Deep Instinct Security Researcher Eliran Nissan has uncovered a new and potent lateral movement technique, “DCOM Upload & Execute,” redefining how attackers might exploit Distributed Component Object Model (DCOM) interfaces for remote code execution. This research not only details the vulnerabilities but also highlights an advanced method of exploiting the IMsiServer interface in Windows systems to install backdoors.
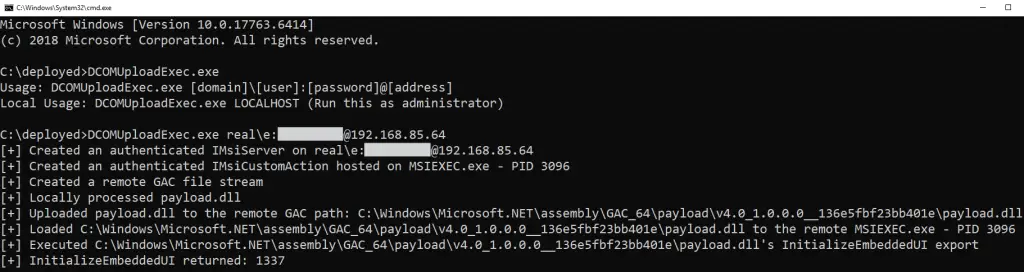
The newly revealed attack bypasses traditional DCOM hardening mechanisms by exploiting the IMsiServer COM interface, a component of the Windows Installer service. The report describes the technique as a “powerful new DCOM lateral movement attack that allows the writing of custom DLLs to a target machine, loading them to a service, and executing their functionality with arbitrary parameters.”
Unlike prior DCOM exploits, this method does not rely on the commonly documented IDispatch interfaces, thus evading many conventional detection mechanisms. Instead, it delves into undocumented IMsiServer functionalities using advanced reverse-engineering techniques to achieve remote execution.
The attack unfolds in several stages:
- DLL Creation and Upload: Using functions within the IMsiCustomAction interface, attackers can upload malicious DLLs to the target’s Global Assembly Cache (GAC) in a predictable path.
- Remote Execution: The LoadEmbeddedDLL method is then used to load the payload, followed by invoking CallInitDLL to execute exported functions from the malicious DLL.
- Backdoor Functionality: Once executed, the attacker can remotely interact with the payload, effectively embedding a backdoor into the victim’s system.
The researcher has also developed a working proof-of-concept (PoC) tool to demonstrate the attack on the latest Windows builds.
Key Features of the Attack
- Novel Exploitation Path: Unlike previous DCOM attacks that targeted well-known interfaces like IDispatch, this method expands the attack surface to less-documented interfaces like IMsiServer.
- Stealthy Lateral Movement: By leveraging obscure COM objects, the attack bypasses many traditional monitoring tools.
- Predictable File Path: Custom payloads are strategically placed in the GAC for reliable execution.
Limitations and Indicators of Compromise
While the attack is powerful, it is constrained by certain conditions:
- Both attacker and victim systems must be in the same domain or forest.
- The payload must be a strong-named .NET assembly, either x86 or x64.
The attack leaves behind clear indicators of compromise (IOCs):
- Remote authentication logs showing DCOM access.
- MSIEXEC processes with unusual child processes.
- Malicious DLLs written to and loaded from the GAC.
The “DCOM Upload & Execute” technique highlights the evolving complexity of lateral movement attacks. By bypassing traditional exploitation pathways, this research reveals how overlooked or under-documented COM interfaces can serve as powerful attack vectors. The report warns, “The research presented here proves that many unexpected DCOM objects may be exploitable for lateral movement, and proper defenses should be aligned.”