
Cyble Research and Intelligence Labs (CRIL) has uncovered an ongoing cyber campaign targeting German organizations using sophisticated tactics like DLL sideloading, proxying, and the deployment of the Sliver implant, an open-source red-teaming framework adapted for malicious purposes.
The attack begins with a spear-phishing email containing a compressed archive file named Homeoffice-Vereinbarung-2025.7z. Once extracted, the archive reveals a deceptive shortcut (LNK) file alongside other hidden components, including:
- Malicious and legitimate DLLs
- Encrypted shellcode in a DAT file
- A decoy PDF file mimicking a legitimate remote work agreement.
The lure document is a Home Office Agreement written in German, serving as a supplementary agreement to an existing employment contract, targeting organizations in Germany.
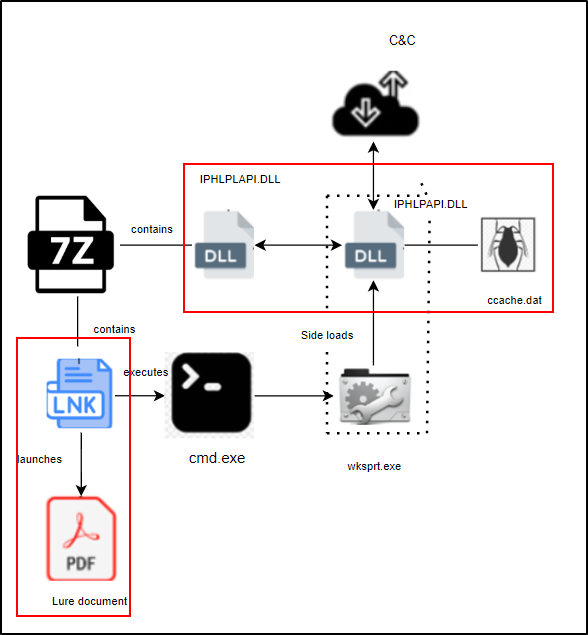
The LNK file, disguised as a PDF, triggers cmd.exe to copy files into a newly created directory, %localappdata%\InteI. It executes wksprt.exe, a legitimate Windows executable, to sideload the malicious IPHLPAPI.dll.
The malicious DLL forwards legitimate function calls to a renamed authentic DLL, IPHLPLAPI.dll, ensuring normal application behavior while executing its malicious payload. The malicious DLL decrypts shellcode stored in the DAT file using cryptographic APIs like CryptAcquireContextW and CryptDecrypt, eventually deploying the Sliver implant.
The implant connects to remote servers hosted at domains like technikzwerg[.]de, enabling the attackers to execute further malicious operations.
CRIL’s analysis suggests similarities with APT29’s tactics, known for using DLL sideloading in previous campaigns. However, the addition of DLL proxying represents a novel evolution.
The campaign’s multi-stage approach, coupled with its focus on evasion, poses challenges for traditional detection systems. However, CRIL has released Yara and Sigma rules to assist in identifying malicious activity, available on their GitHub repository.
The Sliver implant campaign targeting German organizations demonstrates the increasing sophistication of threat actors. CRIL emphasizes, “By employing advanced evasion techniques such as DLL sideloading, DLL proxying, shellcode injection, and the Sliver framework, the attackers effectively bypass traditional security measures.”
Related Posts:
- Python Developers Beware: Attackers Sneak Malware into Popular Package Manager
- Trusted Name Weaponized: Sliver and Ligolo-ng Attack Leverages Y Combinator Brand
- Quasar RAT: Stealthy Data Extraction via DLL Sideloading
- TeamTNT’s “Docker Gatling Gun” Campaign Targets Exposed Cloud Environments with New Sliver Malware