Developers Targeted: North Korean Hackers Deploy “BeaverTail” Malware via NFTs
eSentire’s Threat Response Unit (TRU) uncovers a sophisticated phishing campaign using a fake NFT project to lure unsuspecting software developers.
In a recent report, eSentire’s Threat Response Unit (TRU) has exposed a new tactic employed by North Korean threat actors, dubbed “Contagious Interview.” This campaign uses a fraudulent NFT marketplace project, the “Bored BeaverTail Yacht Club,” to distribute malware known as BeaverTail.
The attack begins with a seemingly innocuous invitation to explore the NFT project, likely through phishing emails or LinkedIn messages. “Due to data retention, it is not obvious what prompted the user to visit the project. Based on the detection, as well as other campaign reporting, it was likely from a phishing email or LinkedIn interview follow-up,” the report states. This approach specifically targets software developers, a community often engaged in exploring new technologies and platforms, including NFTs.
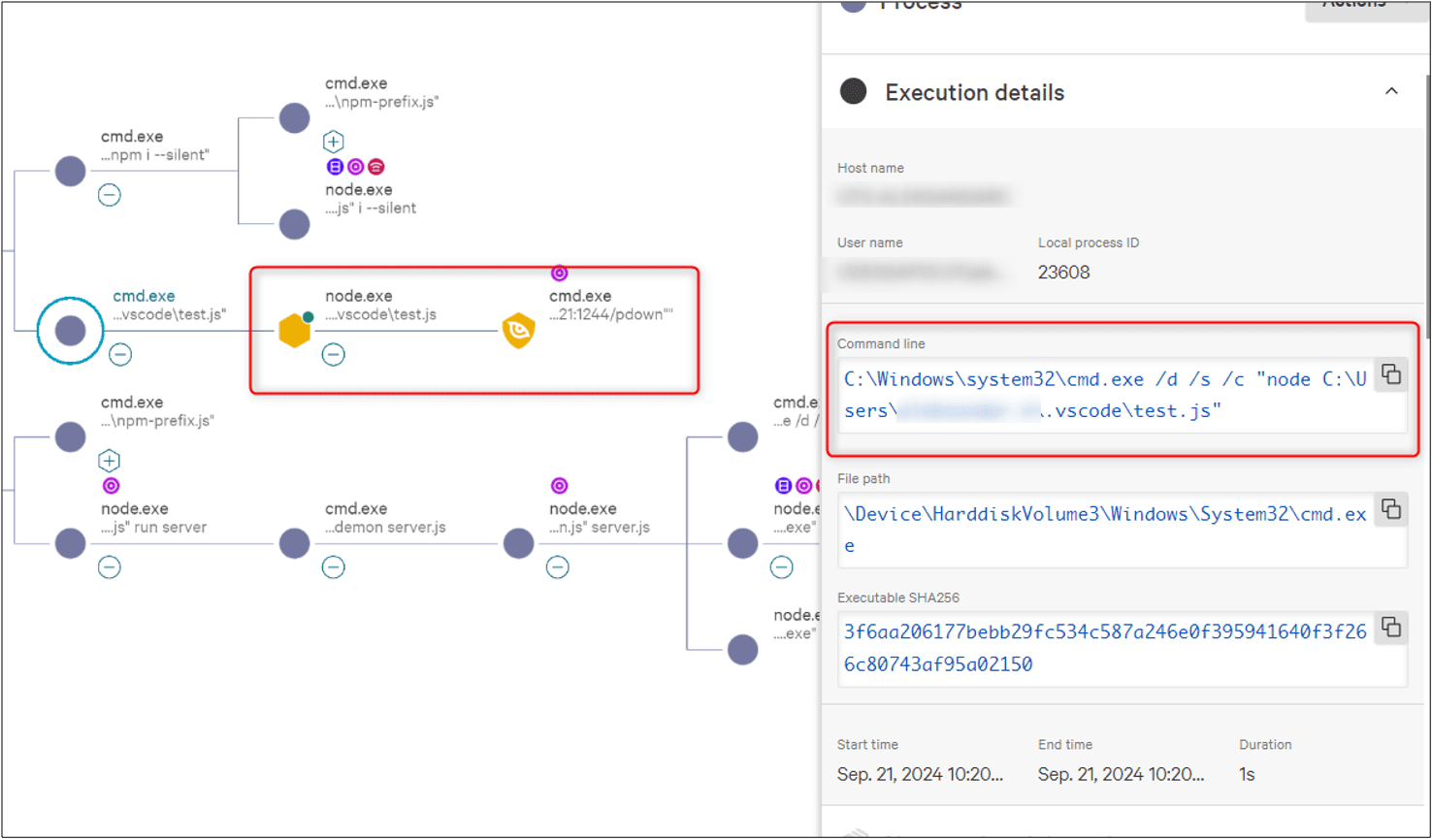
Once the victim downloads the malicious project from a GitHub repository, the BeaverTail malware attempts to download and execute a Python-based backdoor known as Invisible Ferret. This backdoor allows the attackers to gain extensive control over the victim’s system, potentially leading to data theft, and espionage, including the InvisibleFerret backdoor or further malicious activities.
“We did not observe InvisibleFerret deploy, however, we assess the chances as probable that InvisibleFerret components for fingerprinting the infected device were hidden inside the .npl script,” the TRU report stated.
eSentire’s investigation revealed that the tactics, techniques, and procedures (TTPs) used in this attack strongly aligned with those of North Korean threat actors, specifically the Lazarus Group, also tracked as “Contagious Interview.” The Lazarus Group is notorious for targeting software developers and cryptocurrency platforms, often using lures like fake job offers or NFT projects. “The observed incident involved a GitHub project related to NFT and cryptocurrency, another common trait with North Korean threat actors,” the report highlighted.
eSentire’s TRU team emphasizes the importance of vigilance and caution when interacting with unsolicited project invitations or links, even if they appear to be from trusted sources. Developers are advised to carefully scrutinize the authenticity of any project before downloading or installing associated files.





