DeepSleep
A variant of Gargoyle for x64 to hide memory artifacts using ROP only and PIC.
Huge thanks to @waldoirc for documenting large parts of this technique on his blog
This implementation is different in that it does not make use of any APCs and is fully implemented as PIC.
Description
I have created this to better understand how to evade memory artifacts using a Gargoyle like technique on x64. The idea is to set up a ROPChain calling VirtualProtect() -> Sleep() -> VirtualProtect() to mark my own page as N/A while Sleeping.
Unlike Gargoyle and other Gargoyle-like implementations, I fully rely on ROP and do not queue any APC. DeepSleep itself is implemented as fully PIC, which makes it easier to enumerate which memory pages have to be hidden from scanners.
While the thread is active, a MessageBox pops up and DeepSleep’s page is marked as executable. While Sleeping, the page is marked as N/A.
This effectively bypasses Moneta at the time of writing if DeepSleep is injected and the executing thread’s base address does not point to private committed memory.
I have verified this using the Earlybird injection technique to inject DeepSleep.bin into notepad.exe

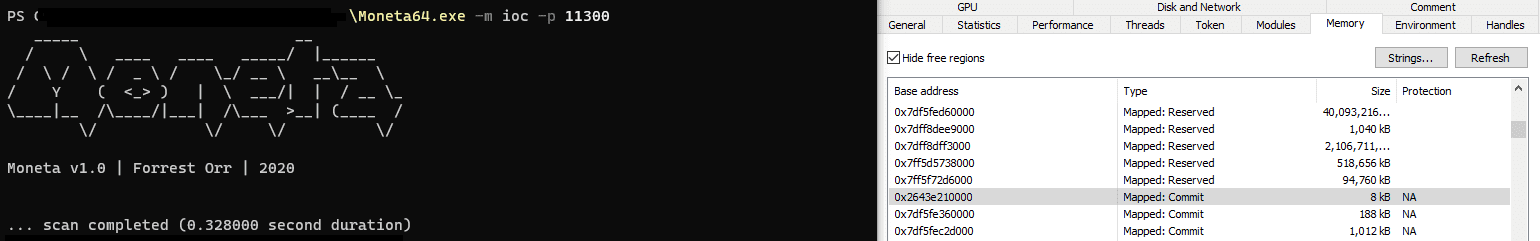
Detection
The callstack to a thread in the DelayExecution state includes unknown/tampered memory regions and additionally includes addresses to VirtualProtect(). Hunt-Sleeping-Beacons detects this.
It may be possible to apply that metric to other C2 using a different technique to wait between callbacks.
Install & Use