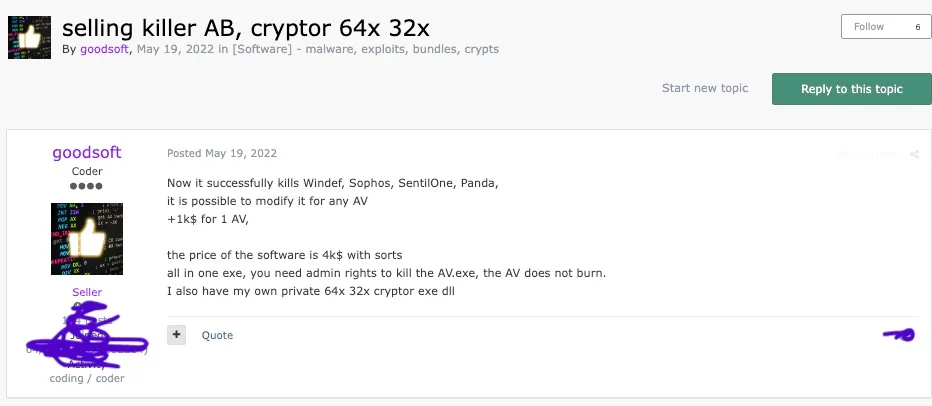
AV killer advertisement by ‘goodsoft’, Google translated from RU
Experts at SentinelLabs have uncovered new evidence that the infamous hacker group FIN7 continues to refine its attack methods and expand its influence in the criminal underworld. According to recent research, the hackers use numerous aliases to mask their true identities and sustain criminal operations on underground forums.
FIN7 has been active since 2012, causing significant damage across various economic sectors, including hospitality, energy, finance, high technology, and retail.
Initially, FIN7 utilized malware targeting POS terminals for financial fraud. However, since 2020, the group has shifted its focus to ransomware operations, aligning with prominent RaaS (Ransomware as a Service) groups like REvil and Conti, and launching their own RaaS programs under the names Darkside and BlackMatter.
One of FIN7’s distinctive features is the creation of fake cybersecurity companies. The group established fictitious firms like Combi Security and Bastion Secure to deceive.
Despite the arrests of some members, FIN7’s activities persist, indicating shifts in tactics, temporary lulls, or the emergence of splinter groups.
New data reveals that FIN7 actively sells its tools on criminal forums. Researchers found advertisements offering a specialized tool for bypassing security systems called AvNeutralizer (also known as AuKill).
Analysis of activity on various underground forums revealed several aliases likely associated with FIN7:
- “goodsoft”
- “lefroggy”
- “killerAV”
- “Stupor”
These users posted similar advertisements for selling tools to bypass antivirus systems and post-exploitation frameworks.
FIN7’s arsenal includes a range of sophisticated tools, each designed for a specific attack phase:
- Powertrash: a heavily obfuscated PowerShell script for reflective loading of PE files into memory.
- Diceloader (also known as Lizar and IceBot): a minimal backdoor for establishing command and control (C2) channels.
- SSH-based Backdoor: a set of tools based on OpenSSH and 7zip to ensure persistent access to compromised systems.
- Core Impact: a commercial penetration testing tool used by FIN7 to exploit vulnerabilities.
- AvNeutralizer: a specialized tool for bypassing security solutions.
The evolution of AvNeutralizer is particularly noteworthy. The latest version of this malware uses a previously unknown technique to bypass certain implementations of protected processes, leveraging the built-in Windows driver ProcLaunchMon.sys (TTD Monitor Driver).
FIN7 also developed an automated attack system called Checkmarks. This platform primarily targets publicly accessible Microsoft Exchange servers, exploiting ProxyShell vulnerabilities (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207).
Moreover, the Checkmarks platform includes an Auto-SQLi module for SQL injection attacks. If initial attempts fail, the SQLMap tool scans targets for potential SQL injection vulnerabilities.
Researchers detected numerous intrusions exploiting SQL injection vulnerabilities targeting publicly accessible servers through automated exploitation. These attacks are attributed to FIN7 with moderate confidence. Most of these intrusions occurred in 2022, especially in the third quarter, affecting American companies in the manufacturing, legal, and government sectors.
Observed exploitation activities involve using multi-layer obfuscated PowerShell droppers, ultimately leading to the download and execution of malicious payloads.
The study of FIN7’s activities highlights the adaptability, persistence, and continuous evolution of this threat group. The development and commercialization of specialized tools like AvNeutralizer on underground forums significantly amplifies the group’s impact.
FIN7’s ongoing innovations, particularly in sophisticated methods to circumvent security measures, demonstrate a high level of technical expertise. The use of multiple aliases and collaboration with other cybercriminal groups complicates attribution and underscores FIN7’s advanced operational strategies.
Related Posts:
- FIN7 Hackers Using Signed Malware and Fake Google Ads to Evade Defenses
- Inside DiceLoader: How FIN7’s Malware Masters Evasion
- Malware Masquerade: HubSpot, Veeam, Xero – Carbanak Lures Victims with Trust
- LockBit Ransomware Gang Exposes Boeing’s Data in Public Leak