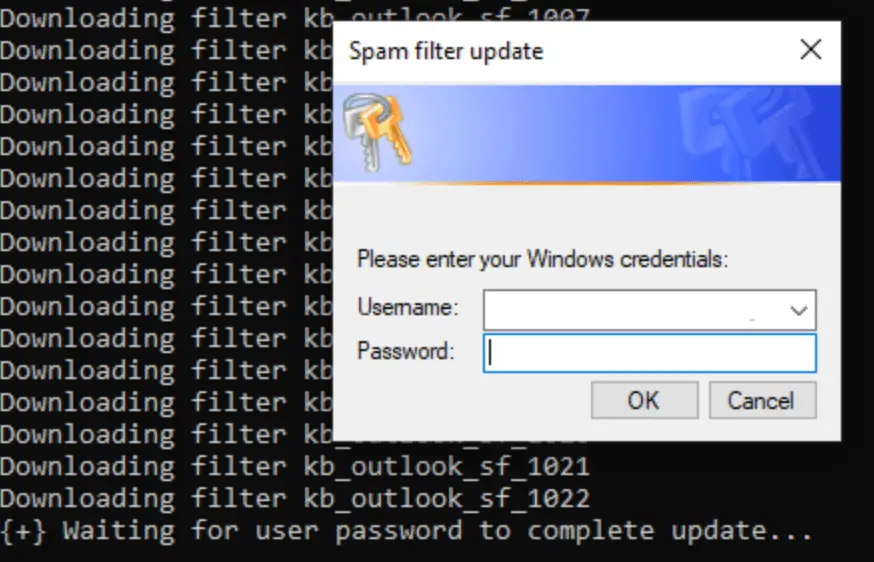
Credential harvester prompt spawned by `AntiSpam.exe | Image: Rapid7
Recently, cybersecurity firm Rapid7 identified a series of sophisticated intrusion attempts linked to an ongoing social engineering campaign that has been actively monitored by its threat intelligence team. The campaign, which has been targeting organizations with a mix of deception and technical subterfuge, has recently evolved, with threat actors adopting new tools and techniques to bypass security measures and compromise systems.
The core strategy of the campaign remains consistent: threat actors initiate their attack with an overwhelming “email bomb,” flooding users with benign emails. This initial barrage is followed by direct contact, typically through Microsoft Teams, where the attackers pose as technical support agents offering to resolve the very issue they’ve created. In a convincing display of social engineering, the threat actors persuade users to download and install AnyDesk, a legitimate remote access tool, granting them full control over the victim’s system.
Once inside, the attackers swiftly move to execute payloads and exfiltrate sensitive data. In past incidents, Microsoft’s Quick Assist was often used as the remote access tool of choice; however, Rapid7 reports that recent cases have exclusively featured AnyDesk, marking a shift in the tools deployed by the attackers.
In a significant departure from previous methods, Rapid7’s investigation revealed that the attackers have replaced their older credential harvesting scripts with a new 32-bit .NET executable named AntiSpam.exe. This malicious file masquerades as an email spam filter updater, aligning with the initial social engineering lure of spam emails. When executed, AntiSpam.exe prompts users to enter their credentials into a pop-up window, which the executable then logs and stores on disk, along with system enumeration information. Even incorrect credentials are captured, with the user being prompted to retry until the correct information is obtained.
The campaign doesn’t stop at credential harvesting. Following the execution of AntiSpam.exe, attackers deploy a series of binaries and PowerShell scripts aimed at establishing connections to their command and control (C2) servers. Rapid7 identified several payloads in this stage, all named to maintain the appearance of legitimate software updates, such as update1.exe, update4.exe, and update6.exe.
One of the most concerning discoveries in Rapid7’s report is the use of the payload update6.exe, which attempts to exploit CVE-2022-26923—a known vulnerability that allows the creation of a machine account within a domain. This capability is leveraged by attackers for Kerberoasting, a technique used to escalate privileges by extracting service account credentials from domain controllers. The exploitation of this vulnerability, especially within environments with unpatched domain controllers, presents a serious threat to organizations, potentially allowing attackers to move laterally and gain deeper access to the network.
In addition to the primary payloads, Rapid7 observed the use of reverse SSH tunnels and the Level Remote Monitoring and Management (RMM) tool. These tools are employed to facilitate lateral movement across compromised networks and to establish persistent access, ensuring that the attackers can maintain control over the environment even after initial detection.
Organizations are urged to baseline their environments for all installed remote monitoring and management solutions and to employ application allowlisting technologies like AppLocker or Microsoft Defender Application Control. These tools can block unapproved RMM solutions from executing within the network, thereby limiting the attackers’ ability to deploy malicious payloads.
Related Posts:
- How an Attacker Took Control of an Active Directory Domain Using CVE-2022-26923
- Kimsuky APT: New TTPs Revealed in Rapid7 Cybersecurity Report
- Sophisticated Social Engineering Campaign Linked to Black Basta Ransomware
- Apache ActiveMQ Servers Exploited by HelloKitty Ransomware