Image: Lina Lau
In a recent blog post, Lina Lau, founder and hacker at @xintraorg, shed light on the potential risks of Microsoft Entra ID’s cross-tenant synchronization feature, introduced in March 2023. While this feature was intended to “allow automation of creation, deletion, and updating of Entra B2B collaboration” for seamless multitenant organization management, threat actors are now exploiting it for lateral movement attacks across tenant environments.
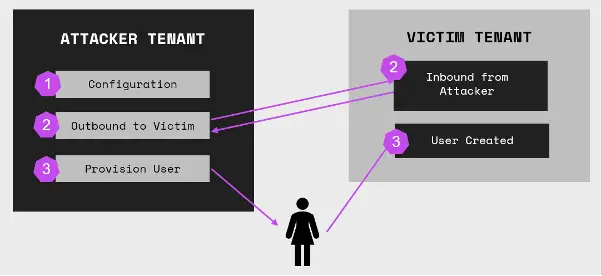
The feature, though useful for legitimate collaboration, has opened a pathway for attackers to infiltrate interconnected tenants. As Lau explains, “Microsoft Entra ID’s cross-tenant synchronization feature allows an attacker the ability to laterally move to a partner tenant,” providing an entry point for an attacker to spread from one compromised tenant to another.
There are two main techniques attackers can exploit: persistence and lateral movement. Lau’s blog post elaborates on how attackers leverage persistence by creating new accounts within compromised tenants. “Once the attacker has been detected by the blue team and has had their account locked out, they can leverage the cross-tenant synchronization feature to provision another malicious account inside the victim tenant.” This mechanism enables attackers to maintain a presence within the tenant environment, even if their initial access is detected and disabled.
For lateral movement, attackers establish cross-tenant synchronization configurations between their own tenant and the victim’s, exploiting permissions such as microsoft.directory/crossTenantAccessPolicy/partners/identitySynchronization/basic/update and microsoft.directory/crossTenantAccessPolicy/partners/create. With these permissions, they configure synchronization to add their account in the victim tenant, allowing them to infiltrate additional tenant networks.
To combat this threat, Lau’s report outlines critical detection steps to identify signs of abuse:
- External Identity Creation: Any creation or update to external cross-tenant settings is logged under the category
CrossTenantAccessSettings, signaling that new access pathways may have been configured. - Modification of Inbound/Outbound Synchronization Settings: Each change in cross-tenant synchronization is marked in logs, enabling defenders to spot unauthorized modifications in access policies.
- Provisioned Malicious User Accounts: Monitoring for new users added through cross-tenant synchronization can reveal the creation of malicious accounts, with logs showing specific details on the targeted tenant and origin of the added user.
- Signs of Lateral Movement: Detection of specific logon events marked with
B2B Collaborationaccess type can indicate cross-tenant movement, a tell-tale sign of attackers leveraging synchronization features for unauthorized access.
While cross-tenant synchronization serves a valuable collaborative role, this blog emphasizes that organizations must closely monitor audit logs and scrutinize user activity within tenant environments. The legitimate use of this feature for B2B collaboration has inadvertently created a conduit for potential attack, requiring vigilant oversight to prevent malicious access and lateral movement across tenants.
Related Posts:
- Microsoft Alerts of Novel SQL Server-Based Lateral Cloud Movement
- Stealthy Persistence: Microsoft Entra ID’s Administrative Units Weaponized
- Phishing for Profits: Attackers Mine Crypto & Spam Through OAuth Apps