File Upload Vulnerability HTTP request | Image: Dor Attias
Security researcher Dor Attias has discovered a critical vulnerability in Flowise, a popular open-source platform used for building AI agents. This vulnerability, tracked as CVE-2025-26319 and assigned a CVSS score of 9.8, could allow unauthenticated attackers to upload arbitrary files to Flowise servers, potentially leading to remote code execution and complete server compromise.
Flowise, known for its user-friendly no-code/low-code interface, has gained significant traction with over 35,000 stars on GitHub and more than a million Docker pulls. Its users range from small and medium-sized businesses (SMBs) to large enterprises, making this vulnerability a widespread concern.
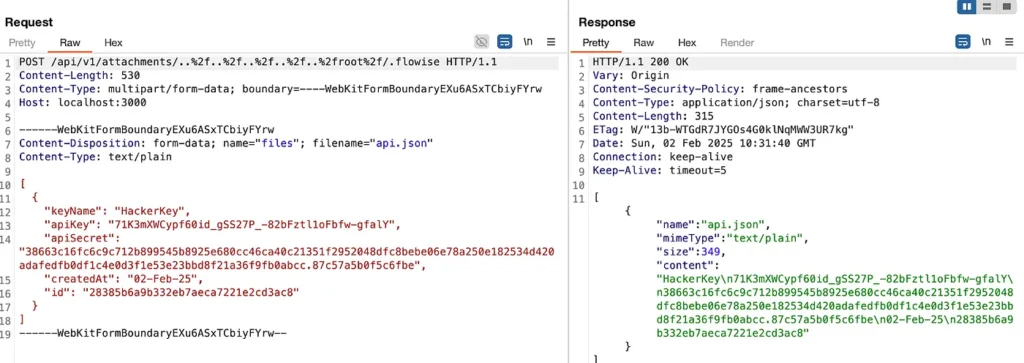
The vulnerability stems from a flaw in Flowise’s knowledge upload feature, which allows users to upload files such as images for AI agents to process. Attackers can exploit this feature to upload malicious files, including scripts, configuration files, and even SSH keys, potentially granting them full control over the server.
Attias explains that the vulnerability lies in the /api/v1/attachments route, which handles attachment uploads. The route’s API endpoint lacks proper validation of user-supplied parameters, allowing attackers to manipulate these parameters and bypass security checks.
By crafting a malicious request, attackers can perform path traversal and overwrite critical files on the server. This could enable them to modify API keys, execute arbitrary code, and gain unauthorized access to sensitive data.
Attias responsibly disclosed the vulnerability to the Flowise team, but they have not yet responded or released a patch. As a result, Attias has published a detailed report outlining the vulnerability and providing a patch for users to mitigate the risk.
Users of Flowise are strongly encouraged to apply the patch or change their storage type to S3 to protect their systems from this critical vulnerability.