Phishing for Secrets: Operation RusticWeb Casts Net on Indian Officials
Indian governmental structures and the defense sector have become the targets of a sophisticated hacker attack, leveraging phishing techniques and malicious software based on Rust for intelligence gathering. Dubbed Operation RusticWeb, this campaign, uncovered in October 2023 by cybersecurity firm SEQRITE, demonstrates a nuanced approach to cyber espionage.
As per SEQRITE’s report, the theft of confidential documents involved the deployment of innovative Rust-based payloads and encrypted PowerShell commands. Unlike traditional methods, these tools transmit the harvested data not to a conventional Command and Control (C2) server but rather to a web service.
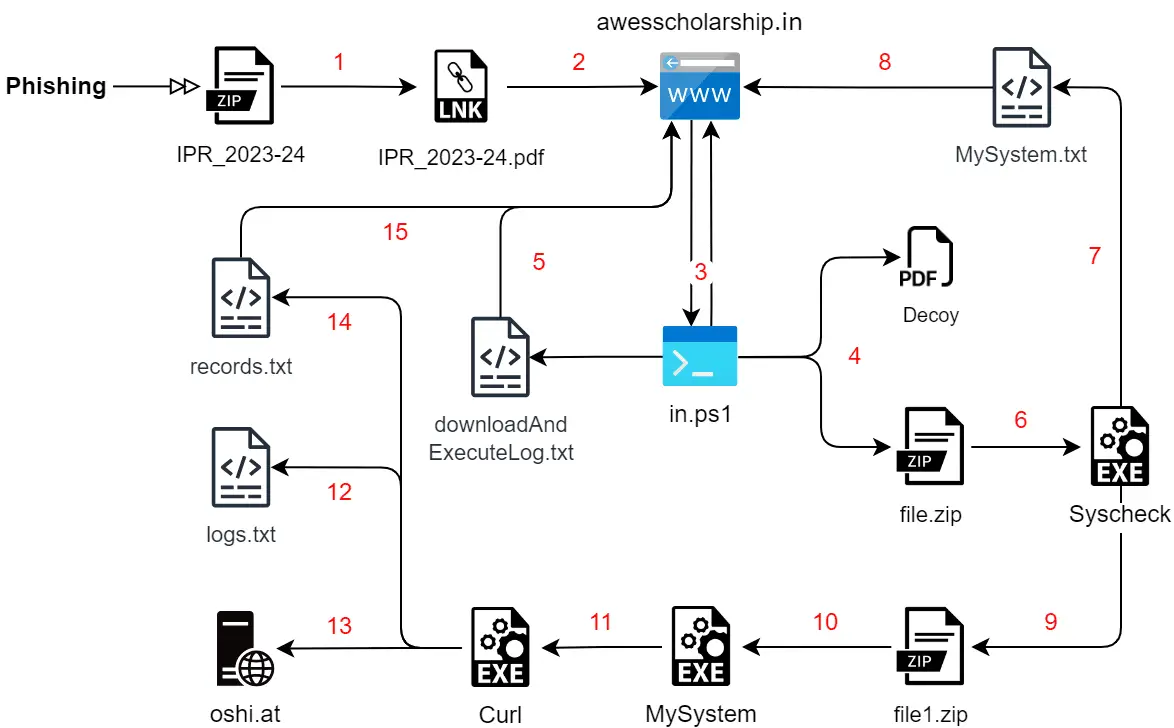
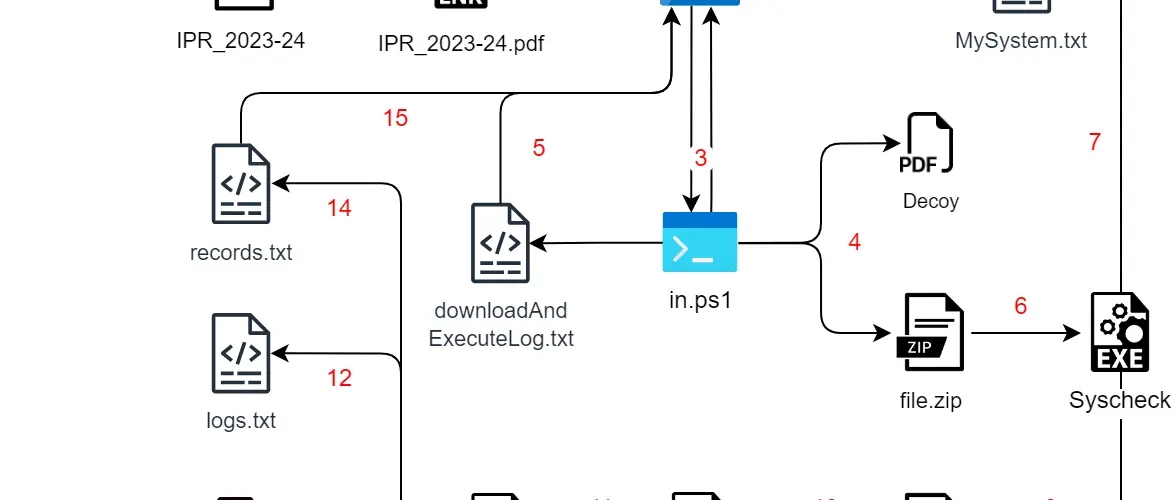
Infection Chain
The analysis indicated tactical connections between this campaign and the activities of groups Transparent Tribe and SideCopy, allegedly linked to Pakistan. SEQRITE’s findings suggest that SideCopy may operate under the aegis of Transparent Tribe. In their latest offensive against Indian government entities, the groups employed the Trojans AllaKore RAT, Ares RAT, and DRat.
ThreatMon observed that recent attacks incorporated the use of counterfeit PowerPoint files and specially crafted RAR archives vulnerable to CVE-2023-38831, enabling the malefactors to gain full remote access and control over the targeted device.
The infection chain of the SideCopy APT Group is multi-staged and meticulously orchestrated to ensure a successful breach. This latest series of attacks commences with a phishing email employing social engineering tactics to deceitfully engage victims with a malicious PDF file. This file delivers Rust-based payloads for file system scanning, while victims are shown a bogus document.
The virus collects files and system information, transmitting them to a C2 server. However, experts note that this malware lacks the functionalities of more advanced malicious programs available in the cybercrime market.
Another infection chain identified by SEQRITE in December is also multi-tiered but replaces the Rust malware with a PowerShell script. At the end of this chain, a Rust executable file named “Cisco AnyConnect Web Helper” is used. The collected data are sent to the domain “oshi[.]at,” a public file service known as OshiUpload.
“Operation RusticWeb could be linked to an APT threat as it shares similarities with various Pakistan-linked groups,” Ram Prakki said.






