NAS maker QNAP continues to issue security alerts, and QNAP says ransomware called DeadBolt is looking for NAS servers exposed on the public internet. Earlier this month, QNAP issued an alert saying it had detected a large number of attacks of unknown origin, which sought to exploit vulnerabilities and weak passwords in devices exposed on the public Internet.
QNAP did not mention whether the ransomware in the warning was related to the attack at the beginning of the month, but judging from the content of the two warnings, it should be the same batch of attacks.
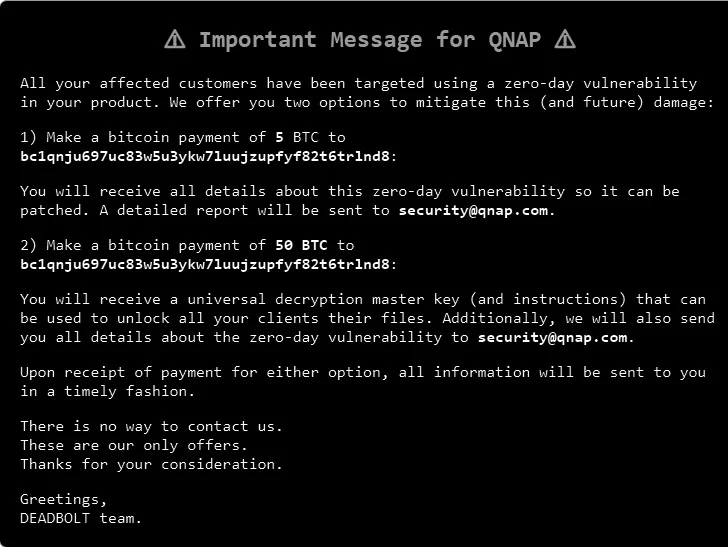
“DeadBolt has been widely targeting all NAS exposed to the Internet without any protection and encrypting users’ data for Bitcoin ransom,” the company said. “QNAP urges all QNAP NAS users to […] immediately update QTS to the latest available version.”

Use the built-in security advisory function of the QNAP device to scan the potential risks of the device, including detecting whether the device is exposed to the public network and specific open ports. If the scanning shows that the system management service can be accessed from an external address then the device is at high risk and the user should follow the security advisor guidelines to disable public network access. Including disabling external address access, disabling exposed ports, turning off port forwarding or UPnP on the router, and DMZ to ensure that the internal network cannot be accessed from the outside. Of course, the result of this is that users will not be able to access QNAP devices through the external network. If you really need external network access, you can try other methods to strengthen security. Including but not limited to using multi-factor authentication, using high-strength passwords, non-repeating passwords, or using encrypted tunnels to connect to the intranet before using the intranet to access.