dns rebind toolkit: JavaScript toolkit for creating DNS rebinding attacks
DNS Rebind Toolkit
DISCLAIMER: This software is for educational purposes only. This software should not be used for illegal activity. The author is not responsible for its use. Don’t be a dick.
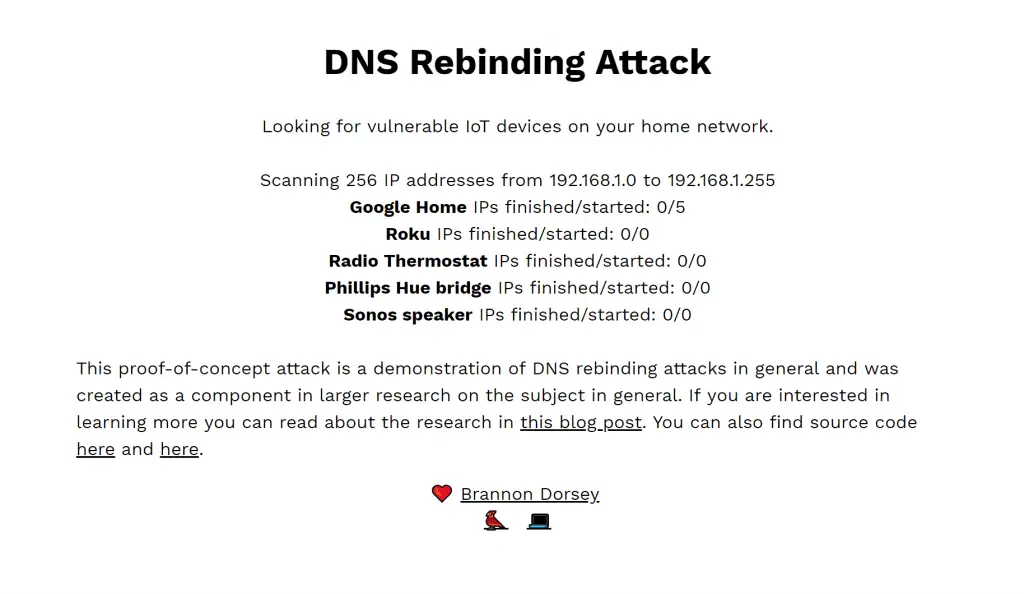
DNS Rebind Toolkit is a frontend JavaScript framework for developing DNS Rebinding exploits against vulnerable hosts and services on a local area network (LAN). It can be used to target devices like Google Home, Roku, Sonos WiFi speakers, WiFi routers, “smart” thermostats, and other IoT devices. With this toolkit, a remote attacker can bypass a router’s firewall and directly interact with devices on the victim’s home network, exfiltrating private information and in some cases, even controlling the vulnerable devices themselves.

The attack requires a victim on the target network to simply follow a link, or be shown an HTML ad containing a malicious iframe. From their, the victim’s web browser is used as a proxy to directly access other hosts connected to their home network. These target machines and services would otherwise be unavailable to the attacker from the Internet. The remote attacker may not know what those services are, or what IP addresses they occupy on the victim’s network, but DNS Rebind Toolkit handles this by brute forcing hundreds of likely IP addresses.
Under the hood, this tool makes use of a public whonow DNS server running on rebind.network:53 to execute the DNS rebinding attack and fool the victim’s web browser into violating the Same-origin policy. From their, it uses WebRTC to leak the victim’s private IP address, say 192.168.1.36. It uses the first three octets of this local IP address to guess the network’s subnet and then inject 256 iframes, from 192.168.1.0-255 delivering a payload to each host that could possibly be on the network subnet.
This toolkit can be used to develop and deploy your own DNS rebinding attacks. Several real-world attack payloads are included with this toolkit in the payloads/ directory. These payloads include information exfiltration (and rickroll tom-foolery) attacks against a few popular IoT devices, including Google Home and Roku products.
Copyright (c) 2018 Brannon Dorsey <brannon@brannondorsey.com>





