DeathNote Malware: Lazarus Group’s New Weapon Against Defense Industry
The Lazarus Group, a high-profile Korean-speaking threat actor, has long targeted cryptocurrency-related businesses. However, recent Kaspersky reports indicate an evolution in their tactics, techniques, and procedures, with shifts in targets and the refinement of their tools. The group has shown particular interest in sectors connected to the defense industry.
In mid-October 2019, security researchers discovered a significantly modified piece of malware, named the active cluster DeathNote. This malware has been utilized in various campaigns since October 2018, primarily targeting the cryptocurrency business. Researchers have observed potential compromises of individuals or companies involved in cryptocurrency across Cyprus, the United States, Taiwan, and Hong Kong.
Infection procedure | Image: Kaspersky
In April 2020, the DeathNote cluster began targeting the automotive and academic sectors in Eastern Europe, both connected to the defense industry. At this point, the actor switched all decoy documents to job descriptions related to defense contractors and diplomatic services.
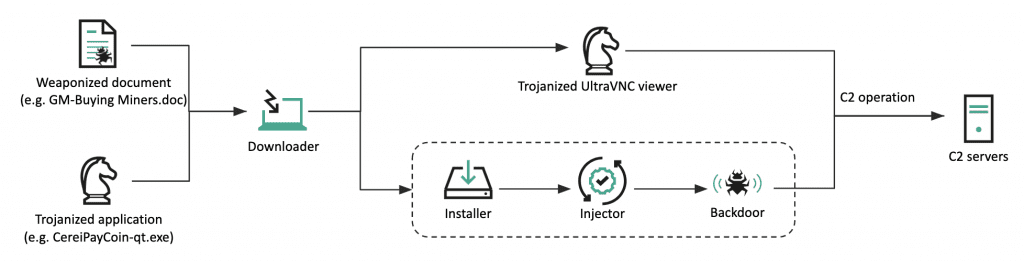
The actor refined its infection chain, using the remote template injection technique in weaponized documents and Trojanized open-source PDF viewer software. Both infection methods result in the DeathNote downloader malware, which uploads victim information and retrieves the next-stage payload at the command-and-control (C2) server’s discretion.
In May 2021, the Lazarus Group compromised an IT company in Europe that provides solutions for monitoring network devices and servers. The group also began utilizing a new infection mechanism against targets in South Korea in early June 2021.

Infection chain | Image: Kaspersky
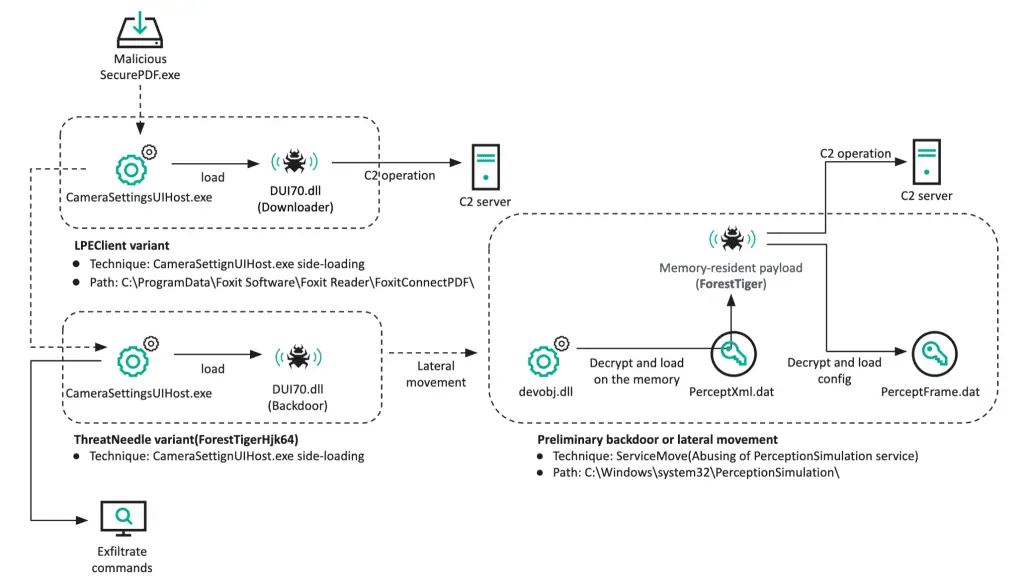
By March 2022, researchers discovered similar downloader malware being propagated to several victims in South Korea, with different payloads delivered in each case. Around the same time, a defense contractor in Latin America was compromised by the same backdoor, using a side-loading technique to execute the final payload.
In July 2022, the Lazarus Group breached a defense contractor in Africa. The initial infection vector was a suspicious PDF application sent via Skype. This attack heavily relied on the same DLL side-loading technique observed in previous cases.
Post-exploitation, the Lazarus Group executed numerous Windows commands to gather basic system information and attempt to find valuable hosts. They acquired Windows credentials using well-known methods and employed public techniques, such as ServiceMove. For data exfiltration, they utilized the WinRAR utility to compress files and transmit them via C2 communication channels.
“Furthermore, we have analyzed the delivery of Windows commands to the victim through the DeathNote malware, and discovered that a significant number of commands were executed between GMT 00:00 and 07:00. Based on our knowledge of normal working hours, we can infer that the actor is located in either the GMT+08 or GMT+09 time zone,” researchers wrote. Moreover, the presence of a Korean comment in the C2 script further supports the hypothesis that Lazarus is a Korean-speaking actor.





