
“What if you received an email stating, ‘YOUR ADS ARE TEMPORARILY SUSPENDED’? The urgency of the email instantly grabs your attention… hoping to get it fixed promptly.”
In the digital world of likes, follows, and ad conversions, a single email can unravel your entire marketing infrastructure. That’s exactly what a sophisticated phishing campaign discovered by the Cofense Phishing Defense Center (PDC) is exploiting — with fake Meta emails, deceptive chatbots, and even counterfeit support agents.
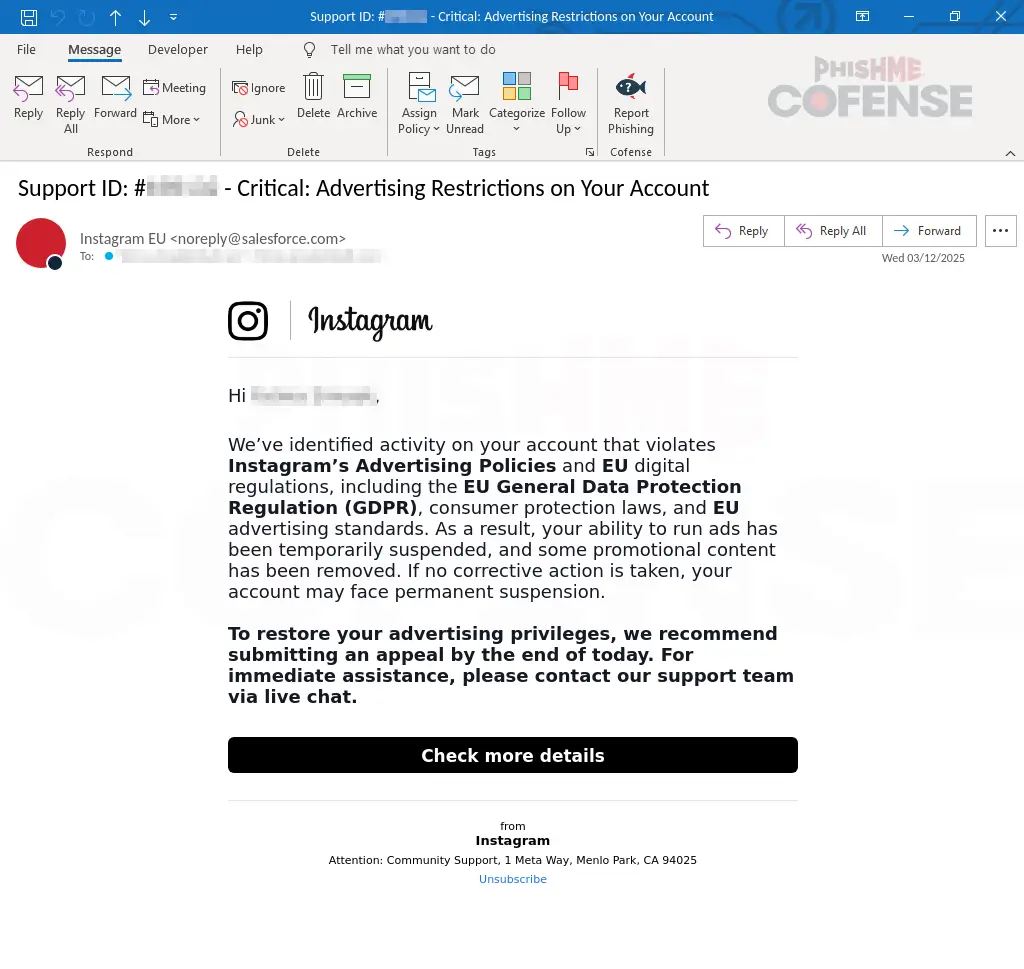
The campaign begins with an urgent email disguised as a Meta/Instagram alert, complete with subject lines like:
“Support ID: #xxxx – Critical Advertising Restrictions on Your Account”
This phishing email plays on fear — warning that ad accounts have violated EU GDPR or Meta’s ad policies. Victims are encouraged to click a “Check More Details” button, which leads to a legitimate-looking fake Meta page.
But there’s a clue: the sender address isn’t official — it’s noreply@salesforce[.]com, not a Meta-owned domain.
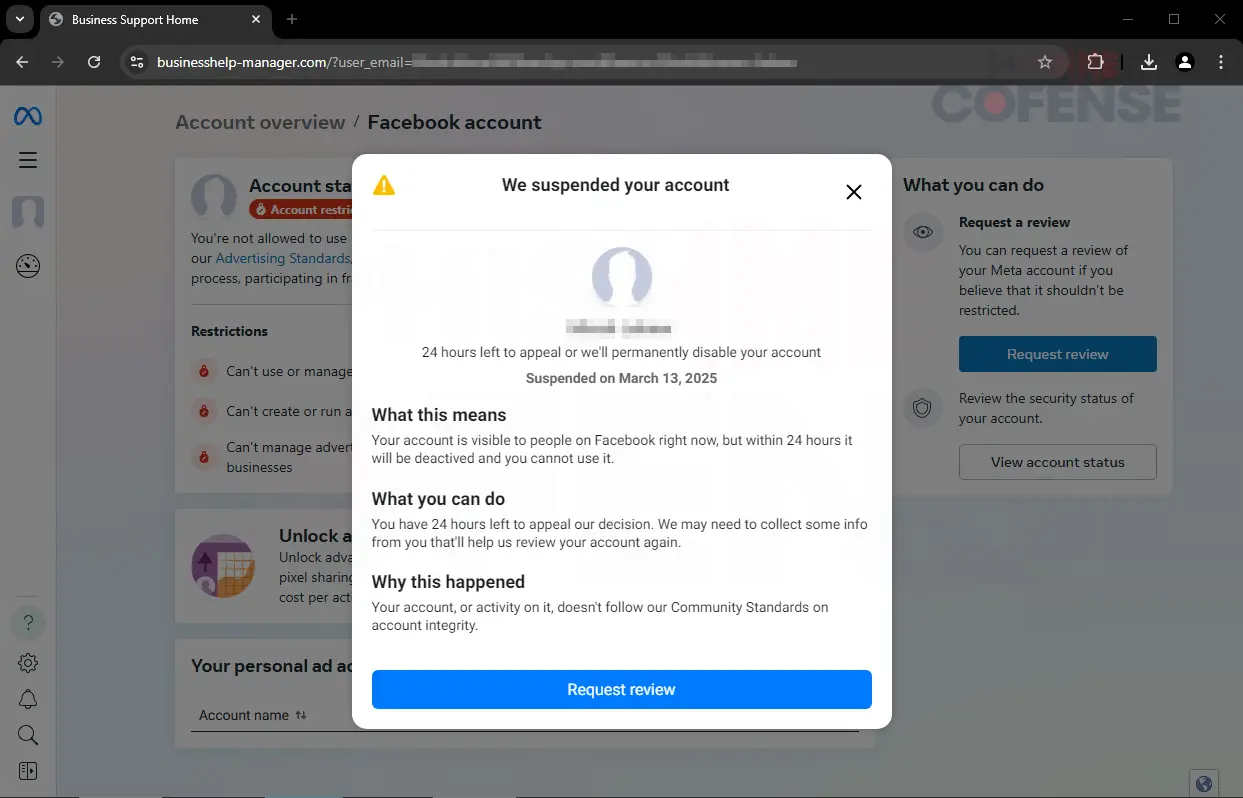
Once on the fake landing page (businesshelp-manager[.]com), victims see a warning that their account may face termination. From there, they’re guided toward a “Request Review” option.
“Comparing this to a legitimate Meta Business page, most people will think there isn’t anything out of the ordinary.”
Victims are asked to chat with a support chatbot — seemingly helpful, but 100% malicious. The chatbot requests:
-
Business name
-
Screenshots of Facebook Business settings
-
Contact number
-
Personal profile information
“The attacker even asks for screenshots… perhaps as a way of screening victims.”
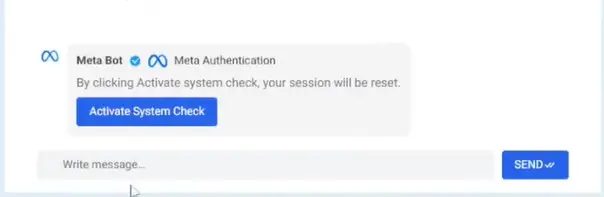
Eventually, the victim is told to run a “System Check” — a euphemism for giving the attacker Two-Factor Authentication (2FA) access via their own Authenticator app.
“The attacker aims to hijack Business Meta accounts by registering themselves as a ‘Secure Login’ via the Authenticator App feature of Meta.”
If users don’t fall for the chatbot, the attacker has a Plan B — a DIY-style “setup guide” that leads victims to the same endpoint: handing over control.
The attack culminates with a password prompt after clicking “Activate System Check.”
“The page reloads and asks the user to enter their Facebook password.”
Once entered, the attacker can:
- Bypass email recovery
- Lock the real user out
- Run ads from the compromised business page
- Steal audience data, post scams, or worse
“The inclusion of live agent support adds an additional layer of deception, making users believe they are interacting with Meta’s official support team.”
Phishing isn’t just about shady links anymore. Today’s attackers are brand impersonation experts, crafting convincing experiences across email, web, and support.
Stay alert. Stay skeptical. And always double-check before you click.
Related Posts:
- Cybercriminals Escalate Attacks with Sophisticated HR-themed Phishing Scam
- Meta’s AI Push: From Llama to Chatbot, Subscription Model Coming
- Phishing Campaign Bypasses MFA to Target Meta Business Accounts, Putting Millions at Risk
- Amazon Prime Phishing Scam Steals Login, Payment Info
- Copilot Phishing: New Scam Targets Microsoft Users