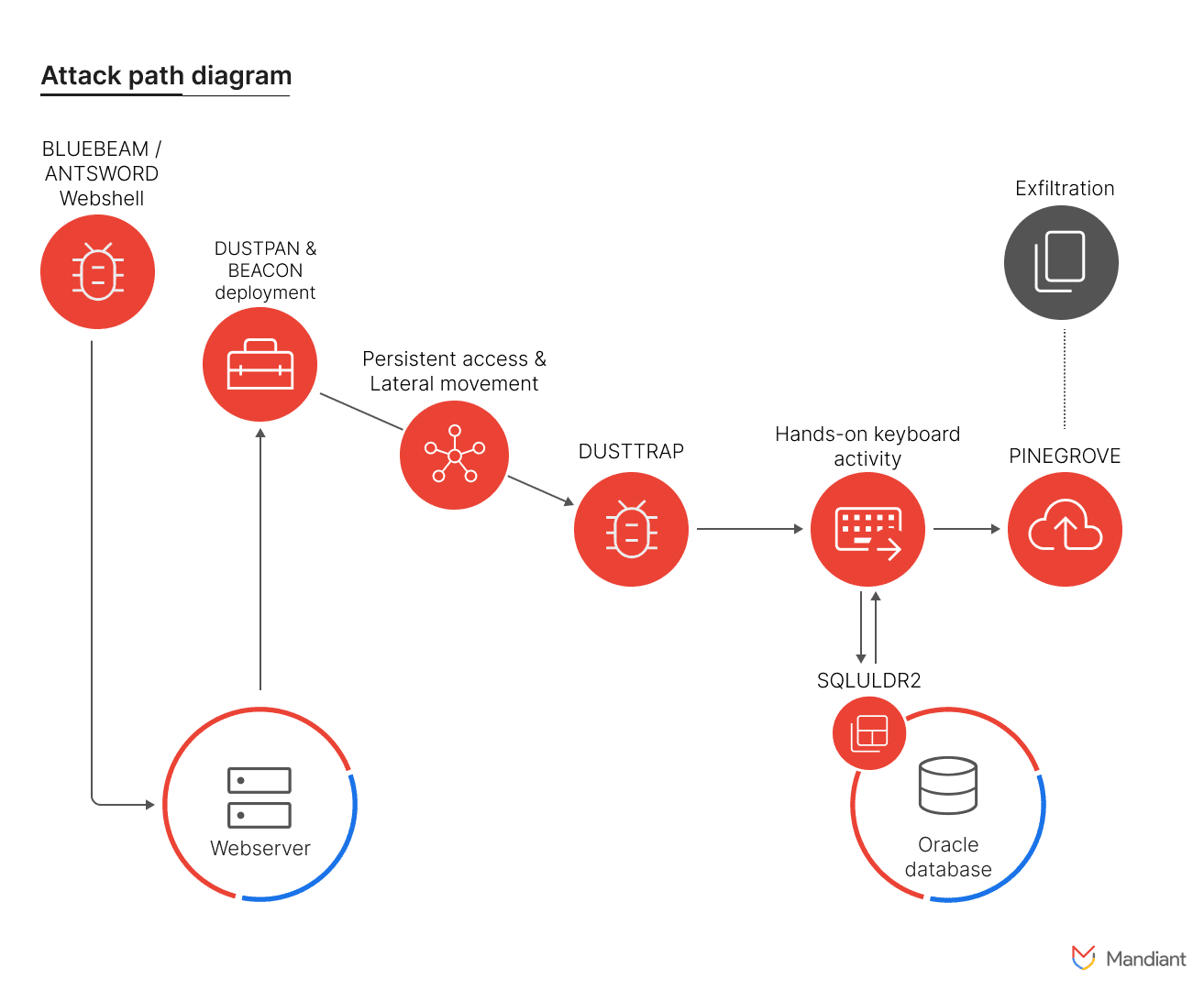
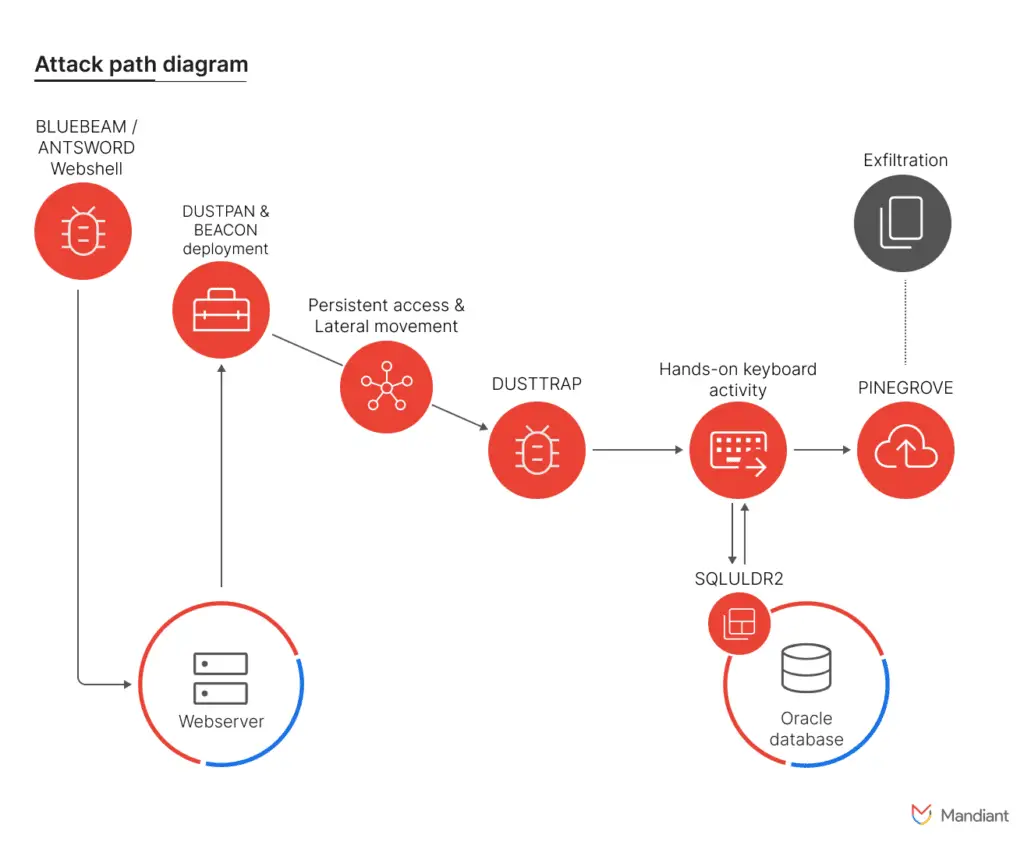
Attack path diagram of observed APT41 attack
Mandiant, in collaboration with Google’s Threat Analysis Group (TAG), has uncovered a widespread cyber espionage campaign orchestrated by the notorious advanced persistent threat (APT) group known as APT41. This sustained operation has compromised multiple organizations across critical sectors worldwide, including shipping and logistics, media and entertainment, technology, and automotive.
The targeted organizations span across continents, with a significant concentration in Italy, Spain, Taiwan, Thailand, Turkey, and the United Kingdom. APT41 employed sophisticated tactics to infiltrate these organizations’ networks, maintaining prolonged, unauthorized access since 2023. This prolonged access enabled the attackers to exfiltrate massive volumes of sensitive data over extended periods.
Among APT41’s arsenal of tools were custom-developed web shells (ANTSWORD and BLUEBEAM), in-memory droppers (DUSTPAN and DUSTTRAP), and data exfiltration tools (SQLULDR2 and PINEGROVE). The group’s multifaceted approach aimed to evade detection and maintain a persistent presence within victim environments.
APT41 is a well-known threat actor with a history of engaging in both state-sponsored espionage and financially motivated cybercrime. While their espionage activities typically target sectors of economic interest, their financially driven operations often focus on the video game industry. The group’s unique blend of espionage and cybercrime tactics makes them a particularly formidable threat.
We strongly recommend that organizations across the targeted sectors conduct thorough investigations to identify potential compromises. Key indicators of compromise include:
- Presence of ANTSWORD, BLUEBEAM, DUSTPAN, or DUSTTRAP malware
- Unauthorized access to Oracle databases or Microsoft OneDrive accounts
- Suspicious activity involving Google Workspace accounts
- Unusual network traffic patterns
Organizations are also urged to implement robust security measures, such as regular security audits, timely software updates, strong access controls, and advanced threat detection solutions, to mitigate the risk of similar attacks in the future.