DavRelayUp: A universal no-fix local privilege escalation in domain-joined windows workstations
DavRelayUp
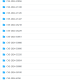
A quick and dirty port of KrbRelayUp with modifications to allow for NTLM relay from webdav to LDAP in order to streamline the abuse of the following attack primitive:
- (Optional) New machine account creation (New-MachineAccount)
- Force start the WebClient service
- Start webdav relay server (GoRelayServer – a golang DLL that is embedded in DavRelayUp using Costura.Fody)
- Local machine account auth coercion (SharpSystemTriggers)
- NTLM relay to LDAP
- Add RBCD privs and obtain privileged ST to the local machine (Rubeus)
- Using said ST to authenticate to the local Service Manager and create a new service as NT/SYSTEM. (SCMUACBypass)
This is essentially a universal no-fix local privilege escalation in domain-joined Windows workstations where LDAP signing is not enforced (the default settings).

Mitigation & Detection
- Enforce LDAP Signing and LDAP Channel Binding to mitigate the relay of the machine account auth to LDAP. This can be configured via the “Domain Controller: LDAP server signing requirements” GPO. (Thank you Will Dormann for your tweet on this matter)
- Make the attack requirements harder to obtain by setting the MS-DS-Machine-Account-Quota attribute in AD to 0, thus removing the ability of any user to add a new machine account to the domain. This is a dangerous default setting in AD – make sure you change it.
- Setting the flag “Account is sensitive and cannot be delegated” on all admin accounts (or put them in protected users) would make it so there is no account with the privileges required that can be delegated in order to complete the attack path. (Thanks to Christoph Falta for this tweet)
- Resources for possible monitoring and detection rules:
- https://github.com/tsale/Sigma_rules/blob/main/windows_exploitation/KrbRelayUp.yml (@Kostastsale)
- https://twitter.com/SBousseaden/status/1518976397364056071 (@SBousseaden). Mainly the rule about authentication to Service Manager via Kerberos from 127.0.0.1, Great Work!.
- https://www.linkedin.com/posts/john-dwyer-xforce_threathunting-threatdetection-blueteam-activity-6924739962131140608-py45/ (John Dwyer @TactiKoolSec)