Cyber Alert: Bumblebee Malware Targets US Organizations
Bumblebee, a malware favored by cybercriminals, disappeared for a few months but is now back in action. After a four-month hiatus, Proofpoint researchers have detected the sophisticated downloader’s return. Security experts spotted a recent attack targeting organizations in the US.
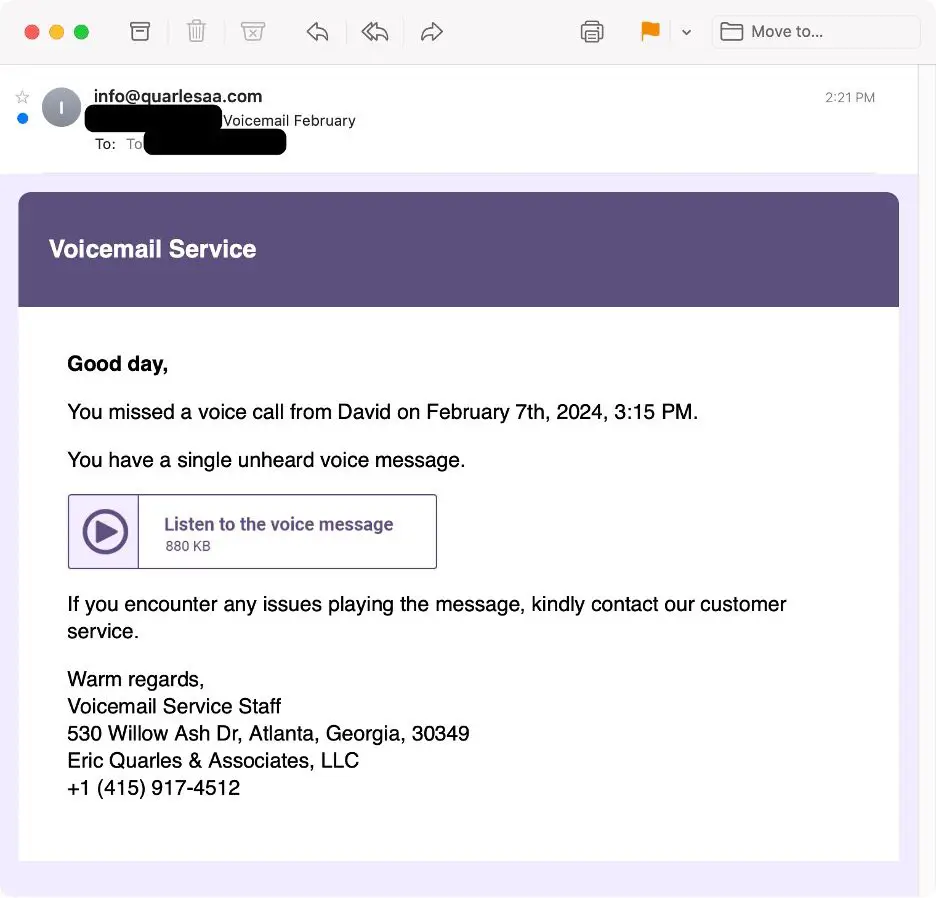
Bumblebee malware, known for its complexity and versatility, was initially a favored payload by cybercriminals from its inception in March 2022 until its disappearance in October 2023. Its comeback was heralded by a meticulously crafted email campaign targeting organizations in the United States. The emails, intriguingly titled “Voicemail February” and originating from a seemingly innocuous sender address, contained OneDrive URLs leading recipients to a malicious Word document. This document masquerades under the guise of consumer electronics brand Humane.

Screenshot of the voicemail-themed email lure
The document employed macros to unleash a script in the Windows temporary directory, a technique that leverages the document’s custom properties to execute a PowerShell command. This command, in turn, paves the way for the Bumblebee DLL to burrow into the system, setting the stage for further exploitation. The use of VBA macro-enabled documents in this campaign is particularly noteworthy, given that such tactics had seen a decline following Microsoft’s move to block macros by default in 2022. This shift forced threat actors to innovate, moving away from macros towards more elaborate exploitation methods. However, the Bumblebee campaign’s reliance on macros underscores a strategic pivot, possibly aiming to exploit specific vulnerabilities or to test the waters for broader deployment strategies.
What sets this campaign apart is the significant deviation from Bumblebee’s previous distribution methods. Previous campaigns saw the malware being delivered through a variety of means, from direct DLL downloads to exploiting vulnerabilities with HTML smuggling and password-protected VBS attachments.
While the current campaign’s actors remain unattributed, their methods bear a resemblance to those associated with previous TA579 activities. Furthermore, Bumblebee’s return coincides with a noticeable uptick in cybercriminal activity, marking the start of 2024 as a period of heightened vigilance for cybersecurity professionals. The reappearance of other threat actors and malware variants further complicates the landscape, challenging organizations to stay ahead of the curve.





