DPAT: Domain Password Audit Tool for Pentesters
Domain Password Audit Tool (DPAT)
This is a python script that will generate password use statistics from password hashes dumped from a domain controller and a password crack file such as oclHashcat.pot generated from the oclHashcat tool during password cracking. The report is an HTML report with clickable links.
You can run the python script as follows.
Note that the group lists at the end (-g “Domain Admins.txt “Enterprise Admins.txt”) are optional. Try this out on the example files provided in the sample_data folder of this project. The sample data was built from census data for common first and last names and passwords from the well-known rockyou list.
You can get this file by first dumping the password hashes from your domain controller by executing the following command in an administrative command prompt on a domain controller. Just make sure you have enough disk space to store the output in c:\temp. The amount of space needed will be slightly larger than the size of the ntds.dit file that is currently on the disk, as this performs a backup of that file and some registry settings.
ntdsutil “ac in ntds” “ifm” “cr fu c:\temp” q q
You can then turn this output into the needed format using secretsdump.py
secretsdump.py -system registry/SYSTEM -ntds Active\ Directory/ntds.dit LOCAL -outputfile customer
The command above will create a file called “customer.ntds” which you will use with this tool as well as for password cracking.
Your Hashcat file should be in this format (which is the default output of the Hashcat):
nthash:password
Or for LM Hashes:
lmhashLeftOrRight:leftOrRightHalfPasswordUpcased
The DPAT tool also supports output from John the Ripper (the same format as hashcat.potfile but prepended with $NT$ or $LM$)
The optional “-g” option is followed by a list of any number of files containing lists of users who are in the given group such as “Enterprise Admins” or “Domain Admins”. The file can be in the format output by the PowerView PowerShell script as shown in the example below:
Get-NetGroupMember -Recurse -GroupName “Domain Admins” > “Domain Admins.txt”
or to read a group from another domain use something like the following (note that name of the other domain and the domain controller can be obtained with Get-NetForestDomain)
Get-NetGroupMember -Recurse -GroupName “Enterprise Admins” -Domain “some.domain.com” -DomainController “DC01.some.domain.com” > “Enterprise Admins.txt”
Alternatively, the group files can simply be a list of users, one per line, in the following format:
domain\username
The Domain Password Audit Tool also has the handy feature to finish cracking the LM hashes for any hashes where the NT hash was not cracked. This asssumes that you have used Hashcat to brute force all 7 character passwords with the following command:
./hashcat.bin -m 3000 -a 3 customer.ntds -1 ?a ?1?1?1?1?1?1?1 –increment
Download
Usage
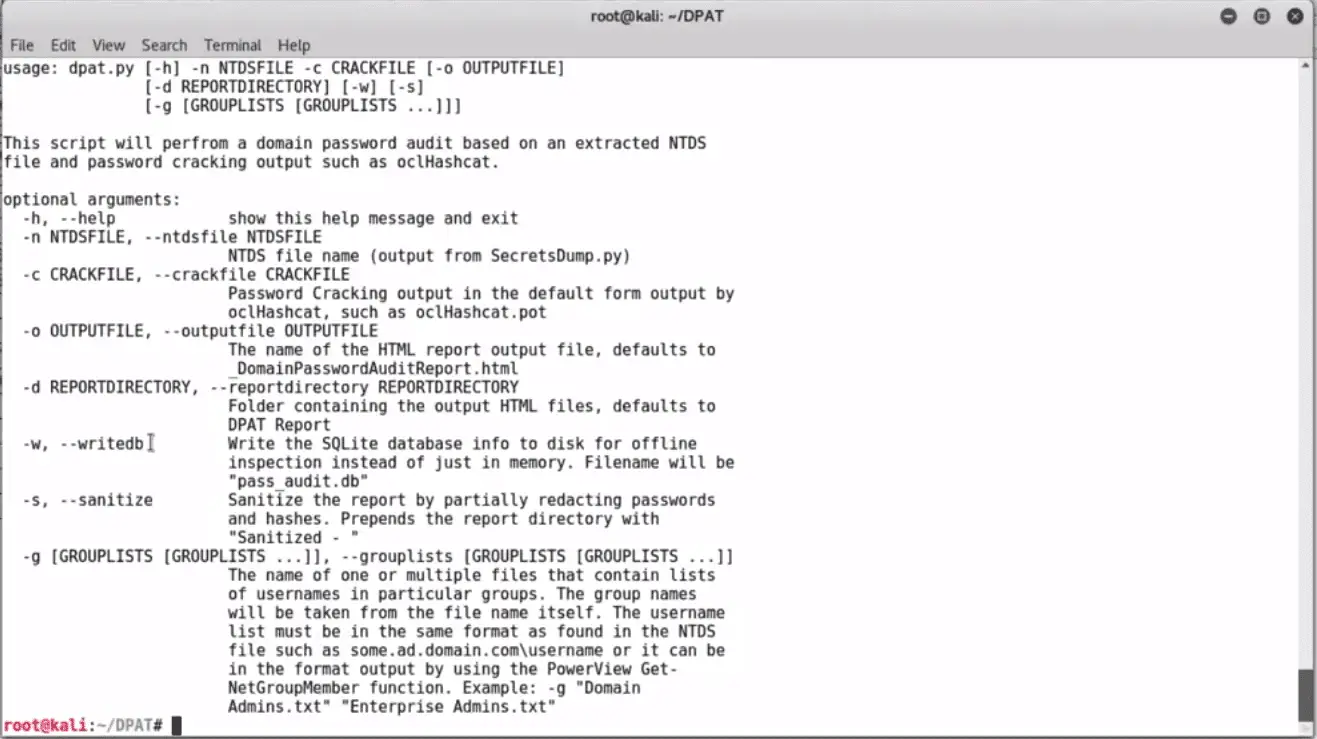
To see all available DPAT options use the ‘-h’ or ‘–help’ option