
In the wake of a widespread system outage triggered by a faulty CrowdStrike update, cybercriminals have wasted no time exploiting the chaos. Within 24 hours of the incident, which affected millions of Windows devices globally, malicious actors created numerous deceptive domains aimed at capitalizing on the confusion and urgency surrounding the situation.
The following day, July 20th, 2024, CrowdStrike released a technical briefing revealing that a logic error in a channel file was the root cause of the BSOD. This faulty channel file, designed to detect newly observed malicious named pipes for identifying standard Command and Control (C2) frameworks in cyberattacks, inadvertently triggered the crashes. CrowdStrike also emphasized that a thorough root cause analysis was underway to fully understand the origin of this logic error.
Security experts and researchers have swiftly identified these malicious domains, which range from phishing sites masquerading as official CrowdStrike support to fraudulent services claiming to offer solutions for the outage.
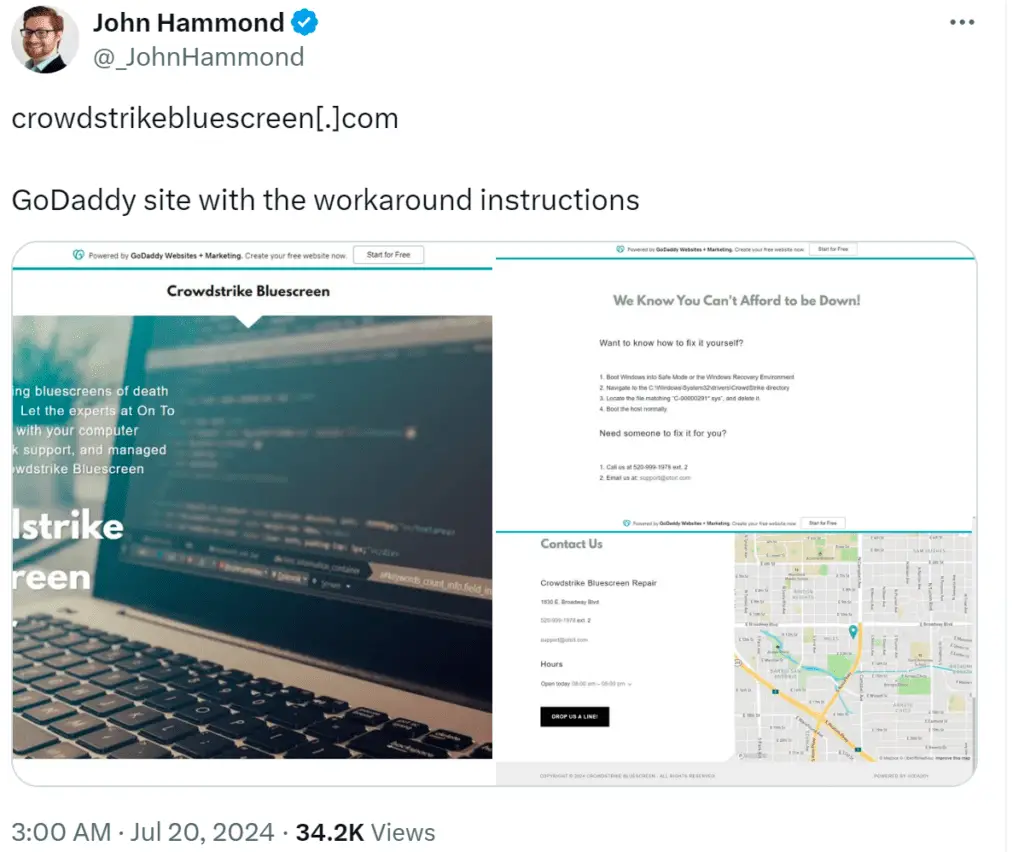
One notable example is “crowdstrikeclaim.com,” which promises a “free claim review” for affected organizations but actually collects sensitive personal and organizational data, posing a significant risk of identity theft and unauthorized access. Another domain, “crowdstrikebluescreen.com,” offers services to affected organizations, potentially diverting resources and attention away from addressing the actual outage.
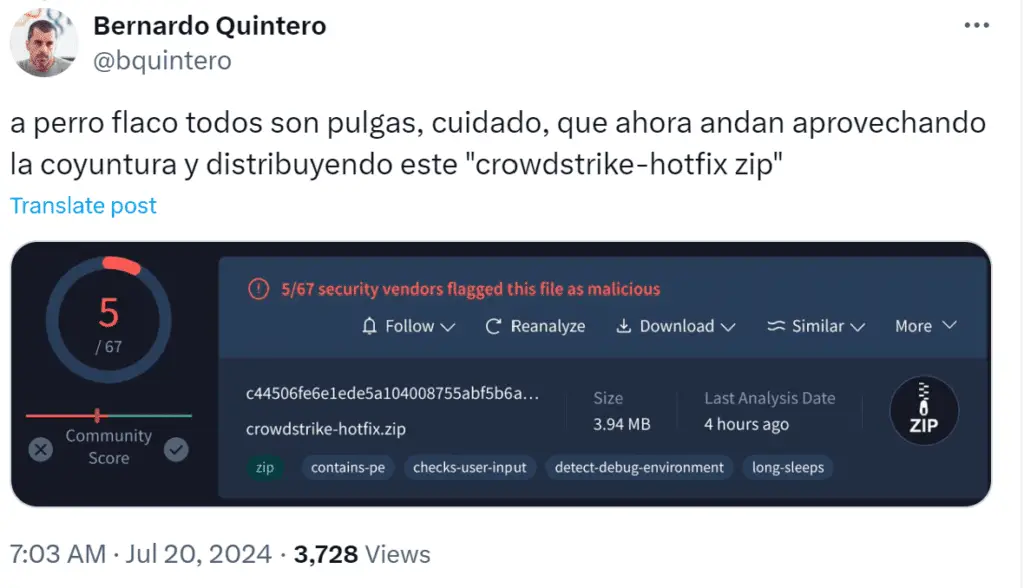
Adding to the concern, VirusTotal founder Bernardo Quintero has reported the distribution of malware disguised as a hotfix for the CrowdStrike issue. This deceptive tactic highlights the lengths to which threat actors are willing to go to exploit the current situation for their gain.
As organizations and individuals grapple with the aftermath of the CrowdStrike outage, it’s imperative to exercise heightened caution and skepticism when dealing with any unsolicited offers or requests related to the incident.
Key recommendations for staying safe include:
- Avoid sharing personal or organizational information on unverified websites or with unknown individuals.
- Verify the legitimacy of any service provider before engaging with them.
- Rely exclusively on official CrowdStrike support channels for remediation steps and instructions.
- Keep antivirus and anti-malware software up-to-date and scan all downloaded files before opening them.
- Educate employees and stakeholders about recognizing and avoiding phishing attempts and other social engineering tactics.
Related Posts
- Widespread Outage: CrowdStrike Update Affects 8.5 Million Windows Users
- CrowdStrike Reveals Technical Details of Update Causing Windows Systems Crash
- CrowdStrike Global Threat Report: extortion and weaponization of data have become mainstream among cybercriminals
- Hackers launched SSH brute-force attacks on Linux systems to deploy Chaos backdoors