docem
Utility to embed XXE and XSS payloads in docx,odt,pptx, etc – any documents that are a zip archive with a bunch of xml files inside
This tool is a side-project of collaborative research of the document’s internal structure with ShikariSenpai and ansjdnakjdnajkd
Features and ToDo
- Features
- Read file with payloads
- XXE custom payload file
- XSS payload file
- Read file with payloads
- ToDo
- Add the ability to embed not only in xml but in unzip file also
- Add a flag to specify custom url to use in XXE
- Add a flag to specify custom url to use in XSS
What it is all about
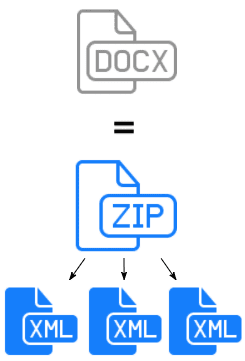
A lot of common document formats, such as doc,docx,odt, etc is just a zip file with a few xml files inside
So why not embed XXE payloads in them?
That was done by great research by Will Vandevanter (_will_is) To create such documents with embedded payloads there is a famous tool called oxml_xxe.
But. It is not convinient to use oxml_xxe when you need to create hundreds of documents with payloads in different places. So there it goes – Docem.
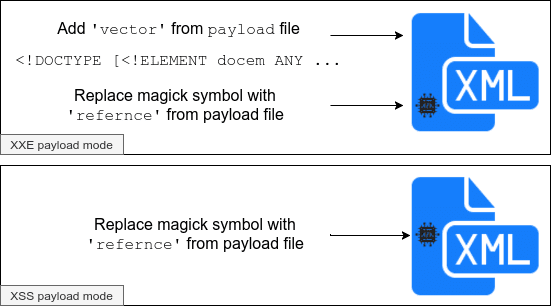
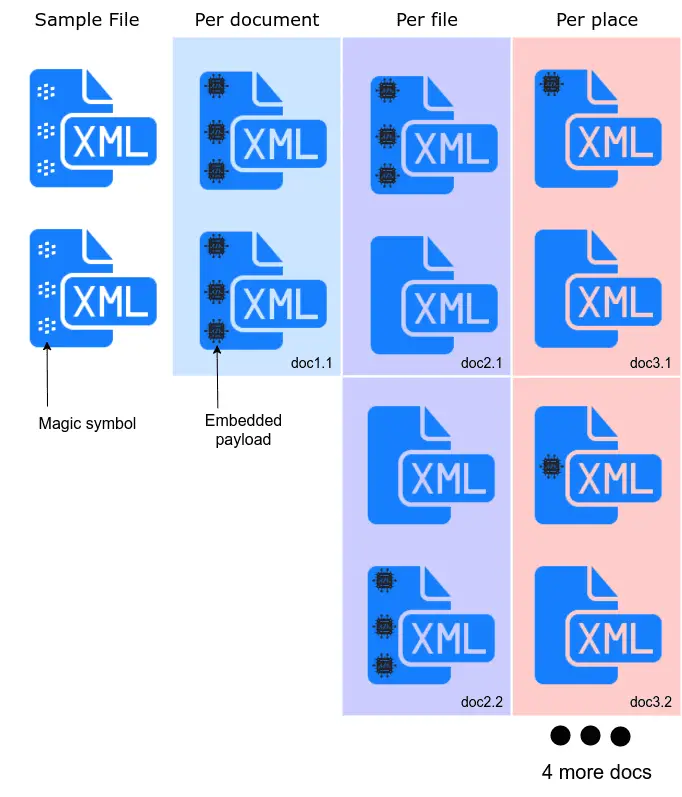
It works like that: You specify sample document – that is a doc that has some magic_symbols (in this case it is ፨) that will be replaced by your refernce to a payload in case of XXE payload or will be replaced by your XSS payload.
Also, there are three different types of payload_type – every type determines how every magic_symbol will be processed for a given file in a document. Every payload_type described in section Usage. Here is a small scheme of how this works:
Payload modes
Programm interface
Changelog v1.5
- Code has been heavily refactored.
- Samples have been checked and improved.
- Tool can be easily extended and upgraded.
- The core functionality remained the same.
Install
git clone https://github.com/whitel1st/docem.git
cd docem
pip3 install -r requirements.txt
Usage Docem
python3 docem.py --help
- required args
-s– path to asample fileor asample directory-pm– payload modexss– XSS – Cross-Site Scriptingxxe– XXE – External XML Entity
- optional
-pt– payload typeper_document– (default mode) for every payload, embed payload in all places in all files and create a new docper_file– for every payload, for every file inside a document, for all places inside file embed payload and create a new docper_place– for every payload, for every place in every file, embed payload and create a new doc
-pf– payload file-kt– do not delete temp folders in tmp-sx– sample extension – used when a sample is a directory-h– print help
Examples
./docem.py -s samples/xxe/sample_oxml_xxe_mod0/ -pm xss -pf payloads/xss_all.txt -pt per_document -kt -sx docx
./docem.py -s samples/xxe/sample_oxml_xxe_mod1.docx -pm xxe -pf payloads/xxe_special_2.txt -kt -pt per_place
./docem.py -s samples/xss_sample_0.odt -pm xss -pf payloads/xss_tiny.txt -pm per_place
./docem.py -s samples/xxe/sample_oxml_xxe_mod0/ -pm xss -pf payloads/xss_all.txt -pt per_file -kt -sx docx
How to create a custom sample
Via new file
- Extract your document example.docx
- Add magic symbols –
፨(yes, literally – those fancy 5 dots) in places where you want payloads to be embedded - Zip your new sample into example_modified0.zip
- Rename extension – example_modified0.docx
- Use a new sample with a tool
File with payloads format
Small documentation to add your custom payloads
XXE payloads
Special format
String from a file
{“vector”:”<!DOCTYPE docem [<!ENTITY xxe_canary_0 \”XXE_STRING\”>]>”,”reference”:”&xxe_canary_0;”}
- vector – required keyword – script will be searching for it
- <!DOCTYPE docem [<!ENTITY xxe_canary_0 \”XXE_STRING\”>]> – payload. Warning all double quotation marks “ must be escaped with one backslash \ => \”
- reference – required keyword – script will be searching for it
- &xxe_canary_0; – a reference that will be added in all places with magic symbol
XSS payloads
No special format. Just a file with strings. As if you would use it in any other tool.
Source: https://github.com/whitel1st/