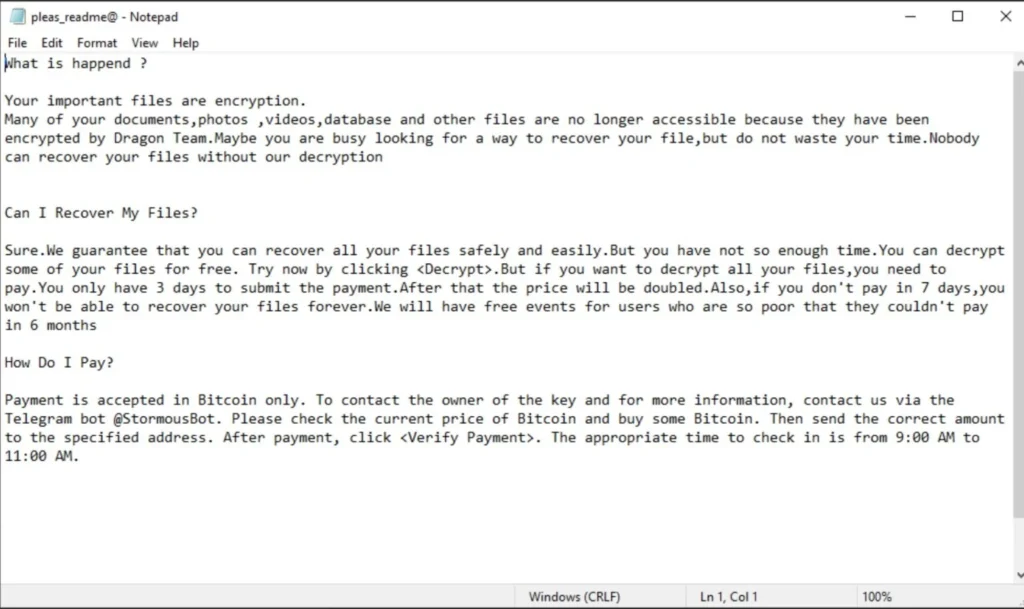
Dragon Team ransom note | Image: SentinelOne
A new Ransomware-as-a-Service (RaaS) player is carving out its niche in the ever-evolving threat landscape. Known as Dragon RaaS, or simply Dragon Team, this emerging group blends political hacktivism with opportunistic cybercrime — all while operating under the shadowy umbrella of “The Five Families” cybercrime syndicate.
Dragon RaaS first emerged in July 2024 as a splinter group from Stormous, a notorious pro-Russian ransomware gang known for its geopolitically motivated attacks. As part of the crimeware cartel known as “The Five Families,” Dragon RaaS is closely affiliated with ThreatSec, GhostSec, Blackforums, and SiegedSec.
“While Dragon RaaS markets itself as a sophisticated Ransomware-as-a-Service (RaaS) operation,” SentinelOne reports, “its attacks are often defacements and opportunistic rather than large-scale ransomware extortion.”
Instead of high-profile takedowns, this group targets smaller organizations with weak security postures, using common exploitation techniques like brute-force attacks, credential theft, and misconfiguration abuses.
In July 2024, Dragon RaaS launched its Telegram channel, followed by the announcement of the “Dragon Ransomware RaaS Platform” in October. The platform promised:
- Ultra-fast encryption
- A 50KB payload size
- A web-based control panel
- Distributed ransomware builder for customization
The group even gamified access, stating: “Once we reach 1k subscribers on the channel, it’ll be available for everyone!”
Dragon RaaS employs a two-pronged attack strategy: a PHP-based webshell and a Windows encryptor based on StormCry. The webshell offers file manipulation, encryption, and defacement capabilities all in one lightweight script.
Initial access is commonly gained via:
- WordPress plugin and theme vulnerabilities (e.g., Porto theme CVEs 2024-3806~3809)
- LiteSpeed HTTP server flaws (e.g., CVE-2022-0073, CVE-2024-47374)
- Vulnerable cPanel instances
SentinelOne notes, “Files encrypted via OpenSSL (AES-256 in CBC mode) are deleted and replaced with the fully encrypted version,” and appended with a “.dragon” extension.
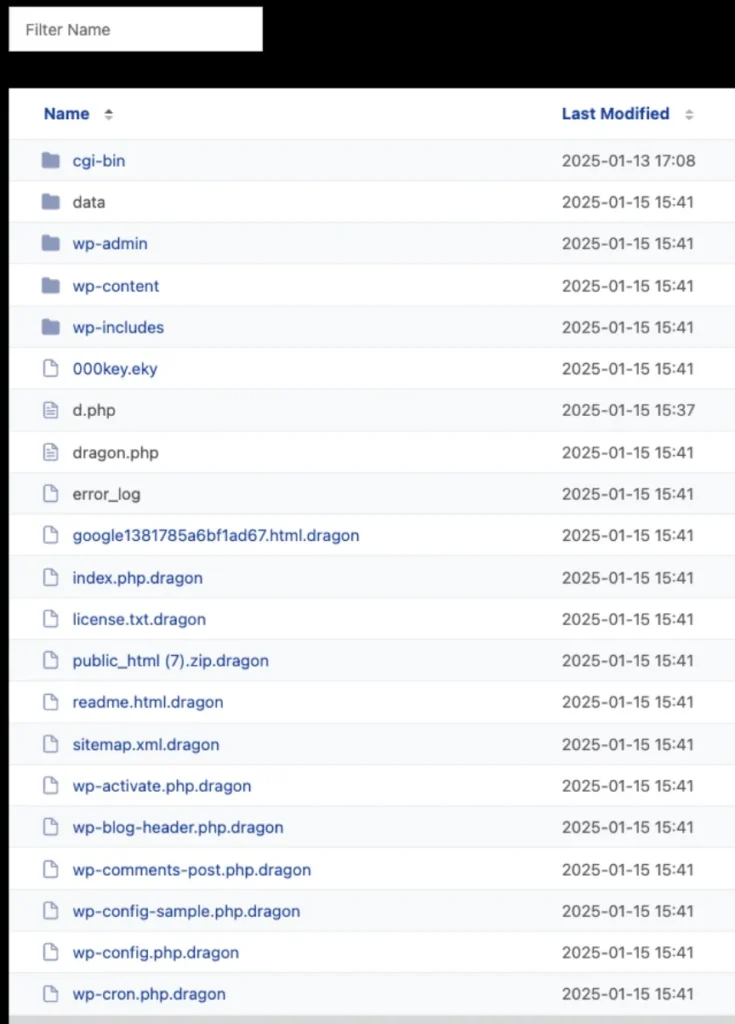
Despite their marketing, Dragon RaaS’s Windows encryptor is nearly identical to Stormous’s StormCry ransomware. SentinelOne states: “The Python source code for StormCry, and the analyzed source code for ‘Dragon Team’ are nearly identical.”
From the use of the same Bitcoin payment address to directing victims to the same Telegram bot, it’s clear that Dragon RaaS is more of a rebrand than a reinvention.
Dragon RaaS targets a wide geographic range, including the U.S., U.K., Israel, France, Yemen, and Ukraine. Many attacks are cataloged on Mirror-H, a popular defacement tracking site.
Although ransom notes typically demand $300 in Bitcoin, the real hallmark of Dragon RaaS is their aggressive defacement activities and social media presence. Victims often find their websites vandalized with the group’s logos and encrypted files ending in “.dragon.”
Dragon RaaS represents a hybrid threat model where hacktivism meets profit-driven ransomware. “The Dragon Ransom group’s defacement activities are more extensive than their ransomware attacks,” SentinelOne concludes, underscoring the group’s dual focus on visibility and extortion.