
A recent investigation by the Cleafy Threat Intelligence and Response (TIR) team has uncovered DroidBot, a sophisticated Android Remote Access Trojan (RAT) linked to a new Turkish Malware-as-a-Service (MaaS) operation. With advanced capabilities and an active campaign targeting banking institutions, cryptocurrency exchanges, and national organizations across Europe, DroidBot signals a significant escalation in mobile malware threats.
First detected in June 2024, DroidBot combines advanced features, including hidden VNC, overlay attacks, and spyware-like keylogging, making it a powerful tool for on-device fraud. It employs dual-channel communication, using MQTT for outbound data and HTTPS for inbound commands, ensuring flexibility and resilience.
“DroidBot is an advanced Android Remote Access Trojan (RAT)… with features often associated with spyware, enabling the interception of user interactions and credential theft,” the Cleafy report notes.
The malware currently targets 77 entities across countries such as the UK, Italy, France, Spain, and Portugal, with indications of expansion into Latin America. Cleafy highlights, “The combination of advanced surveillance features, dual-channel communication, a diverse target list, and an active MaaS infrastructure highlights DroidBot’s sophistication and adaptability.”
Unlike traditional malware campaigns, DroidBot operates as a Malware-as-a-Service (MaaS), enabling affiliates to access its capabilities through a subscription model. Each affiliate is assigned unique identifiers, and a Telegram channel advertises DroidBot’s features for a monthly fee of $3,000.
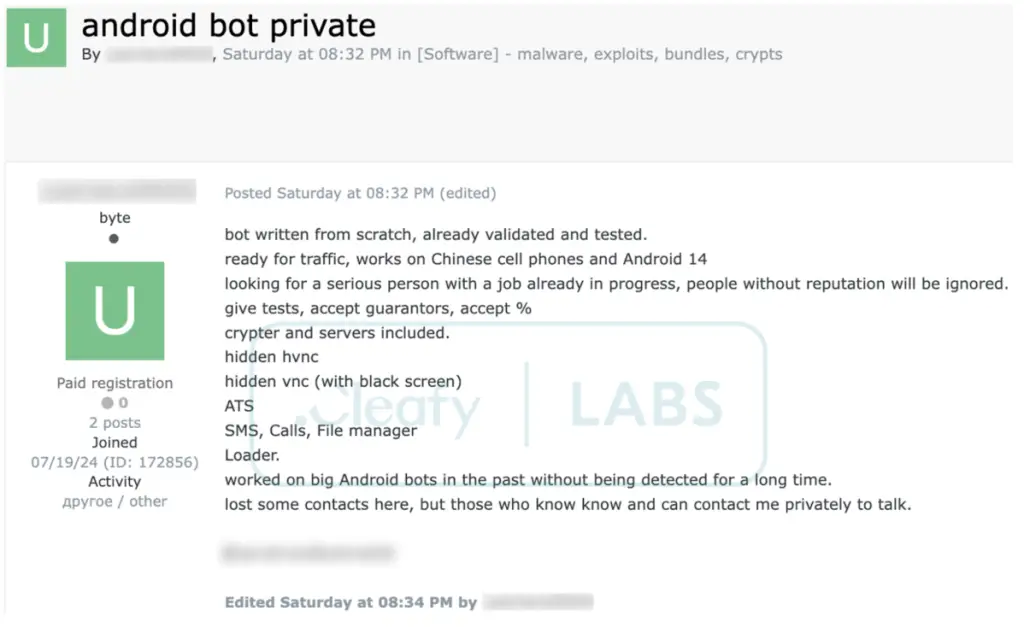
“DroidBot introduces a well-known but not widely spread paradigm in the mobile threat landscape,” Cleafy explains, emphasizing the scalability and reach offered by this approach.
DroidBot is distributed through social engineering tactics, disguised as legitimate security or banking apps. It abuses Android Accessibility Services to perform malicious actions, including:
- Keylogging: Capturing sensitive input such as login credentials.
- Overlay Attacks: Displaying fake login pages over legitimate apps to harvest credentials.
- VNC-Like Routines: Providing attackers with continuous screenshots of device activity.
- Remote Control: Enabling attackers to simulate user interactions and manipulate the device.
Notably, DroidBot leverages MQTT for its command-and-control (C2) infrastructure, a protocol typically used in IoT systems. This unconventional choice aids in evading detection and enhances operational resilience.
Cleafy’s analysis reveals that DroidBot is still under active development, with placeholder functions and varying levels of obfuscation across samples. Evidence such as debug strings and malware configurations suggests that its developers are Turkish speakers, with localization for English, Italian, Spanish, and Turkish users.
DroidBot poses a significant threat to financial institutions and high-value targets. Its operational model elevates the scale and complexity of monitoring and defending against such attacks. As Cleafy warns, “The real point of concern lies in this new model of distribution and affiliation, which would elevate the monitoring of the attack surface to a whole new level.”
Related Posts:
- Over 1,500 Devices Infected: Android Trojan ToxicPanda Targets Banks in Europe and Latin America
- Google Advanced Protection Program now supports iOS applications
- Beware of Fake Advanced IP Scanner: Malicious Installer Delivers CobaltStrike Backdoor