Cybereason Uncovers Widespread Exploitation of Apache ActiveMQ Vulnerability
In a newly released Threat Analysis report, Cybereason Security Services has sounded the alarm about a dangerous wave of attacks targeting a critical vulnerability (CVE-2023-46604) in the Apache ActiveMQ messaging service. Threat actors have been exploiting this flaw with alarming speed and diverse tactics, underscoring the urgency for immediate mitigation steps.
The Vulnerability Detail

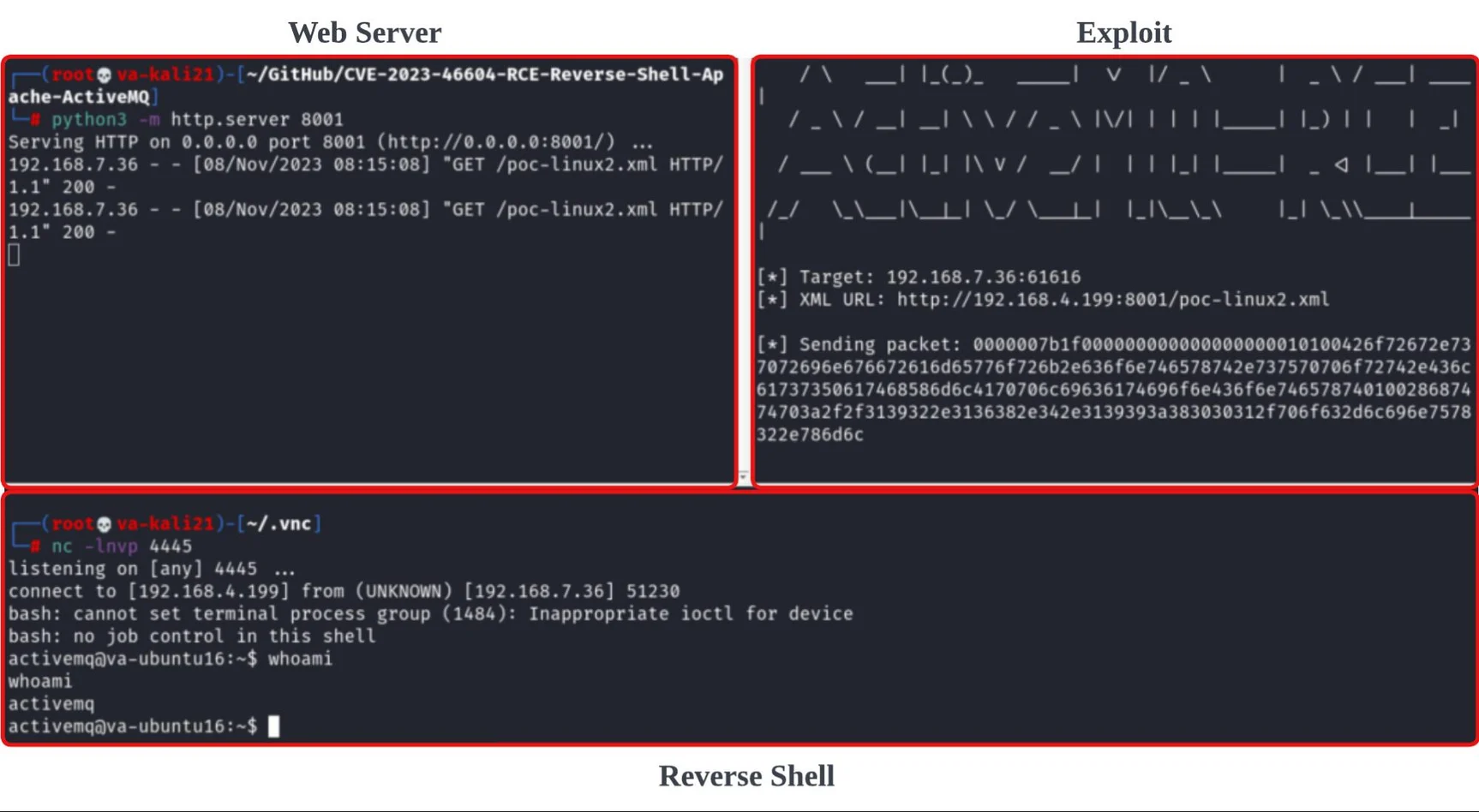
Exploitation Of CVE-2023-46604 | Image: Cybereason Security Services
CVE-2023-46604 centers on a weakness in the way Apache ActiveMQ Artemis and Classic versions handle certain network protocols. This vulnerability allows attackers without any prior authentication to run arbitrary code on vulnerable systems. The potential consequences are severe, ranging from data theft and unauthorized access to a complete system takeover.
Attack Timeline Raises Concern
The most unsettling aspect of this Cybereason report is the timeline: attacks abusing this vulnerability began on October 11th, 2023, a full 16 days before the CVE was officially disclosed and a patch was made available. This highlights the sophistication of modern threat actors, who can identify and exploit critical flaws even before security teams are fully aware of them.
Opportunistic Mayhem: Diverse Payloads Observed
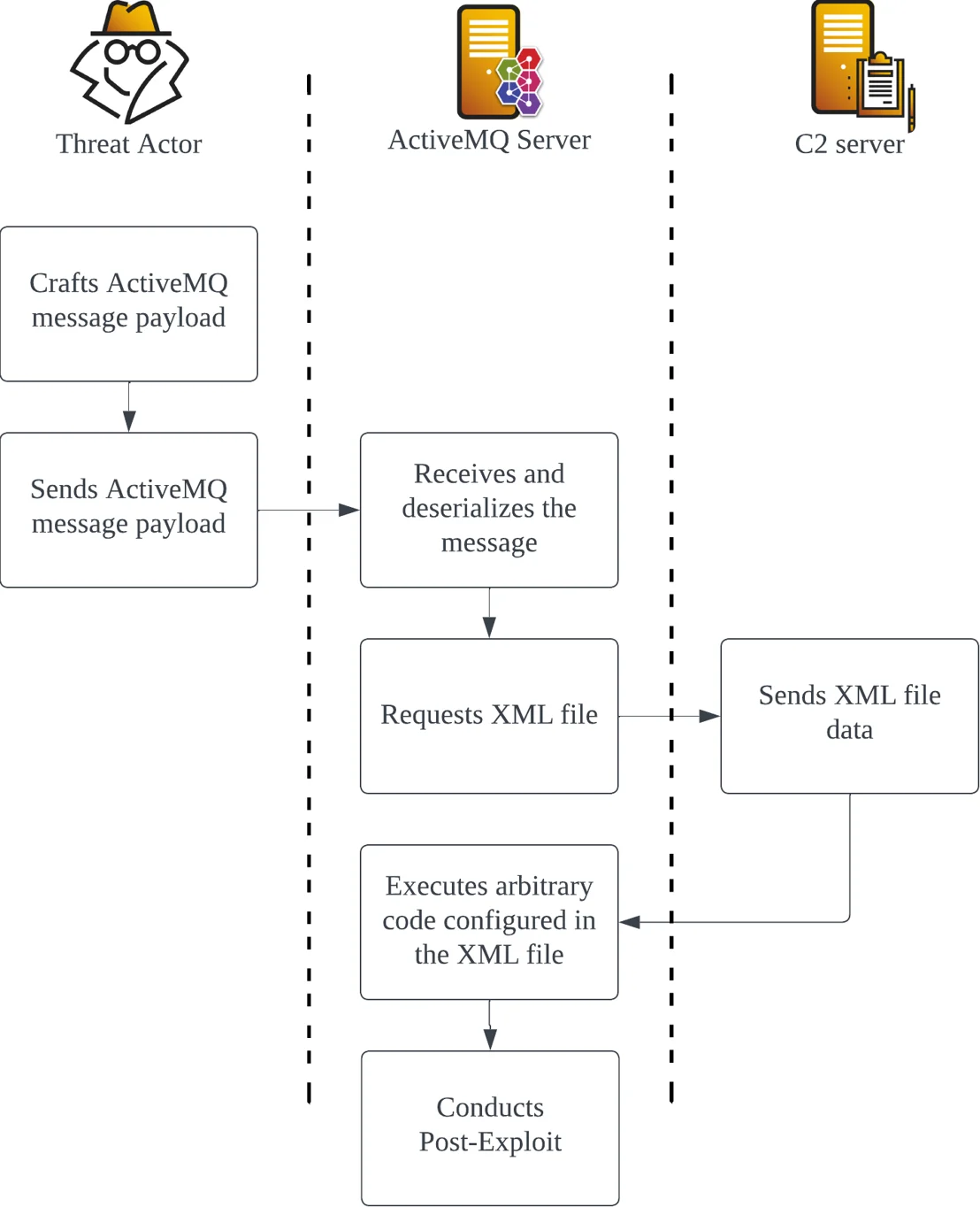
CVE-2023-46604 Exploit Flowchart | Image: Cybereason Security Services
Further analysis reveals that multiple threat groups are likely capitalizing on this exploit. Cybereason analysts observed an alarming variety of malicious payloads deployed on a single compromised server. These included:
- Mirai Botnet: Expanding botnet armies used to launch overwhelming DDoS attacks, crippling victim websites and services.
- HelloKitty Ransomware: Encrypting vital files and extorting organizations for decryption keys.
- SparkRAT: A potent Remote Administration Tool that gives attackers extensive control over compromised systems, facilitating data theft and further intrusion.
- Coinminers (XMRig, XMRigCC): Stealing precious computing power to mine cryptocurrency, degrading system performance, and profiting at the victim’s expense.
Varied Attack Strategies
The report underscores that threat actors exploiting CVE-2023-46604 operate with different tempos and goals. Some attacks are automated and focus on rapid deployment, while others involve manual commands and a slower, more methodical approach, suggesting attackers unconcerned with speed who may be laying the groundwork for more elaborate attacks.
Mitigating the Threat: Urgent Actions Required
- Patch Now: Install the latest security updates for Apache ActiveMQ Artemis and Classic as soon as possible. There is no time to waste.
- Enhanced Monitoring: Scrutinize network logs for any indications of compromise. Look for suspicious commands, unusual traffic patterns, or connections to unknown command-and-control servers.
- Threat Intelligence: Subscribe to up-to-date threat intelligence feeds to stay informed about the evolving tactics used to exploit this and other vulnerabilities.
- Defense in Depth: Single-point security solutions are insufficient. Implement a layered approach with firewalls, intrusion detection systems, endpoint protection, and regular vulnerability scanning.




