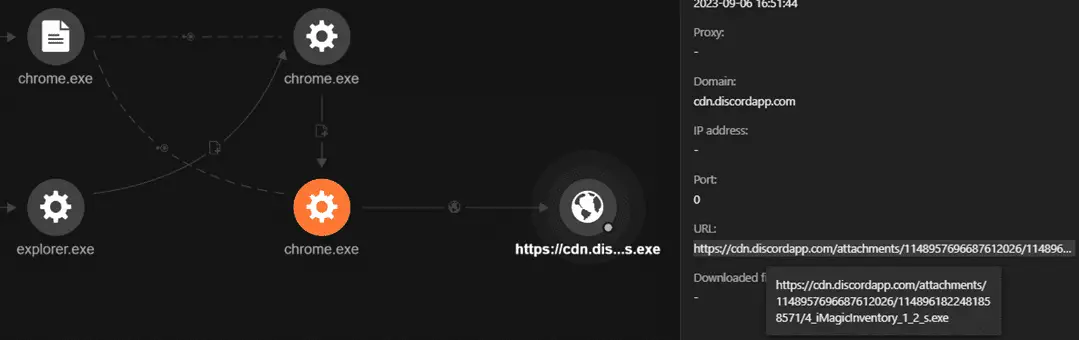
The user accessed Discord via Google Chrome to download the malicious file “4_iMagicInventory_1_2_s.exe” that contains Lumma Stealer, as seen on the Trend Vision One™ Workbench. | Image: Trend Micro
In a concerning revelation, Trend Micro’s security researchers have spotlighted a sinister trend: cybercriminals are deploying a pernicious malware named Lumma Stealer via Discord. This platform, a staple for gamers, streamers, and content creators, is now a conduit for a stealthy cyber threat.
The insidious exploit begins with Discord’s content delivery network (CDN). Malicious actors exploit it to host Lumma Stealer. To compound the complexity, Discord’s application programming interface (API) is also manipulated to generate bots, which can communicate with this malware. Their audacity doesn’t end there; these bots can transmit the purloined data to clandestine Discord channels.
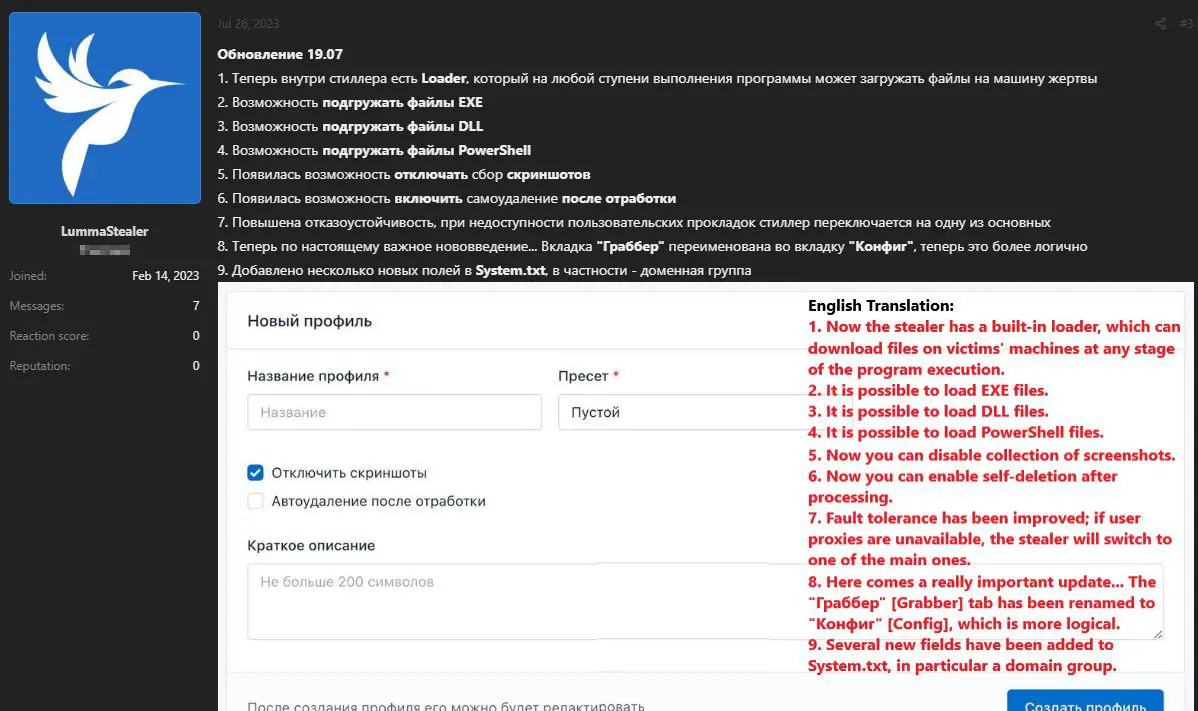
Composed in the C programming language, this malware pilfers user credentials. Making its ominous debut in August 2022, Lumma Stealer’s cyber perpetrators honed in on YouTube users through spear-phishing endeavors. Now, the stealer’s blueprints are up for grabs on the shadowy recesses of the internet, with prices commencing at a staggering USD$250 monthly. Packages range from basic log analysis tools to a staggering US$20,000 plan, offering the malware’s source code and resale rights.
Diving deeper, the modus operandi of these cyber rogues is chillingly simple. Victims find themselves ensnared through direct Discord messages from either random or compromised accounts. With promises of compensation for a mere few minutes of game reviewing, victims are lured. And should they bite? A malicious file swiftly finds its way onto their system.
During Trendmicro’s investigation, the particular malevolent link, when accessed via Google Chrome, instigated the downloading of “4_iMagicInventory_1_2_s.exe”, the vessel for Lumma Stealer. Once activated, it links to a notorious domain, aiming to snatch cryptocurrency wallets and browser data.

But Lumma Stealer isn’t static. The underworld buzzes with its evolving prowess. It can now load diverse files, some serving as gateways to other malware. Moreover, it boasts an AI-driven capability to discern “bots”, which likely means analysis environments or emulators.
Closing on a cautionary note, while technology offers boundless possibilities, it’s imperative to tread with discernment. Unsolicited messages, especially those carrying attachments or links, should be treated with suspicion. Bolstering defenses with robust antivirus solutions, maintaining a vigilant eye on communication tools, and ensuring continuous cybersecurity education is more crucial than ever in our interconnected digital age.