Cyber-Espionage Campaign Unveiled: Operation Cobalt Whisper Hits Sensitive Industries
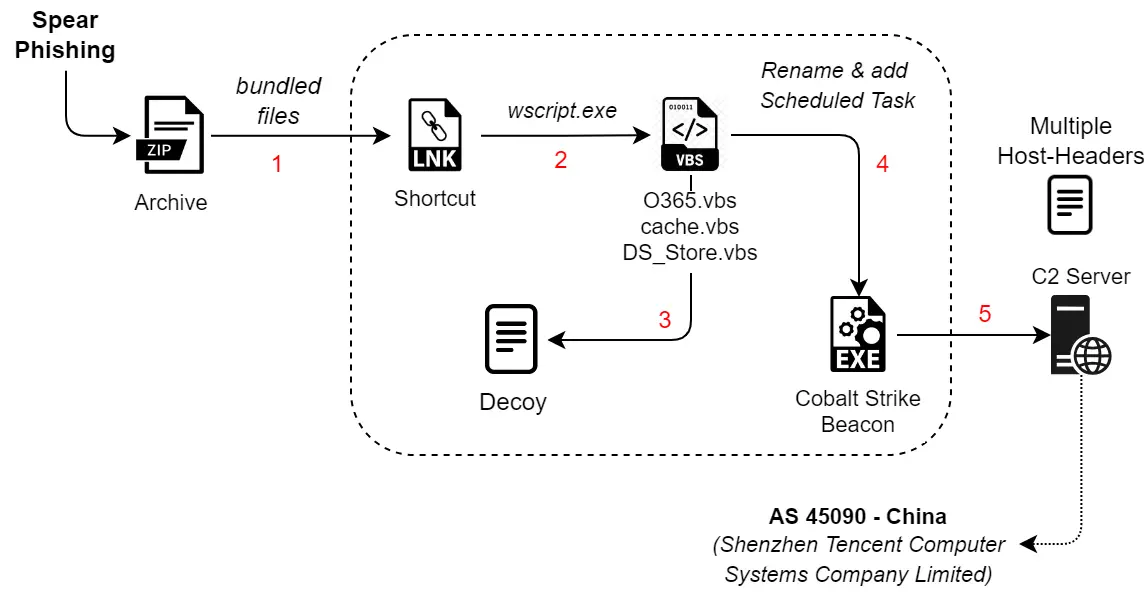
Quick Heal’s SEQRITE Labs has recently uncovered a significant cyber-espionage campaign dubbed Operation Cobalt Whisper, targeting sensitive industries in Pakistan and Hong Kong. The operation, attributed to a yet unidentified Advanced Persistent Threat (APT) group, reveals a sophisticated approach to compromising defense, research, and technical sectors in South Asia through a well-orchestrated series of attacks.
Operation Cobalt Whisper has affected a range of industries, including Defense, Electrotechnical Engineering, Renewable Energy, Civil Aviation, Environmental Engineering, and Academia. “The entire campaign heavily leverages the use of a post-exploitation tool Cobalt Strike, which is deployed using obfuscated VBScrip,” the SEQRITE report notes. The research team identified 20 infection chains, with most targeting Hong Kong and two aimed at Pakistan, employing over 30 decoy files to lure victims.
The attackers use targeted decoy documents related to prestigious events and research awards as a delivery method for their malicious payloads. Among them is a PDF-style LNK file titled, “附件1:《2024年度中国电工技术学会科学技术奖推荐提名书》(技术发明奖和科技进步奖)填报说明(2024年8月新版).pdf.lnk,” which triggers a batch script called O365.vbs. This VBScript file performs multiple malicious actions, including decoding and executing a Cobalt Strike beacon. As SEQRITE explains, “The decoded VBScript renames the backup cache.bak found in the RAR which was delivered to the target to sigverif.exe… and then deletes the original to remove its presence.”
The VBScript creates a persistent backdoor through a scheduled task, allowing attackers to monitor and exploit their target continuously. This beacon connects back to the command-and-control (C2) server, ensuring a steady foothold within the compromised systems.
A distinguishing characteristic of Operation Cobalt Whisper is the repeated use of specific naming conventions across campaigns, notably ImeBroker.exe, which SEQRITE identified in 14 separate samples linked to this operation. These artifacts allowed researchers to trace the threat actor’s broader infrastructure. “This pattern highlights the threat actor’s widespread use of consistent naming and configurations across multiple campaigns,” SEQRITE reports, further indicating the group’s methodical approach.
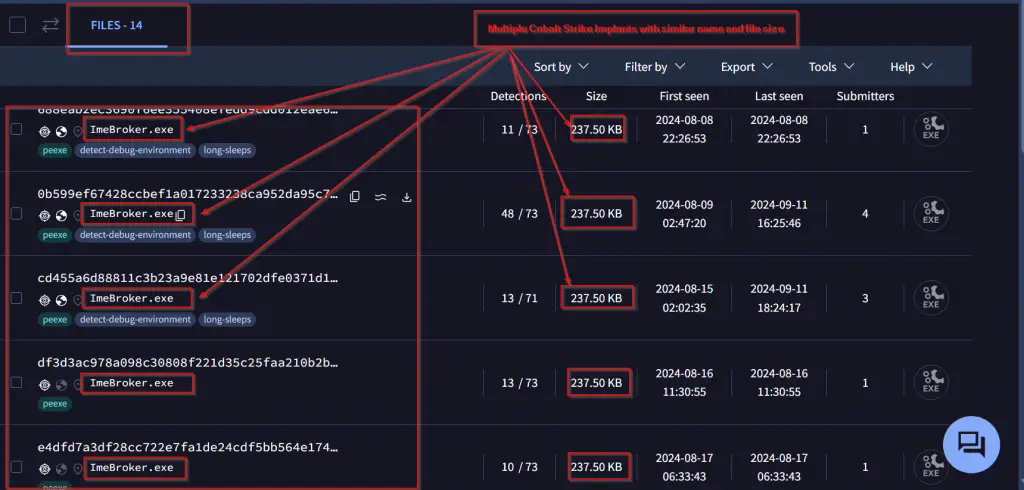
Image: SEQRITE Labs
Operation Cobalt Whisper employs lures tailored to its targets, including documents on military research, electrotechnical studies, and energy infrastructure. The team discovered campaigns targeting the Pakistani Defense Industry and Hong Kong’s electrotechnical researchers. Another campaign focused on cybersecurity researchers in China, with decoys mimicking Chinese cybersecurity entities like CNCERT, underscoring the attackers’ interest in exploiting high-value targets across borders.
The report emphasizes the need for vigilant cybersecurity measures, especially among organizations operating in targeted sectors. Quick Heal recommends updating antivirus solutions, avoiding unknown links, and backing up critical data to prevent such breaches. Organizations are advised to “enable multi-factor authentication” to further bolster their defenses against these sophisticated tactics.
Related Posts:
- From SideCopy to Transparent Tribe: Pakistan APTs Hit Indian Government With RATs
- Phishing for Secrets: Operation RusticWeb Casts Net on Indian Officials
- Seqrite Labs Uncovers New Cronus Ransomware Campaign Utilizing Fake PayPal Documents
- Advanced Cyberattacks: Patchwork APT’s Nexe Backdoor Campaign Exposed





