deepce
Docker Enumeration, Escalation of Privileges, and Container Escapes (DEEPCE)
In order for it to be compatible with the maximum number of containers DEEPCE is written in pure sh with no dependencies. It will make use of additional tools such as curl, nmap, nslookup, and dig if available but for the most part, is not reliant upon them for enumeration.
None of the enumerations should touch the disk, however, most of the exploits create new containers which will cause disk writes, and some exploits will overwrite runC which can be destructive, so be careful!

Enumerations
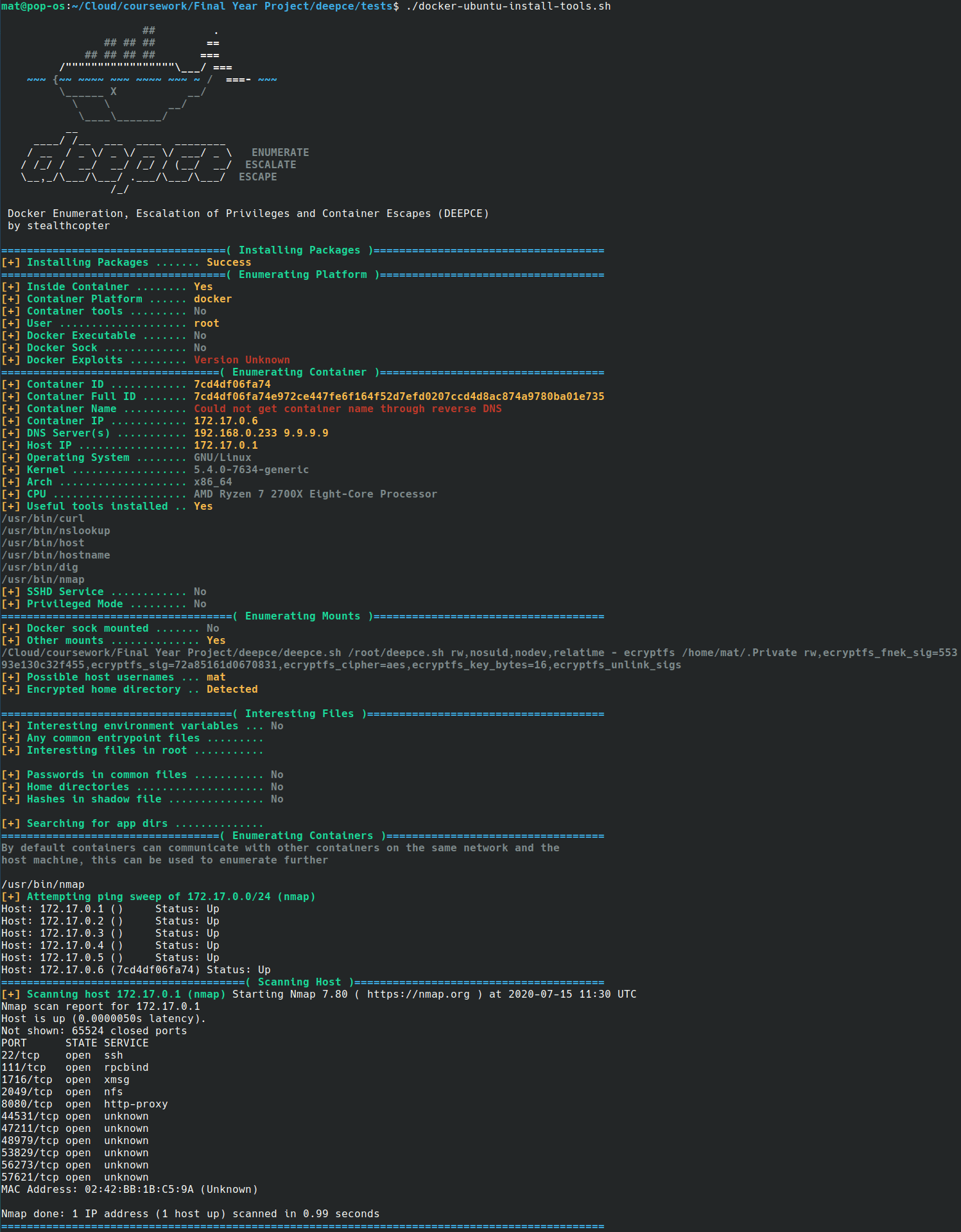
The following is the list of enumerations performed by DEEPCE.
- Container ID & name (via reverse dns)
- Container IP / DNS Server
- Docker Version
- Interesting mounts
- Passwords in common files
- Environment variables
- Password hashes
- Common sensitive files stored in containers
- Other containers on the same network
- Port scan other containers, and the host machine itself
- Find exposed docker sock
Exploits
- Docker Group Privilege Escalation
- Privileged mode host command execution
- Exposed Docker Sock
Payloads
For each of the exploits above payloads can be defined in order to exploit the host system. These include:
- Reverse TCP shell
- Print /etc/shadow
- Add a new root user
- Run custom commands
- Run custom payload binaries
Install & Use
Copyright (C) 2022 stealthcopter