Image: Malwarebytes Labs
A recently discovered malvertising campaign targeting Slack users has highlighted the increasingly sophisticated tactics employed by cybercriminals. Security researchers at Malwarebytes Labs have uncovered a complex scheme that leverages Google Search ads, click trackers, and cloaking domains to deliver malware payloads.
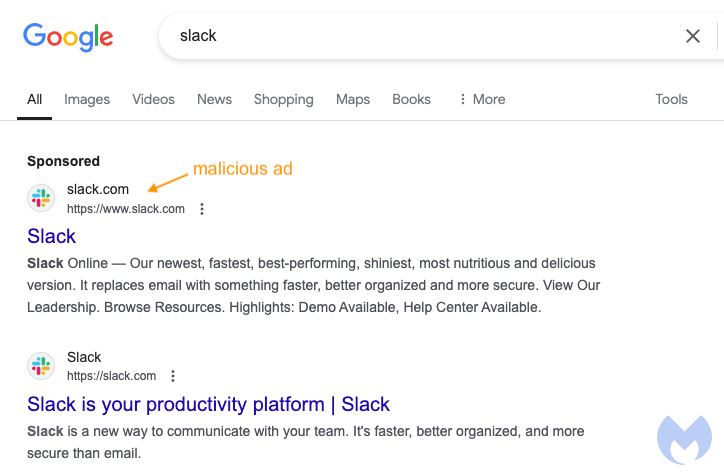
For several days, a seemingly legitimate ad for Slack appeared at the top of Google search results, blending seamlessly with authentic listings. To the unsuspecting eye, it was just another promotional link for Slack. Clicking on it initially redirected users to the official Slack website, reinforcing its appearance of legitimacy. However, security experts at Malwarebytes knew better. The ad was flagged as suspicious, and they began to closely monitor its behavior.
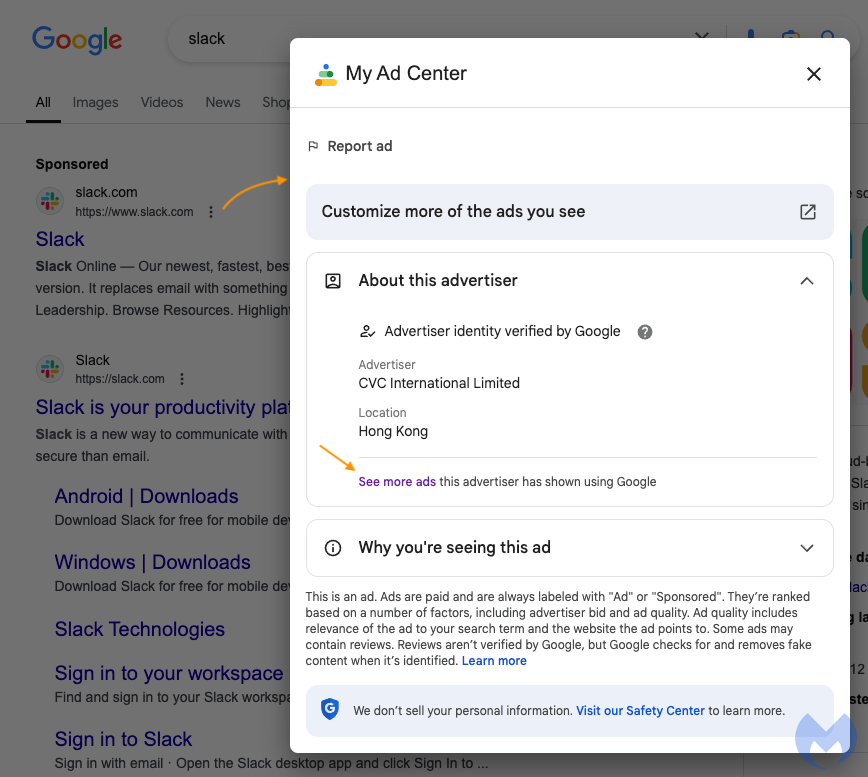
Contextual clues provided the first hints of the ad’s true nature. A deeper investigation into the Google Ads Transparency Center revealed that the advertiser behind the Slack ad was also promoting products targeted at the Asian market, an incongruous mix that raised further suspicions. This is a classic example of how contextualized detection can help identify compromised advertiser accounts.
For days, the ad remained benign, redirecting users to Slack’s official pricing page. But in the world of malvertising, patience is a virtue. Threat actors often allow their ads to “cook,” lulling security systems into a false sense of security before weaponizing them. Eventually, Malwarebytes detected a change: the ad began redirecting to a click tracker, a common tactic used by malvertisers to obfuscate the true destination of their ad traffic.
The ad’s final destination soon became the domain slack-windows-download[.]com, a suspicious URL that had been registered just days before. While the page initially appeared harmless, likely generated automatically through AI, further investigation revealed a more sinister purpose. Through a series of tweaks and network traffic captures, Malwarebytes was able to bypass the decoy page and access the malicious content hidden within.
This sophisticated cloaking technique—where different users are shown different content—made the ad even more dangerous. The malicious page was designed to impersonate Slack, complete with a download button that delivered a harmful payload to unsuspecting victims. Dynamic analysis of the download revealed a connection to a remote server associated with SecTopRAT, a remote access Trojan with data-stealing capabilities, previously used in malvertising campaigns targeting other popular platforms like Zoom and NordVPN.
In response, Malwarebytes reported the fraudulent ad to Google, and the decoy domains used in the campaign have since been flagged by Cloudflare as phishing sites. However, the threat remains. As malvertisers continue to refine their techniques, leveraging both free and paid platforms, cybersecurity professionals must remain vigilant.
Related Posts:
- NordVPN Impersonators Exploit Bing Ads to Spread SecTopRAT Malware
- Google Products Exploited in Sophisticated Malvertising Scheme
- Beware of Fake AI Photo Editors on Social Media: Malvertising Campaign Targets Credentials