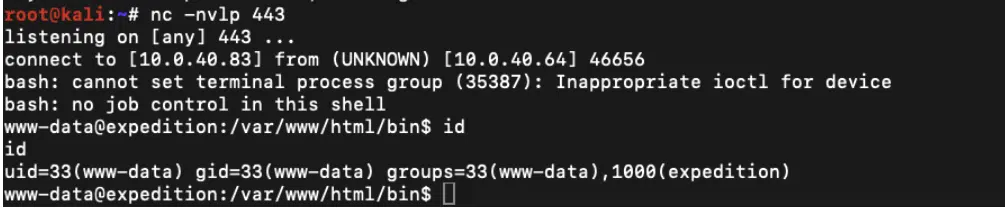
www-data reverse shell | Image: Horizon3.ai
A recent analysis by security researcher Zach Hanley of Horizon3.ai has uncovered a critical vulnerability, CVE-2024-9466, in Palo Alto Networks’ Expedition tool. This vulnerability, with a CVSS score of 8.2, could allow authenticated attackers to gain access to sensitive credentials, including firewall usernames, passwords, and API keys, due to the cleartext storage of this information.
Expedition is a tool designed to streamline the migration of firewall configurations from other vendors to Palo Alto Networks’ systems, making it a widely adopted solution. However, as detailed by Hanley, the flaw could be exploited by attackers with network access, allowing them to reveal critical data. “Once you have access to the server as the www-data user from the above vulnerability, pilfering credentials out of the database is straight forward,” Hanley noted in his detailed analysis.
The vulnerability arises from improper handling of credentials during the migration process, where sensitive information is stored in cleartext. Hanley discovered that attackers could access a log file located at /home/userSpace/devices/debug.txt, which stores raw request logs from the Expedition server. These logs include cleartext credentials used in API key exchanges during device integration, providing attackers with a wealth of sensitive data.
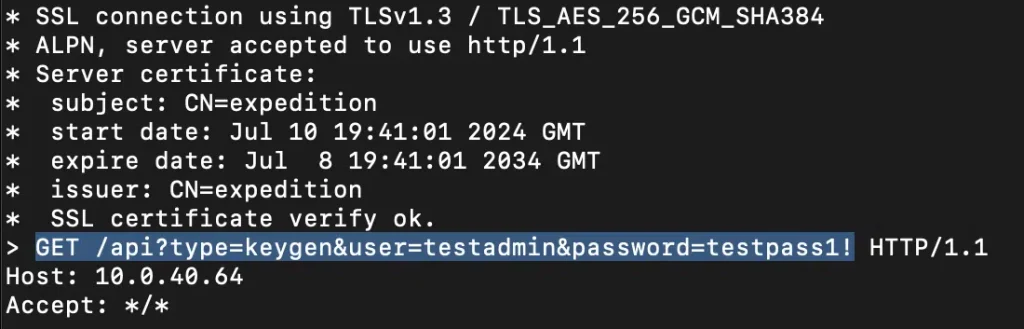
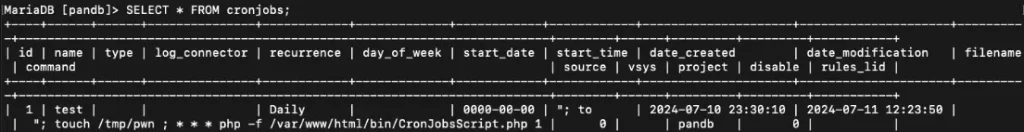
Hanley demonstrated a proof-of-concept attack that involves leveraging a vulnerable cronjob execution process within the Expedition web interface. By injecting malicious commands through the cronjob feature, attackers can execute arbitrary code on the server, escalating their privileges and accessing sensitive files and databases.
To mitigate this risk, Palo Alto Networks has released patches and recommends that users of affected versions of Expedition update their software. The vulnerability affects Expedition versions prior to 1.2.96, and users are advised to apply the fix immediately to avoid potential exploitation.
Related Posts:
- Palo Alto Networks Issues Fix for Critical Vulnerabilities, Including CVE-2024-9463 (CVSS 9.9)
- CVE-2024-5910: Critical Vulnerability Threatens Palo Alto Networks’ Expedition
- PoC Exploit Releases for Exploited Vulnerability CVE-2024-8190 in Ivanti Cloud Services Appliance
- Critical SolarWinds Flaw Exposes 827 Instances: PoC Exploit Unveiled for CVE-2024-28987