Antivirus company Dr.Web’s security experts discovered three new Android Trojans in the Google Play store last week. They were detected as Android.Click.415, Android.Click.416 and Android.Click.417 respectively.
The malicious application used to spread the Trojan horse pretends to be a legitimate Android application. After installation, it can accept the command of the attacker to load and display any web page. According to Dr.Web’s security experts, this feature can be used to launch phishing attacks.
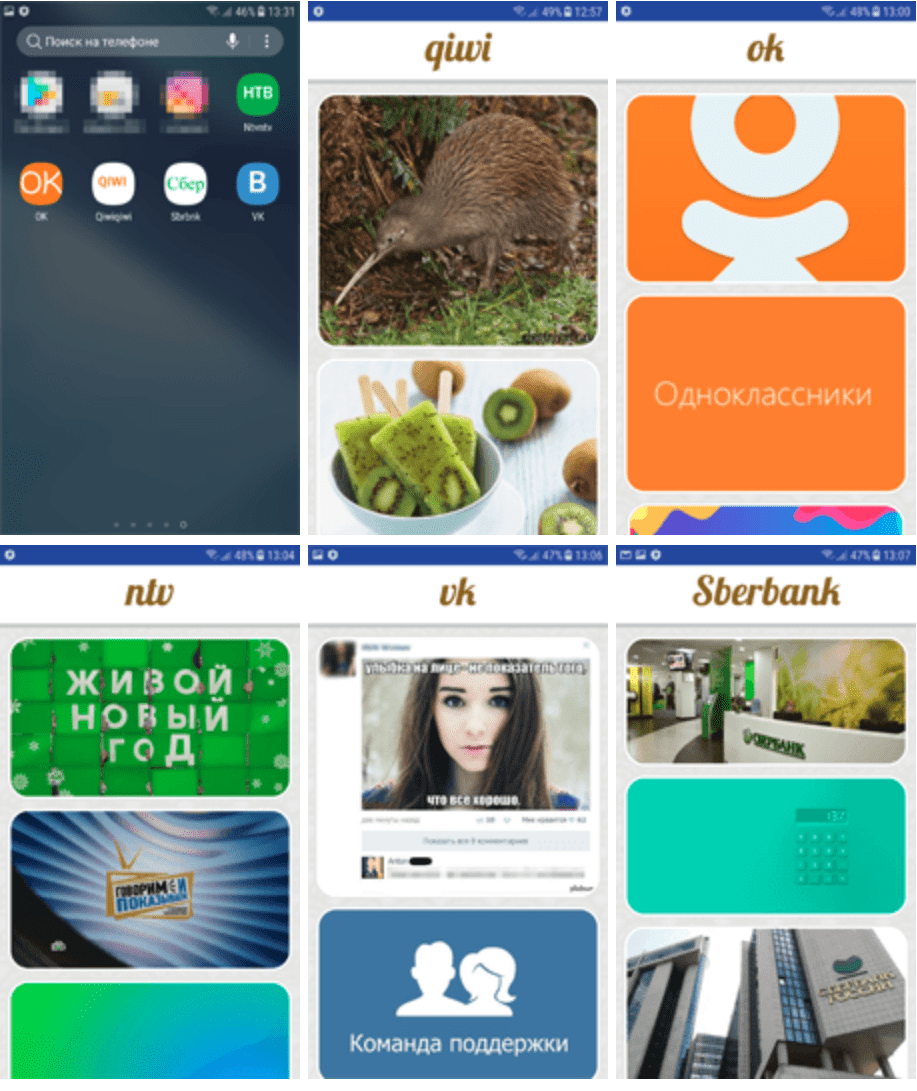
Security experts said that the detected malicious application has the same name and similar icon as the legitimate application. Take Android.Click.415, the malicious application used to spread the Trojan has imitated several popular legitimate Android applications, such as QIWI app (Russian payment service provider), Odnoklassniki and VK (Russian popular social network) and NTV. (Russian Independent Television Station). On the left is the description page of the malicious application in the Google Play Store, and on the right is the description page of the legitimate application:

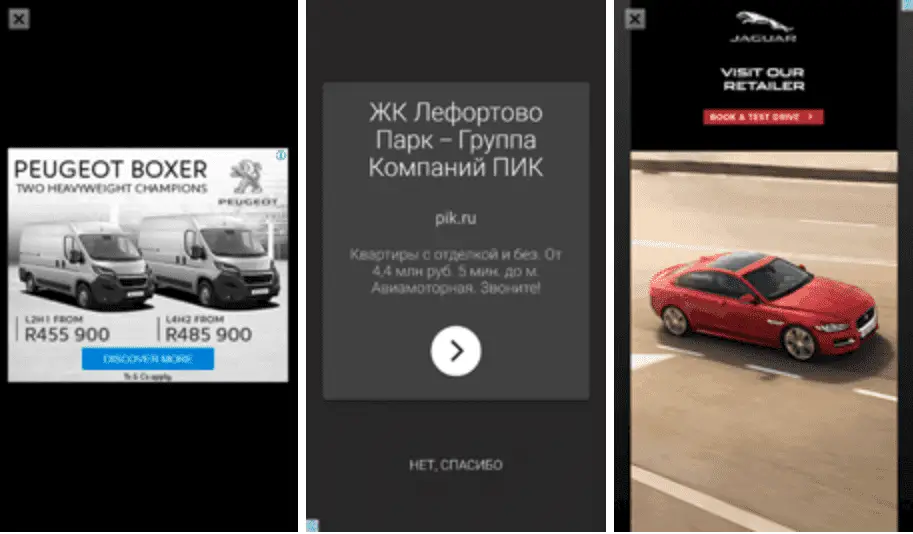
Each time a malicious application launches, it connects to a command and control (C&C) server. The server responds to the “none” parameter or sends a web page link specified by the attacker. When a parameter is received, the malicious application extracts multiple images from its resources and displays it to the victim.

If a malicious application receives a web page link from a C&C server, they will load the web page and display it. Then, open the page directly in the application via WebView. In this case, these web pages may be fake login interfaces for some online banking systems or social networks, which exposes victims to the risk of phishing attacks.
Next, let’s take a look at how Trojan horses detected as Android.Click.416 and Android.Click.417 work.
Dr.Web’s security experts discovered a total of more than 70 malicious applications for the spread of the two Trojans, with over 270,000 downloads. Similar to the malicious applications that spread Android.Click.415, they are also disguised as legitimate Android applications. These applications may be some mobile games, recipes, and weaving manual applications.
Like Android.Click.415, after establishing a foothold on the victim device, Android.Click.416 and Android.Click.417 will also display any web page by accepting a command response from the C&C server.
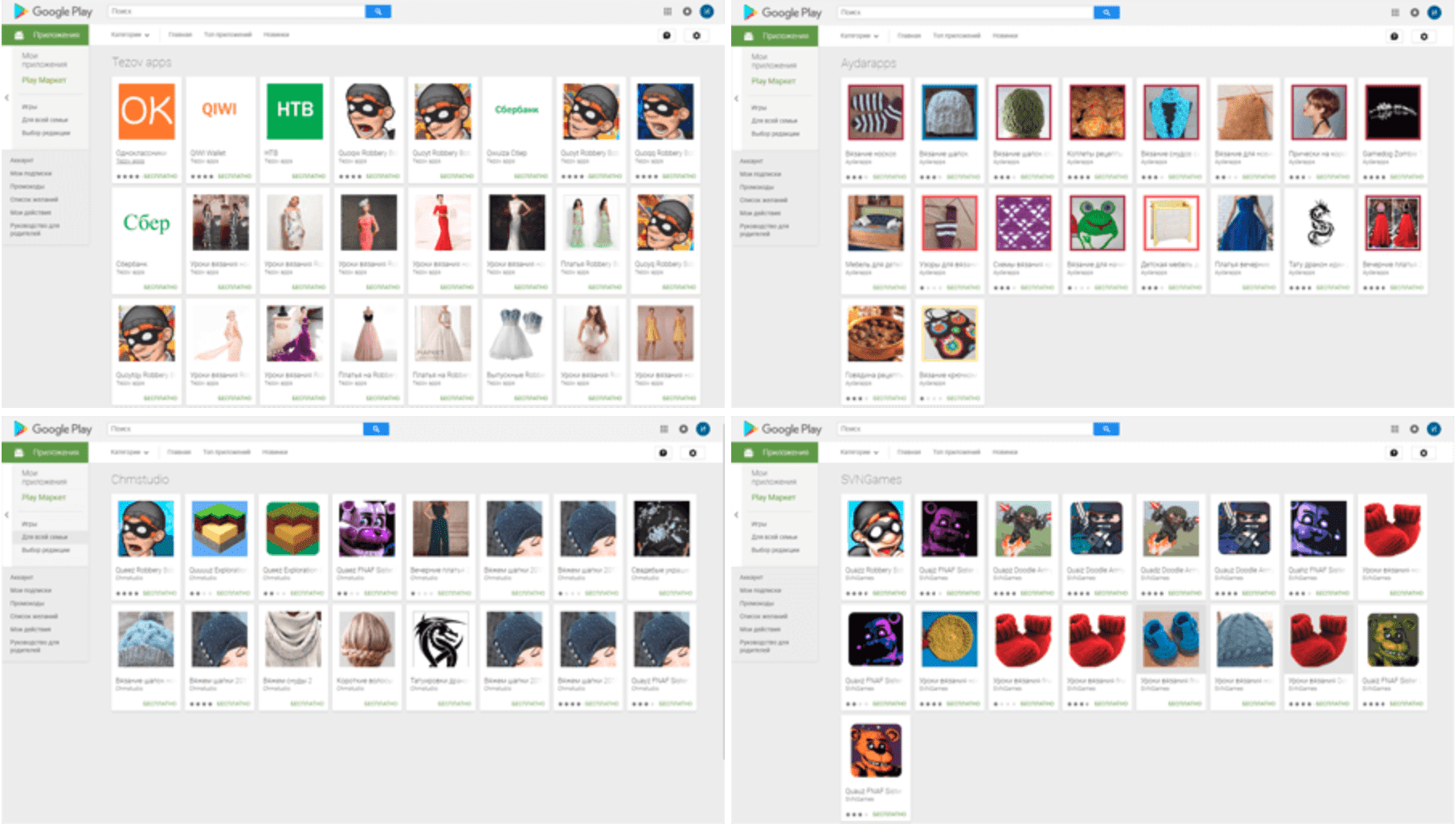
 In addition, in the discovery of Dr.Web security experts, at least four software developers participated in the distribution of these Trojans. Their usernames on the Google Play Store are Tezov apps, Aydarapps, Chmstudio, and SVNGames.
In addition, in the discovery of Dr.Web security experts, at least four software developers participated in the distribution of these Trojans. Their usernames on the Google Play Store are Tezov apps, Aydarapps, Chmstudio, and SVNGames.
Dr.Web has already communicated these findings to the Google team and also reminded users that even if they download applications from a reliable source such as the Google Play Store, they also need to pay attention to the name of the software developer and the comments under the software description.
Source, Image: drweb