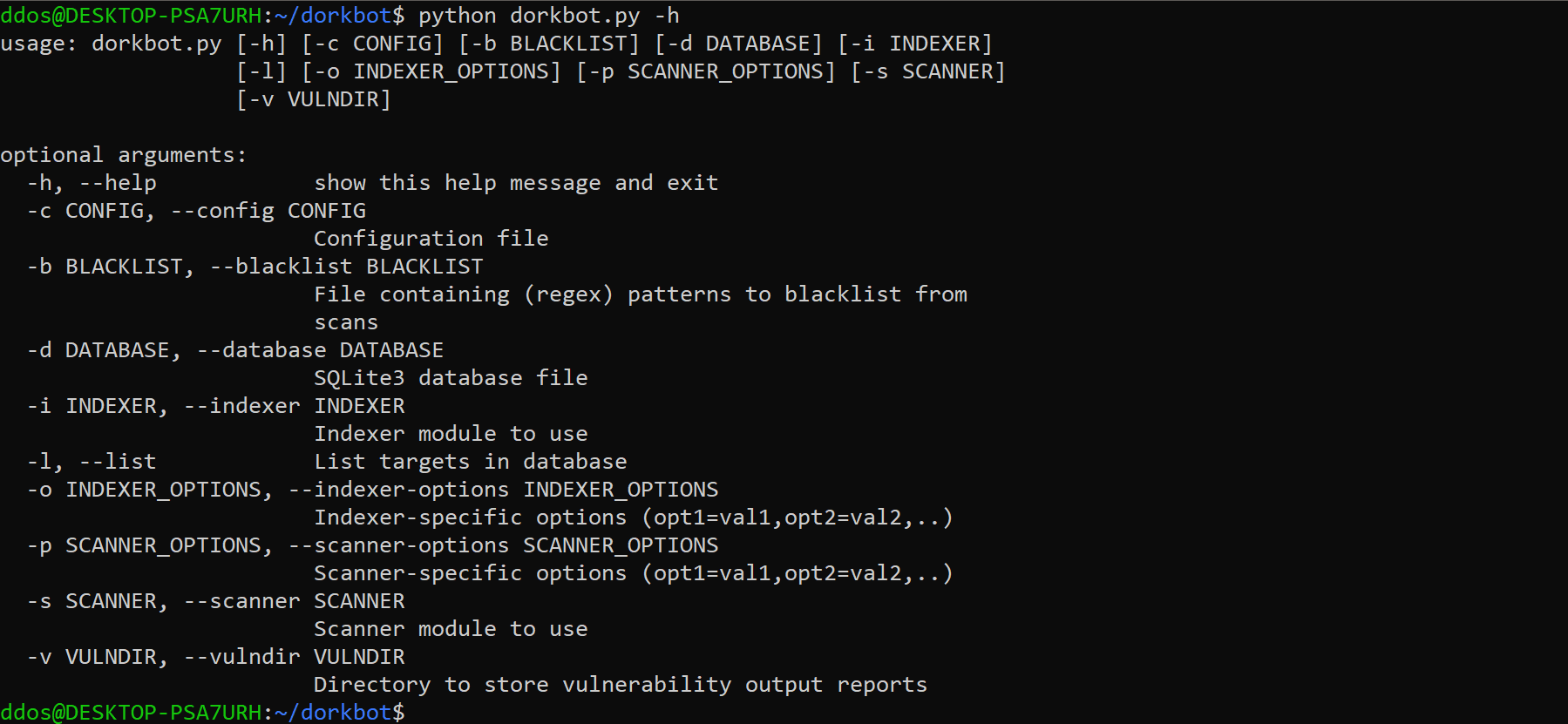
dorkbot v0.0.5 releases: Command-line tool to scan Google search results for vulnerabilities
dorkbot
Scan Google search results for vulnerabilities.
dorkbot is a modular command-line tool for performing vulnerability scans against a set of web pages returned by Google search queries in a given Google Custom Search Engine. It is broken up into two sets of modules:
- Indexers – modules that issue a search query and return the results as targets
- Scanners – modules that perform a vulnerability scan against each target
 Targets are stored in a local database file upon being indexed. Once scanned, any vulnerabilities found by the chosen scanner are written to a standard JSON report file. Indexing and scanning processes can be run separately or combined in a single command.
Targets are stored in a local database file upon being indexed. Once scanned, any vulnerabilities found by the chosen scanner are written to a standard JSON report file. Indexing and scanning processes can be run separately or combined in a single command.
Download
git clone https://github.com/utiso/dorkbot.git
Use
Tools
As needed, dorkbot will search for tools in the following order:
- Directory specified via relevant module option
- Located in dorkbot’s tools directory, with the subdirectory named after the tool
- Available in the user’s PATH (e.g. installed system-wide)
Quickstart
Create a Google Custom Search Engine and note the search engine ID, e.g. 012345678901234567891:abc12defg3h. Download either Arachni or Wapiti, unpack it into the tools directory, and rename the subdirectory to arachni or wapiti as appropriate.
Indexer Modules
Search for targets in a Google Custom Search Engine (CSE) via custom search element.
Requirements: PhantomJS
Options:
- engine – CSE id
- query – search query
- phantomjs_dir – phantomjs base directory containing bin/phantomjs (default: tools/phantomjs/)
- domain – limit searches to specified domain
google_api
Search for targets in a Google Custom Search Engine (CSE) via JSON API.
Requirements: none
Options:
- key – API key
- engine – CSE id
- query – search query
- domain – limit searches to a specified domain
cc_py
Search for targets within commoncrawl.org results via cc.py.
Requirements: cc.py
Options:
- domain – pull all results for given domain or subdomain
- cc_py_dir – cc.py base directory containing the file cc.py (default: tools/cc.py/)
- year – limit results to data sets from a given year (17 or 18, defaults to all)
bing_api
Search for targets via Bing Web Search API.
Requirements: none
Options:
- key – API key
- query – search query
stdin
Read targets from standard input, one per line.
Requirements: none
Options: none
Scanner Modules
Scan targets with Arachni command-line scanner.
Requirements: Arachni
Options:
- arachni_dir – arachni base directory containing bin/arachni and bin/arachni_reporter (default: tools/arachni/)
- report_dir – directory to save arachni scan binary and JSON scan report output (default: reports/)
- checks – space-delimited list of vulnerability checks to perform (default: “active/* -csrf -unvalidated_redirect -source_code_disclosure -response_splitting -no_sql_injection_differential”)
wapiti
Scan targets with Wapiti command-line scanner.
Requirements: Wapiti
Options:
- wapiti_dir – wapiti base directory containing bin/wapiti (default: tools/wapiti/)
- report_dir – directory to save wapiti JSON scan report (default: reports/)
Copyright © 2017, The University of Texas at Austin. All rights reserved.
Source: https://github.com/utiso/





