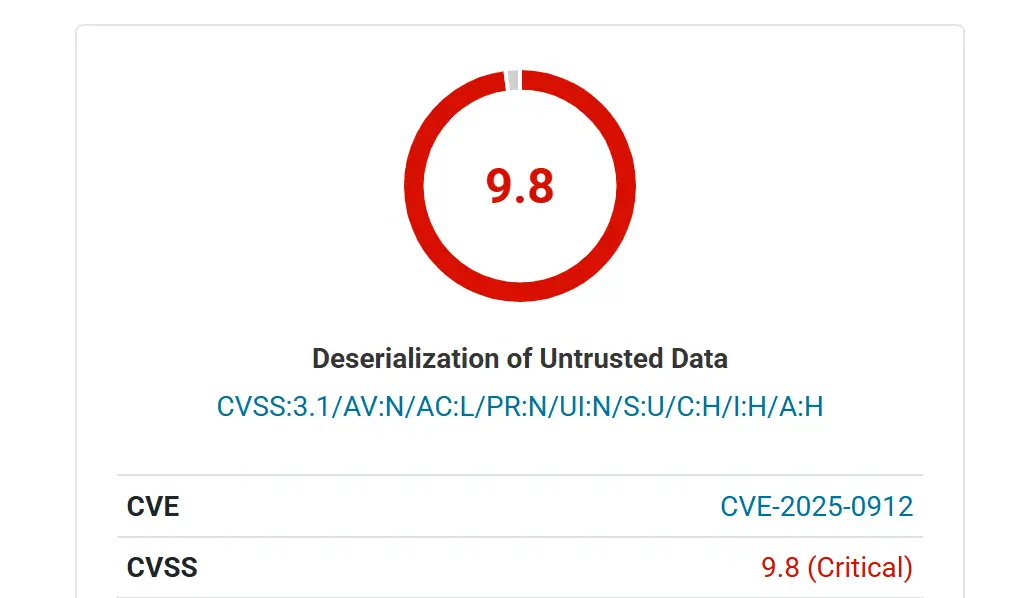
A severe security vulnerability has been discovered in GiveWP, the popular WordPress donation plugin, putting over 100,000 websites at significant risk. The vulnerability, tracked as CVE-2025-0912, carries a critical CVSS score of 9.8, indicating the highest level of severity.
GiveWP, known for its user-friendly interface and robust donation management features, is a staple for non-profits, charities, and individuals seeking to raise funds online. However, a flaw within the plugin’s Donations Widget has exposed a critical weakness.
The root of the problem lies in the plugin’s handling of the ‘card_address‘ parameter within the donation form. Specifically, versions up to and including 3.19.4 are vulnerable to PHP Object Injection. This occurs due to the deserialization of untrusted input, allowing an unauthenticated attacker to inject malicious PHP objects.
In simple terms, an attacker can manipulate the data sent to the website during a donation attempt. This manipulation allows them to introduce code that the server interprets and executes. Without authentication, anyone can exploit this flaw.
What makes this vulnerability particularly dangerous is the presence of a “POP chain.” This technical term refers to a sequence of PHP functions that, when triggered, can lead to remote code execution (RCE). RCE enables an attacker to execute arbitrary commands on the server hosting the affected website.
The developers of GiveWP have released version 3.20.0, which addresses this critical vulnerability. Website administrators are strongly advised to update their plugin to this version immediately.
Related Posts:
- CVE-2025-22777 (CVSS 9.8): Critical Security Alert for GiveWP Plugin with 100,000 Active Installations
- CVE-2024-8353 (CVSS 10): Critical GiveWP Flaw, 100k WordPress Sites at Risk
- CVE-2024-9634 (CVSS 9.8): Critical GiveWP Flaw Exposes 100,000+ WordPress Sites to RCE
- Pineapple Fund donated 27 Bitcoin to KDE worth $200,000
- CVE-2024-5932 (CVSS 10): Critical RCE Vulnerability Impacts 100k+ WordPress Sites