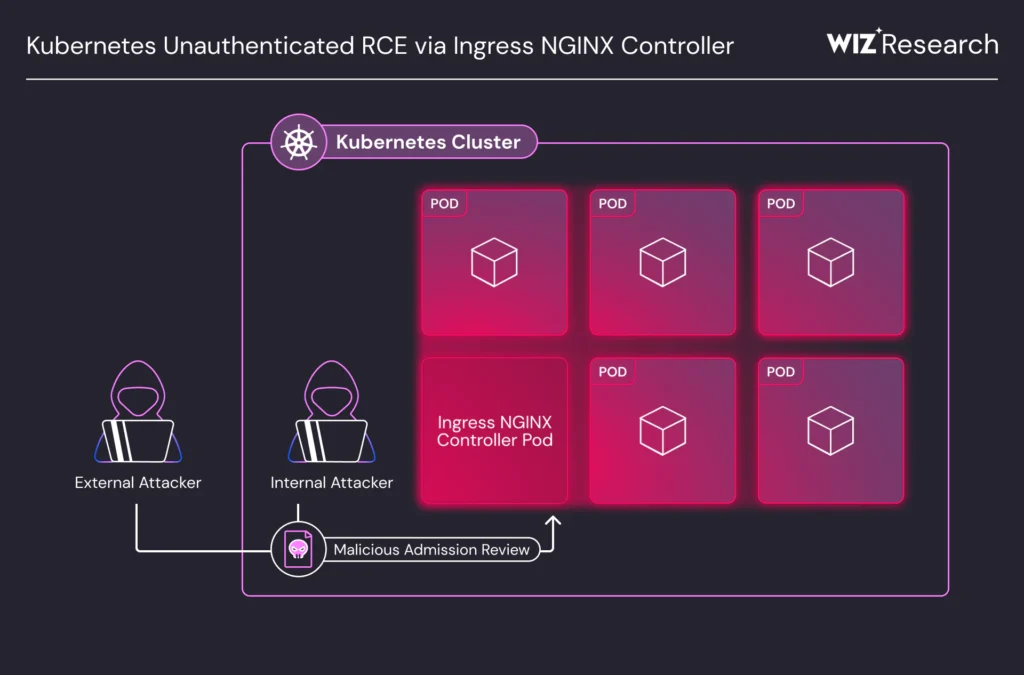
IngressNightmare attack vectors | Image: Wiz Research
A new cybersecurity threat has been identified by Wiz Research, dubbed “IngressNightmare,” which exposes critical vulnerabilities in the Ingress NGINX Controller for Kubernetes. Assigned CVEs CVE-2025-1097, CVE-2025-1098, CVE-2025-24514, and CVE-2025-1974, this quartet of critical unauthenticated Remote Code Execution (RCE) flaws strikes at the heart of Kubernetes ingress infrastructure, enabling attackers to potentially seize control of entire clusters.
“Exploitation of these vulnerabilities leads to unauthorized access to all secrets stored across all namespaces in the Kubernetes cluster by attackers, which can result in cluster takeover,” warns Wiz Research.
⚠️ Why This Matters
Ingress NGINX is the most widely deployed ingress controller in Kubernetes environments. Designed to route external traffic to internal services via NGINX as a reverse proxy, it’s a cornerstone of modern Kubernetes networking.
However, its admission controller—intended to validate ingress configurations—is the unexpected Achilles’ heel. By default, this controller is exposed to internal network traffic and lacks authentication. The vulnerabilities exploit this trusted but exposed position to enable code injection and execution.
“Our team found a vulnerability… that allows injecting an arbitrary NGINX configuration remotely, by sending a malicious ingress object directly to the admission controller through the network,” the researchers explain.
The flaws have been rated CVSS 9.8, and Wiz’s scans revealed over 6,500 internet-exposed clusters, including infrastructure from Fortune 500 companies, are vulnerable.
🔍 The Exploit Chain: From Config Injection to RCE
The vulnerability chain hinges on how Ingress NGINX constructs and tests configurations using the nginx -t command. When validating configuration files, unsanitized user input can inject arbitrary NGINX directives that, when parsed, lead to remote code execution.
Key flaws include:
- CVE-2025-24514 (CVSS 8.8) – Malicious
auth-urlannotation enables configuration injection. - CVE-2025-1097 (CVSS 8.8) – Exploits
auth-tls-match-cnto sneak in regex-based config manipulation. - CVE-2025-1098 (CVSS 8.8) – Manipulates the ingress object UID for payload injection.
- CVE-2025-1974 (CVSS 9.8)– Leverages the undocumented
ssl_enginedirective to load shared libraries from the filesystem and execute arbitrary code.
“We found that the
ssl_enginedirective, part of the OpenSSL module, can also load shared libraries. This behavior is undocumented.”
To plant their malicious library, the researchers used a clever trick involving NGINX client body buffers. By sending oversized HTTP requests, the payload gets stored temporarily as a file—even after deletion, a file descriptor remains active and accessible via /proc.
With just a few educated guesses for PID and FD numbers, attackers can feed this path into the ssl_engine directive. Once NGINX parses the injected directive, the shared library is executed—fully compromising the pod.
🔎 Who’s Affected?
If you’re running Ingress NGINX and haven’t upgraded to versions 1.12.1 or 1.11.5, you may be at risk. According to Wiz:
“Over 41% of internet-facing clusters are running Ingress-NGINX… and about 43% of cloud environments are vulnerable.”
The vulnerability particularly affects configurations where the validating admission webhook is exposed—often unintentionally via misconfigured networking or Helm charts.
🛡️ How to Defend
Wiz offers several mitigation and detection strategies:
✅ Immediate Actions
- Update to Ingress NGINX Controller v1.12.1 or v1.11.5.
- Restrict access to the admission webhook using network policies.
- Disable the admission controller temporarily, if upgrades aren’t immediately possible.
🔍 Detection
- Use this command to check for active Ingress NGINX pods: kubectl get pods –all-namespaces –selector app.kubernetes.io/name=ingress-nginx
- Use Wiz’s pre-built query in the Wiz Threat Center or run the Wiz Dynamic Scanner.
- Consider the Nuclei template to scan for exposed admission controllers.
Related Posts:
- Australia Bans Kaspersky Products from Government Systems, Citing “Unacceptable Security Risk”
- The Trio of Unpatched Flaws in NGINX Ingress Controller for Kubernetes
- NGINX Open Source Makes the Jump to GitHub, Boosting Collaboration and Community Engagement
- New Phishing Campaign Targets AWS Accounts: Security Experts Warn